Introduction to using components with known vulnerabilities
Causes of loopholes
There are known security vulnerabilities in the frameworks, libraries and toolkits used in the application technology stack.
Attack mode
Exploit known vulnerabilities in frameworks, libraries, tools, etc. in the application technology stack to obtain high permissions or sensitive data.
Vulnerability impact
Sensitive data disclosure, privilege upgrading, remote code execution, etc. the specific impact depends on the exploitability of the vulnerability.
Vulnerability protection
1. Remove all unnecessary dependencies.
2. Understand and master the list of all components you use.
3. Monitor national information security vulnerability library cnnvd and general vulnerability library cve to find vulnerabilities in components.
4. Update and upgrade your components regularly.
5. Try not to use components that are not actively maintained.
Automatic inspection scheme
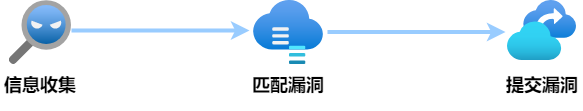
The development idea of automatic inspection is mainly divided into three parts:
1. Collection of components used by the system.
2. Match the components of the collection class with vulnerabilities in the vulnerability library.
3. Submit the matched vulnerabilities to the project team for modification.
The idea of each step is introduced below.
information gathering
This step is mainly to collect accurate component reference information as much as possible. The information should include the name of the component and the corresponding version number.
For example, the components that may be used in typical back-end applications are:;
1. Middleware: Nginx, Tomcat, Mq, Rides, etc
2. Databases: Oracle, Mysql, Postgresql, ClickHouse, InfluxDB, etc
3. Back end services: back end services generally refer to more third-party packages, which are also prone to vulnerabilities, such as Fastjson, Shiro and other components.
Collection method
1. Collection of middleware and database components
The middleware and database versions can be collected and maintained manually, or automatically identified by referring to fingerprint identification tools. However, in order to ensure accuracy, it is recommended to have full-time personnel in the project team for maintenance, such as testing or operation and maintenance personnel
2. Back end service reference component collection
For the three-party packages referenced by the back-end service, it is recommended to collect them by dependency file parsing, which is more efficient and accurate. Taking the java project managed by maven as an example, we can resolve their dependencies and parent dependencies according to the pom file, resolve these dependencies and store them according to the rules, which is the component resources we refer to. The following is the routine (this example is to analyze local services. If you need to analyze remote code, you can integrate jgit tools to analyze all items in git warehouse);
//Used to call and execute mvn instructions
<dependency>
<groupId>org.apache.maven.shared</groupId>
<artifactId>maven-invoker</artifactId>
<version>3.1.0</version>
</dependency>
// It is used to parse PomTree as Node
<dependency>
<groupId>org.whitesource</groupId>
<artifactId>maven-dependency-tree-parser</artifactId>
<version>1.0.5</version>
</dependency>
public class AnalysisPom {
public static void main(String[] args) throws FileNotFoundException, UnsupportedEncodingException,
ParseException, MavenInvocationException {
// Define pom path
String PomFile = "Yours pom Path/pom.xml";
// Define Maven path
String MavenHome = "Yours maven Path/apache-maven-3.8.1";
// Define the mvn instruction to execute
String MavenCommand = "dependency:tree -D outputFile=YoursPomTree.txt";
// The path of the dependency tree file that needs to be resolved as a Node object (i.e. YoursPomTree)
String PomTreeFile = "YoursPomTree.txt";
InvocationRequest request = new DefaultInvocationRequest();
// The path of the pom file to be parsed is not written. The default is to parse the pom file of the current project
request.setPomFile(new File(PomFile));
Invoker invoker = new DefaultInvoker();
// Your maven installation path
invoker.setMavenHome(new File(MavenHome));
// Enter the mvn instruction to be executed
request.setGoals(Collections.singletonList(MavenCommand));
// implement
invoker.execute(request);
//Resolve PomTree to Node
InputType type = InputType.TEXT;
Reader r = new BufferedReader(new InputStreamReader(new FileInputStream("tree.txt"), StandardCharsets.UTF_8));
Parser parser = type.newParser();
Node tree = parser.parse(r);
System.out.println(tree); //Here, you can continue to recursively process the Node and obtain all dependent pom coordinates. The routine does not do specific processing
}
}
3. Store all identified three-party components in the component warehouse in the project dimension
Matching vulnerability
The matching vulnerability link is mainly used to match the components collected in the link with the vulnerabilities in the vulnerability library. For example, fastjson-v1.2.62 is referenced in the three-party components, and the vulnerabilities related to fastjson-v1.2.62 also exist in the vulnerability library, so the vulnerability matching is completed. If fastjson-v1.2.62 is not found in the vulnerability library, we believe that this component is safe and there are no vulnerabilities. The specific matching methods are as follows: Lower;
Matching method
1. Collect vulnerabilities and maintain your own vulnerability warehouse
Since the Ministry of industry and information technology, the state Internet information office and the Ministry of Public Security jointly issued the regulations on the management of security vulnerabilities of network products in July this year, the discovery, report repair and release of future vulnerabilities are under the unified jurisdiction of national departments, so the collection suggestions of vulnerabilities focus on national professional websites. The recommendations are as follows;
1. National information security vulnerability database cnnvd: http://www.cnnvd.org.cn/
2. National information security vulnerability sharing platform cnvd: https://www.cnvd.org.cn/
3. Cstis, the network security threat and vulnerability information sharing platform of the Ministry of industry and information technology: https://www.cstis.cn/
4. General vulnerability library CVE maintained by Mitre: http://cve.mitre.org/
5. NVD maintained by NIST: https://nvd.nist.gov/
Because cnnvd and cve provide external data files with a high degree of professionalism, they can give priority to parsing the vulnerability data files provided by the two websites when doing vulnerability collection procedures, which can reduce a lot of investment.
2. Associate the keywords in the vulnerability Library (such as the components and versions involved in the vulnerability) with the components in the third-party component library
Submission vulnerability
Submit the vulnerable components to the corresponding team for rectification.