Catalog
I. DNS
1.1 Introduction to DNS Services
DNS (Domain Name System), a distributed database on the Internet that maps domain names and IP addresses to each other, enables users to access the Internet more easily without having to remember the IP strings that can be read directly by the machine. The process of getting the IP address corresponding to the host name through the host name is called domain name resolution (or host name resolution).
-
DNS protocol runs over UDP and TCP, using port 53
-
The UDP protocol is used when DNS parses queries, and the TCP protocol is used when the master-slave transfers the zone database files.
1.2 Internet Domain Name Structure
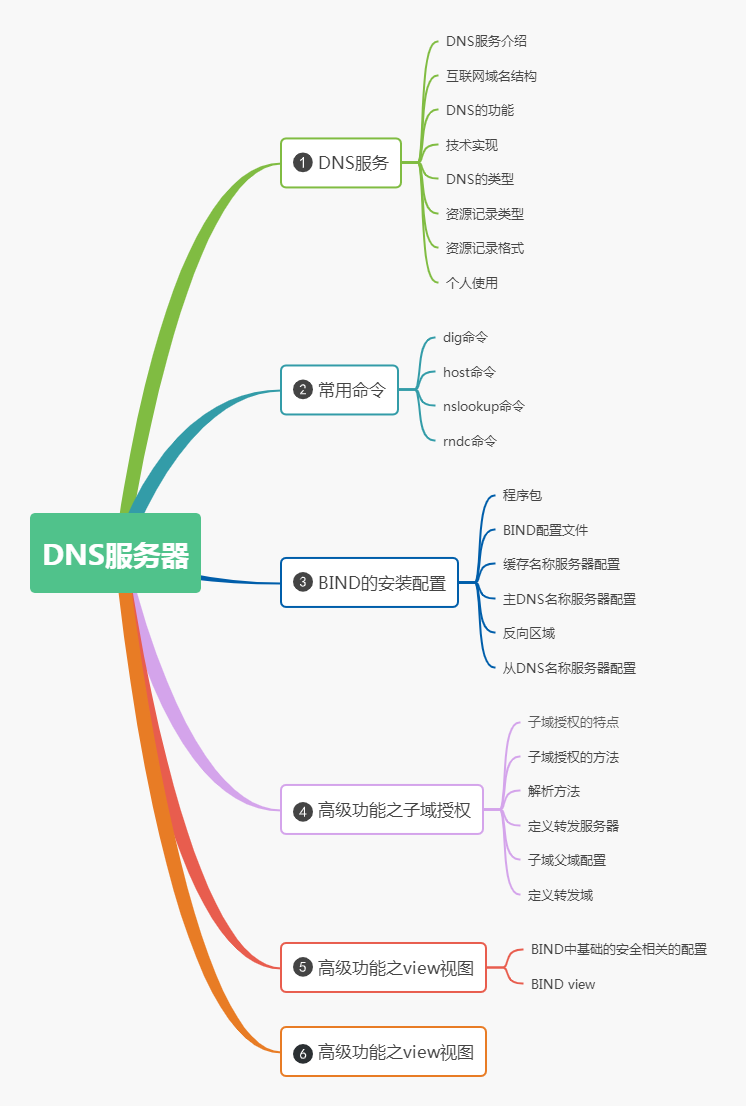
General structure
-
Host name. Secondary domain name. Top domain name. Root
-
www.wsescape.com.
management style
-
Top-level domain names on the Internet are registered and managed by the Internet Networking Association Domain Name Registration Query Committee responsible for network address assignment
-
It also assigns a unique IP address to each host on the Internet
Functions of 1.3 DNS
Each IP address can have a host name, which is composed of one or more strings separated by decimal points. With a host name, don't memorize the IP address of each IP device by heart, just remember the host name that is relatively intuitive and meaningful.
Two ways to map hostname to IP address
-
static mapping
/etc/hosts file
There is a host-to-IP mapping relationship on each device for this device only
-
Dynamic Mapping
/etc/resolv.conf file
Refers to the mapping relationship between hosts and IP configured through a DNS server
# cat /etc/hosts 127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 ::1 localhost localhost.localdomain localhost6 localhost6.localdomain6 # cat /etc/resolv.conf nameserver 172.16.242.2
Resolution - FQDN(Full Qualified Domain Name)
-
Forward==> FQDN --> IP
-
Reverse==> IP --> FQDN
-
authority
-
Non-authoritative
-
Parsing Order
When resolving a domain name, first use static domain name resolution, and then use dynamic domain name resolution if static domain name resolution is unsuccessful.
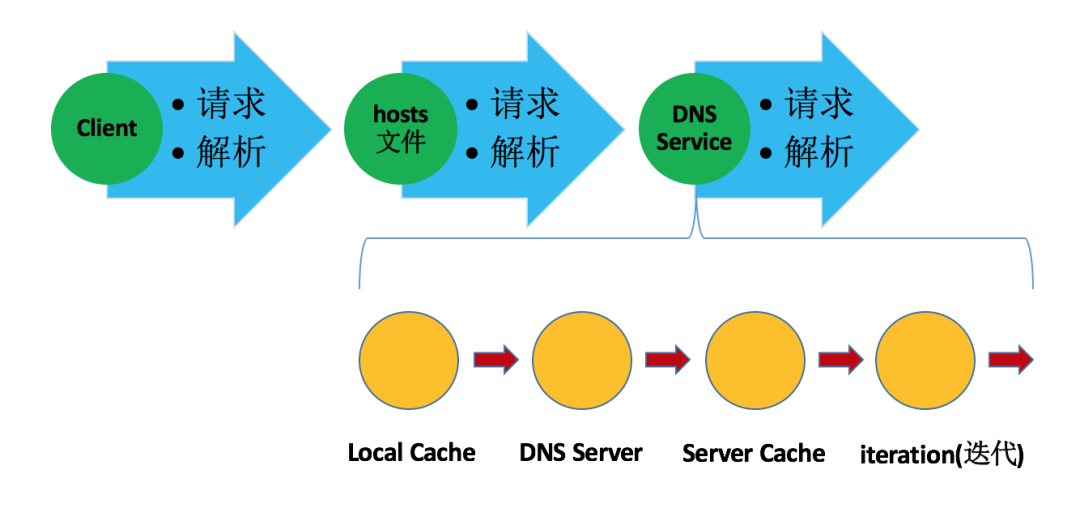
Process through which a complete query request passes
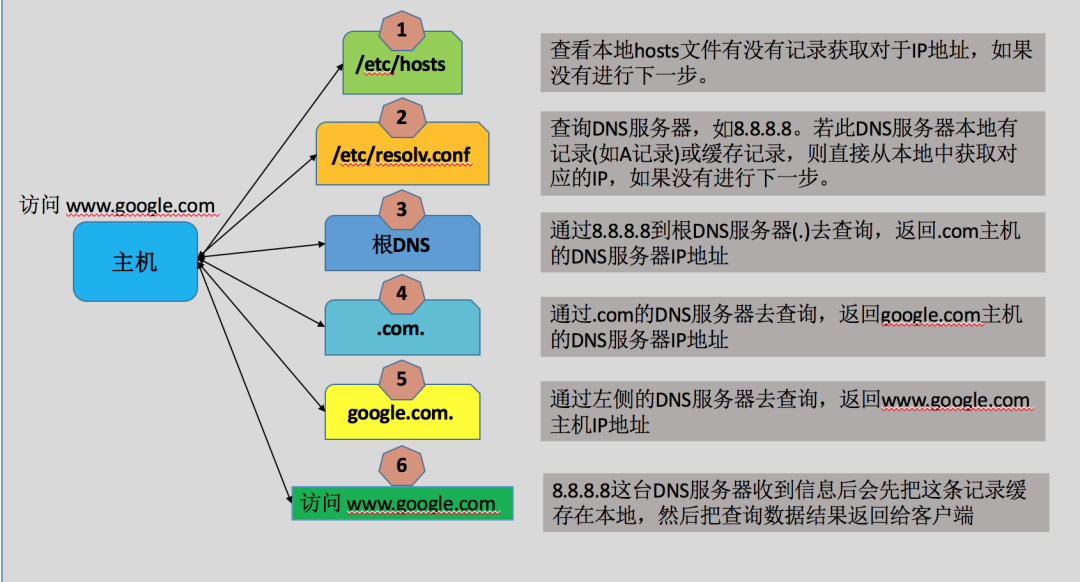
1.4 Technology Implementation
DNS implements a hierarchical namespace as a subdomain authorization mechanism by allowing a name server to delegate part of its name service, known as zone, to a subserver
-
DNS also provides additional information, such as system aliases, contact information, and which host is acting as a mail hub for a system group or domain
-
Any computer network using IP can use DNS to implement its own private name system
Software for implementing DNS
-
BIND
-
DJBDNS
-
MaraDNS
-
Name Server Daemon
-
PowerDNS
-
Dnsmasq
DNS Query Type
-
Iterative Query
-
recursive query
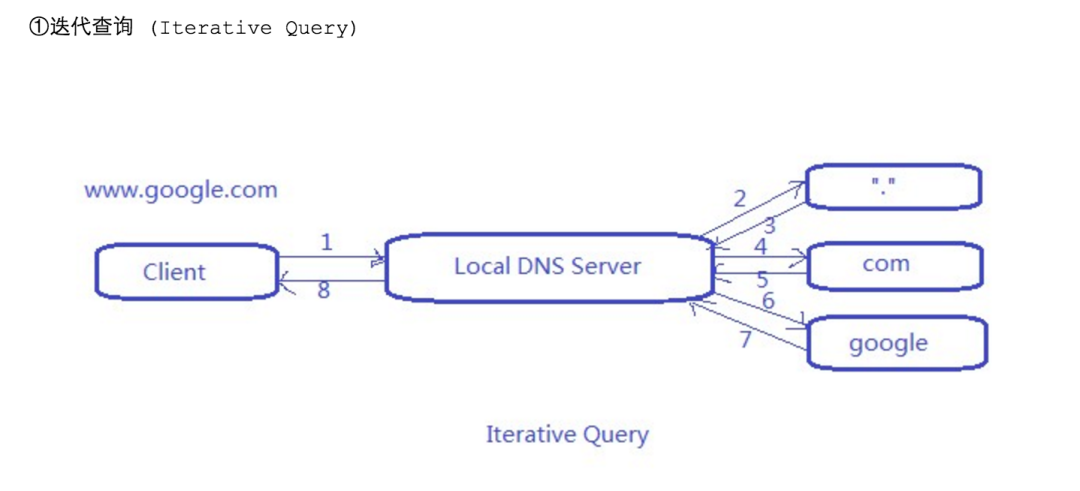
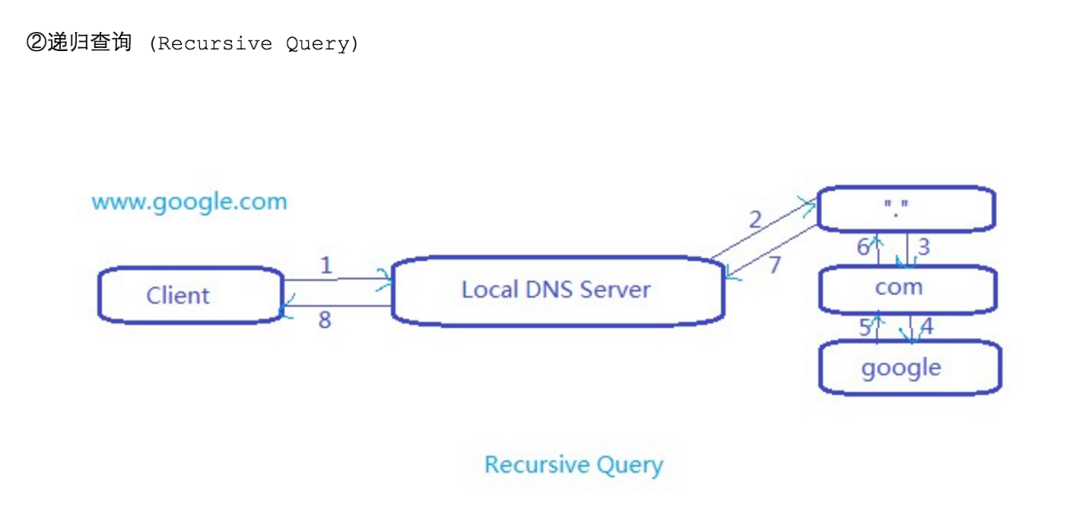
Types of 1.5 DNS
(1)Primary DNS Server(Master)
The master server of a domain holds the zone configuration file for that domain. All configuration and changes for that domain are made on that server. This article also explains how to configure the master DNS server for a domain.
(2)Secondary DNS Server(Slave)
Domain slave servers are generally used as redundant loads. A domain slave server grabs zone profiles from the primary server of the domain. No information changes are made from the server. Zone profile modifications can only be made on the primary DNS server. All modifications are synchronized by the primary server.
(3)Caching only Server(Cache)
DNS cache servers do not have any zone profiles and rely solely on caching to serve clients, which is often used for load balancing and accelerated access operations.
(4) Forwarding server
Forwarding only
Note Description
Primary DNS Server
-
Maintain intra-zone parsing library servers responsible for parsing
-
Parsing libraries are managed and maintained freely, either manually or automatically
-
Notification mechanism
-
Notify slave server of any changes to the primary DNS server resolution Library
From DNS Server
-
Copy (zone transfer) a resolution library from the master DNS server or another DNS server
-
Serial number: Represents the version number of the parsing library, provided that the content of the primary server parsing library changes and its sequence increases
-
Refresh time: The interval between requests from the server to synchronize the parse libraries from the master server
-
Retry time: The interval between retries when a request from the server to synchronize the resolution libraries fails
-
Length of expiration: How long before you give up from a server perspective and stop servicing when the primary server is never reached from the server
-
Area Transport
-
Full Transfer: Transfer the entire parse Library
-
Incremental Transfer: Transfer that part of the Parse Library change
1.6 Resource Record Type
Common resource record types in DNS systems:
Host Record (A Record)
-
FQDN --> IP
-
A record is an important record for name resolution, which maps a specific host name to the IP address of the corresponding host
Pointer record (PTR record)
-
IP --> FQDN
-
Boot to a Canonical Name, most commonly used to run reverse DNS lookups
Start of Authoritative Record (SOA Record)
-
A Zone Resolution Library has and can only have one SOA record and must be the first record of the Resolution Library
Name Server Record (NS Record)
-
A DNS server dedicated to identifying the current zone
Alias record (CNAME record)
-
CNAME records are used to point an alias to an A record so that you do not need to create another A record for a new name
MX Record (MX Record)
-
Guide a domain name to the list of Message Transfer Agents for that domain name
IPv6 Host Record (AAAA Record)
-
FQDN --> IP
-
Corresponds to an A record used to map a specific host name to the IPv6 address of a host.
Service Location Recording (SRV Recording)
-
Used to define the location of servers that provide specific services, such as host name, port
NAPTR Records
-
It provides regular expressions to map a domain name. A well-known application of NAPTR records is for ENUM queries.

1.7 Resource Recording Format
grammar
name [TTL] IN rr_type value
(1) TTL is cache length if omitted from global inheritance
(2)IN stands for Internet
(3)rr_type represents the resource record type
(4) @can be used to refer to the name of the current region
(5) Multiple different values can be defined by multiple records for the same name, in which case the DNS server will respond in a polling fashion
(6) The same value may have multiple different defining names, defined by multiple different names pointing to the same value, which only means that the same host can be found by multiple different names
SOA
Name: The name of the current region, such as wsescape.com.
value:has multiple components
-
(1) The FQDN of the primary DNS server of the current zone, or the name of the current zone.
-
(2) The mailbox address of the current regional administrator, but the @ sign cannot be used in the address, which is usually replaced by. e.g. linuxmail.wsescape.com
-
(3) Unified TTL for the definition of master-slave service coordination attributes and negative answers
#86400 is a TTL value in seconds #The primary DNS server address is ns.wsescape.com. #The mailbox address is nsadmin.wsescape.com. #First edition is 2016052201, identifying version number wsescape.com.86400INSOAns.nsadmin.wsescape.com.( 2016052201 ;serial number 2H ;Refresh time, 2 hours 10M;Retry time, 10 minutes 1W;Expiration time, one week 1D;Negative TTL Value, day )
NS
Name: The name of the current region
value: The name of a DNS server in the current zone, such as ns.wsescape.com.
Be careful
-
(1) When two adjacent resource records have the same name, subsequent omissions may be made
-
(2) For NS records, a server name following any NS record should have an A record following it
#A region can have multiple NS records #Both ns1.wsescape.com. and ns2.wsescape.com. should have a subsequent A record wsescape.com.INNS ns1.wsescape.com. wsescape.com.INNS ns2.wsescape.com.
MX
Name: The name of the current region
value: Host name of a mail server (smtp server) in the current zone
-
Within an area, MX records can have more than one
-
However, each record value should be preceded by a number (0-99) indicating the priority of this server
-
The smaller the number, the higher the priority
Be careful
-
(1) When two adjacent resource records have the same name, subsequent omissions may be made
-
(2) For MX records, any server name following an MX record should have an A record following it
#Both mx1.wsescape.com. and mx2.wsescape.com. should have a subsequent A record wsescape.com.IN MX 10 mx1.wsescape.com. INMX 20 mx2.wsescape.com.
A
name: The FQDN of a host, such as www.wsescape.com.
value: The host name corresponds to the IP address of the host;
Be careful
-
Avoid giving incorrect answers when users write incorrect names, and resolve to a specific address through universal domain name resolution
#Polling www.wsescape.com.IN A1.1.1.1 www.wsescape.com.IN A 1.1.1.2 #A host has more than one name mx1.wsescape.com.IN A 1.1.1.3 mx2.wsescape.com. IN A 1.1.1.3 #Avoid giving incorrect answers when users write incorrect names, and resolve to a specific address through universal domain name resolution *.wsescape.com.IN A 1.1.1.4 wsescape.com.IN A 1.1.1.4
AAAA
Similar to an A record, this simply represents an IPv6 address
#Polling www.wsescape.com.IN AAAA1.1.1.1 www.wsescape.com.IN AAAA 1.1.1.2 #A host has more than one name mx1.wsescape.com.IN AAAA 1.1.1.3 mx2.wsescape.com. IN AAAA 1.1.1.3 #Avoid giving incorrect answers when users write incorrect names, and resolve to a specific address through universal domain name resolution *.wsescape.com.IN AAAA 1.1.1.4 wsescape.com.IN AAAA 1.1.1.4
PTR
name:Name here denotes an IP address
IP address has a specific format, write IP address in reverse, if 1.2.3.4 need to write 4.3.2.1
There is also a specific suffix in-addr.arpa., written in 4.3.2.1.in-addra.arpa.
value: value here is FQDN
Be careful
-
Network address and suffix can be omitted, host address still needs to be written in reverse
#Examples 4.3.2.1.in-addr.arpa.INPTRwww.wsescape.com. #If 3.2.1 is abbreviated as a network address 4 IN PTRwww.wsescape.com. #If 2.1 is abbreviated as a network address 4.3 IN PTRwww.wsescape.com.
CNAME
name:FQDN of Alias
value: FQDN of the working name
web.escapelife.com.IN CNAME www.escapelife.com.
1.8 people use
Subdomain authorization is the name server for each domain, authorized in the resolution library through its parent name server
Similar root domain authorization tld
.com.INNS ns1.com. .com. IN NSns2.com. ns1.com.INA 2.2.2.1 ns2.com. INA2.2.2.2
Take wsescape.com for example
#wsescape.com. Add resource records to the parse library on the name server of.Com wsescape.com.INNSns1.wsescape.com. wsescape.com.INNSns2.wsescape.com. wsescape.com.INNSns3.wsescape.com. ns1.wsescape.com.INA 3.3.3.1 ns2.wsescape.com.INA 3.3.3.2 ns3.wsescape.com.INA 3.3.3.3
Domain name registration
-
Agent
-
Wanwan
-
New Network
-
godaddy
Binding Server
-
After the registration is complete, would you like to resolve it yourself with a dedicated service?
-
Manage background, server name to which NS records point and server address to which A records point
2.Common Commands
2.1 dig command
dig is used to test the dns system, so the hosts file will not be queried for resolution
-
Flexible tool for interrogating DNS domain name servers
-
dig will try any of the servers listed in /etc/resolv.conf unless told to request a specific domain name server
-
When no command line parameters or options are specified, dig will execute NS queries against. (root)
format
dig [-t type] name [@SERVER] [query options]
grammar
Type Query
dig -t NS wsescape.com @172.16.242.178 dig -t MX wsescape.com @172.16.242.178 dig -t A www.baidu.com
Query options:
+[no]trace: Track the parsing process +[no]recurse: Perform recursive resolution Test reverse resolution: dig -x IP @SERVER dig -x 172.16.100.11 @172.16.242.178
Analog Area Transfer:
dig -t axfr ZONE_NAME @SERVER dig -t axfr wsescape.com @172.16.242.178
2.2 host command
Tool for querying DNS with host command
-
It converts the host name of the specified host name to an IP address by often converting it
-
When no parameters are specified, it displays help information for the host command
format
host [-t type] name [SERVER]
grammar
-a equals-v-t
-C Finds SOA records on domain name servers that require authentication
-l Lists all hosts in a domain
-i reverse lookup
-r does not use recursive processing
-v Runtime displays detailed processing information
-4 Query for IPv 4
-6 Query for IPv 6
-t <type>Specify type, including a, all, mx, ns, etc.
Instance Display
[root@localhost ~]# host -t A www.wsescape.com 172.16.242.178 Using domain server: Name: 172.16.242.178 Address: 172.16.242.178#53 Aliases: www.wsescape.com has address 172.16.100.11 www.wsescape.com has address 172.16.100.12 [root@localhost ~]# host -t A www.wsescape.com 172.16.242.178 Using domain server: Name: 172.16.242.178 Address: 172.16.242.178#53 Aliases: www.wsescape.com has address 172.16.100.12 www.wsescape.com has address 172.16.100.11 [root@localhost ~]# host -t A www.wsescape.com 172.16.242.178 Using domain server: Name: 172.16.242.178 Address: 172.16.242.178#53 Aliases: www.wsescape.com has address 172.16.100.11 www.wsescape.com has address 172.16.100.12 [root@localhost ~]# host -t A www.wsescape.com 172.16.242.178 Using domain server: Name: 172.16.242.178 Address: 172.16.242.178#53 Aliases: www.wsescape.com has address 172.16.100.12 www.wsescape.com has address 172.16.100.11
2.3 nslookup command
The nslookup command is used to find a program for a domain name server. There are two modes: interactive and non-interactive
format
nslookup [-option] [name | -] [server]
grammar
-
Non-interactive mode
-
Just query directly
-
interactive mode
nslookup> server IP: Indicate which to use DNS server Query; set q=RR_TYPE: Indicates the resource record type of the query; NAME: Name to query;
Instance Display
[root@localhost ~]# nslookup > server 172.16.242.178 Default server: 172.16.242.178 Address: 172.16.242.178#53 > set q=A > www.wsescape.com Server:172.16.242.178 Address:172.16.242.178#53 Name:www.wsescape.com Address: 172.16.100.11 Name:www.wsescape.com Address: 172.16.100.12 > set q=NS > wsescape.com Server:172.16.242.178 Address:172.16.242.178#53 wsescape.comnameserver = ns2.wsescape.com. wsescape.comnameserver = ns1.wsescape.com. #Non-interactive mode query [root@rudder ~]# nslookup baidu.com Server: 8.8.8.8 Address: 8.8.8.8#53 Non-authoritative answer: Name: baidu.com Address: 123.125.114.144 Name: baidu.com Address: 220.181.111.85 Name: baidu.com Address: 220.181.111.86 #Non-interactive mode query [root@rudder ~]# nslookup > www.baidu.com Server:172.17.0.254 Address:172.17.0.254#53 Non-authoritative answer: #Non-authoritative answer indicating read in cache www.baidu.comcanonical name = www.a.shifen.com. Name:www.a.shifen.com Address: 61.135.169.105 #Return the first IP address Name:www.a.shifen.com Address: 61.135.169.125 #Return the second IP address > server 8.8.8.8 #Set Domain Name Server to 8.8.8.8 Default server: 8.8.8.8 Address: 8.8.8.8#53 > www.baidu.com #Request the IP address of Baidu again Server:8.8.8.8 Address:8.8.8.8#53 Non-authoritative answer: www.baidu.comcanonical name = www.a.shifen.com. Name:www.a.shifen.com Address: 220.181.111.147 #Different DNS acquires different IP addresses.
2.4 rndc command
The rndc client modifies the name of the server by establishing a socket to connect the server and listening on port 953 of TCP. However, due to security considerations, the rndc client and the server are installed on the same host.
Grammar 1
-
-b:source-address Using source-address as the source address to connect to the server allows multiple instances to set IPv4 and IPv6 source addresses
-
-c config-file: use config-file as an alternative to the default configuration file/etc/rndc.conf
-
-k key-file: Use the key-file as an alternative to the default key file/etc/rndc.key. If the config-file does not exist, /etc/rndc.key will be used to authenticate commands sent to the server
-
-s server: The name or address of the server that matches the server statement in the rndc configuration file. If the command line does not provide a server, the host named by the default-server clause in the options statement in the rndc configuration file is used
-
-p port: Send commands to TCP port to replace BIND 9's default control channel port 953
-
-V: Open redundant log
-
-y key_id: Use the key_id in the configuration file
Grammar 2
-
reload: overload master profile and region parse library files
-
reload zone: overloaded zone parsing library file
-
refresh zone: arrange immediate maintenance of the zone
-
retransfer zone: Manually start the zone transfer process regardless of whether the serial number is increased or not
-
notify zone: Re-issue notifications for zone transfers
-
reconfig: overload master profile
-
status: Write server statistics to the statistics file
-
querylog: Turn query logs on or off, and suggest opening them when debugging, otherwise they consume too much performance
-
Dump db: Dump the cache to a dump file (named_dump.db)
-
Stop: Save pending updates to the main file and stop the server
-
halt: Stop the server without saving pending updates
-
trace: increase the debug level one level and turn it on when debugging is recommended, otherwise the log consumes too much performance
-
trace level: change debug level
-
notrace: set debug level to 0
-
Flush: flush all caches on the server
-
Status: Displays the status of the server
-
Restart: restart the server
Instance Display
#The rndc tool helps us output system information [root@localhost ~]# rndc status version: 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6 CPUs found: 1 worker threads: 1 number of zones: 20 debug level: 0 xfers running: 0 xfers deferred: 0 soa queries in progress: 0 query logging is OFF recursive clients: 0/0/1000 tcp clients: 0/100 server is up and running #rndc does not restart loading area files [root@localhost ~]# rndc reload
3.BIND Installation Configuration
DNS service, package name bind, program name named.
3.1 Package
Just install bind, bind-libs, and bind-utils
-
bind: main package
-
bind-libs: Dependent library files, including 32-bit and 64-bit
-
bind-utils: Provides client tools such as dig, host, nslookup, and nsupdate
-
bind-chroot: Build do not install, easily intruded
-
The bind-chroot package is designed to improve security by creating a hard link under the / var/named/chroot/etc/ folder from the configuration file/etc/named.conf, etc. of the DNS service and logging in using the service account instead of the root user
-
Note that modifying the profile will modify / etc / below, which will automatically synchronize to the link file below chroot
bind-sdb
bind-dyndb-ldap
In both cases, parse library files are stored in different databases
3.2 BIND Profile
configuration file
-
Service startup script under CentOS6/etc/rc.d/init.d/named
-
Main profile/etc/named.conf, /etc/rndc.key, shared key file for rndc, providing authentication
-
What is rndc? The remote name controller, default and bind are installed on the same host and can only connect to the named process through the local loopback address 127.0.0.1, provide helpful management functions such as viewing parsing status, default work on port 953/tcp, /etc/named.rfc1912.zones, request comment documents
-
Parse library file/var/named/ZONE_NAME.ZONE, multiple parse library files/var/named/named.ca exist in/var/named/directory, point to root DNS This file does not require administrator changes, but system-owned/var/named/named.local, local subdomain resolution, reverse parse localhost to 127.0.0.1
-
Be careful
(1) A physical server can provide resolution for multiple zones at the same time
(2) You must have a root zone file that contains 13 node addresses in named.ca, generated by the dig command
(3) There should be two (and more if ipv6 is included) resolution libraries for localhost and local loopback addresses
#Under CentOS6 [root@localhost ~]# rpm -ql bind | less /etc/NetworkManager/dispatcher.d/13-named /etc/logrotate.d/named /etc/named /etc/named.conf /etc/named.iscdlv.key /etc/named.rfc1912.zones /etc/named.root.key /etc/portreserve/named /etc/rc.d/init.d/named /etc/rndc.conf /etc/rndc.key /etc/sysconfig/named /usr/lib64/bind /usr/sbin/arpaname ......
#@indicates the region name of the current region, defined in the main profile/etc/named.conf #TTL value is not written because macro $TTL 1D is defined and directly inherited #rname.invalid.Indicates the administrator's mailbox address #The latter defaults, such as NS, A, etc., because the former is inherited [root@localhost named]# cat /var/named/named.localhost $TTL 1D @IN SOA@ rname.invalid. ( 0; serial 1D; refresh 1H; retry 1W; expire 3H ); minimum NS@ A127.0.0.1 AAAA::1 [root@localhost named]# cat /var/named/named.loopback $TTL 1D @IN SOA@ rname.invalid. ( 0; serial 1D; refresh 1H; retry 1W; expire 3H ); minimum NS@ A127.0.0.1 AAAA::1 PTRlocalhost.
Main Profile
-
Global configuration: options {}
-
Log subsystem configuration: logging {}
-
Zone Definition: Define which zones this machine can parse, such as zone "ZONE_NAME" IN {}
-
Note: Any service program that expects it to be accessible by other hosts over the network should at least listen on an IP address that can communicate with an external host
[root@localhost ~]# cat /etc/named.conf
options {
listen-on port 53 { 127.0.0.1; };
listen-on-v6 port 53 { ::1; };
directory"/var/named";
dump-file"/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { localhost; };
recursion yes;
dnssec-enable yes;
dnssec-validation yes;
dnssec-lookaside auto;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.iscdlv.key";
managed-keys-directory "/var/named/dynamic";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
#localhost.localdomain is the name of the region, which is @
[root@localhost ~]# cat /etc/named.rfc1912.zones
zone "localhost.localdomain" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "localhost" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "1.0.0.127.in-addr.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "0.in-addr.arpa" IN {
type master;
file "named.empty";
allow-update { none; };
};
3.3 Cache Name Server Configuration
After installing bind, even if it's a cached name server, it only takes a little configuration to complete
-
Modify listen-on port 53
-
Modify allow-query
-
Modify recursion
(1) Installation
[root@localhost ~]#yum install bind
(2) Startup
[root@localhost ~]# service named start Generating /etc/rndc.key: [ OK ] Starting named: [ OK ]
(3) View
#For security, after installing bind, by default only listens locally and does not provide services outside
#Any service program that expects it to be accessible by other hosts over the network should at least listen on an `IP'address that can communicate with external hosts
#Edit the main profile
[root@localhost ~]# ss -tunlp | grep :53
udp UNCONN 0 0 127.0.0.1:53 *:* users:(("named",39822,512))
udp UNCONN 0 0 ::1:53 :::* users:(("named",39822,513))
tcp LISTEN 0 3 ::1:53 :::* users:(("named",39822,21))
tcp LISTEN 0 3 127.0.0.1:53 *:* users:(("named",39822,20))
(4) Modification
#Back up before making changes
#Comma has no content before it, defaults to the previous name, followed by copied content
[root@localhost ~]# cp /etc/named.conf{,.bak}
[root@localhost ~]# ll /etc/named*
-rw-r-----. 1 root named 984 11 month 20 2015 /etc/named.conf
-rw-r-----. 1 root root 984 6 month 20 21:53 /etc/named.conf.bak
#//Indicates a single line comment, comment ipv6
#/**/for multi-line comments
#The modification must be made with;Must end with spaces at both ends of {}, otherwise it is a syntax error
#directory is used to define the location where the zone parsing library files are stored
#Recommend turning off dnssec functionality
#Change dnssec-enable and dnssec-validation to no and comment on the key file
#If more than one address can be added, it cannot be omitted
#If listen-on port 53 is commented or deleted, the default is to listen on all
#Change the allow-query comment to allow-query {any;};
#Recursive recursion must be yes
[root@localhost ~]# vim /etc/named.conf
options {
listen-on port 53 { 172.16.242.178; 127.0.0.1; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
// allow-query { localhost; };
recursion yes;
dnssec-enable no;
dnssec-validation no;
/* Path to ISC DLV key */
// bindkeys-file "/etc/named.iscdlv.key";
// managed-keys-directory "/var/named/dynamic";
};
(5) Restart takes effect
#Configuration will not take effect until restarted
[root@localhost ~]# service named restart
Stopping named: . [ OK ]
Starting named: [ OK ]
[root@localhost ~]# ss -tunlp | grep :53
udp UNCONN 0 0 172.16.242.178:53 *:* users:(("named",40086,513))
udp UNCONN 0 0 127.0.0.1:53 *:* users:(("named",40086,512))
udp UNCONN 0 0 ::1:53 :::* users:(("named",40086,514))
tcp LISTEN 0 3 ::1:53 :::* users:(("named",40086,22))
tcp LISTEN 0 3 172.16.242.178:53 *:* users:(("named",40086,21))
tcp LISTEN 0 3 127.0.0.1:53 *:* users:(("named",40086,20))
3.4 Primary DNS Name Server Configuration
Primary DNS name server configuration is to add zone profile on top of caching DNS server
-
Add zone records in/etc/named.rfc1912.zones
-
Add zone file at/var/named/
(1) Define zones in the main profile
format
#Master denotes master DNS
#slave denotes from DNS
#hint represents root
#forward Forward
#file uses the path defined by the master profile directory
zone "ZONE_NAME" IN {
type {master|slave|hint|forward};
file "ZONE_NAME.zone";
};
Modify Configuration
#Define a domain name in the /etc/named.rfc1912.zones file
#named-checkconf is used to check for grammatical errors
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "wsescape.com" IN {
type master;
file "wsescape.com.zone";
};
[root@localhost ~]# named-checkconf
(2) Define region parsing library files
format
What appears: Macro Definition; Resource records;
Modify Configuration
#Here, $TTL defines the value of TTL, 86400 seconds, and 1D can be used instead #$ORIGIN is used to specify domain name endings such as ns and mx are defaults # named-checkzone #Two www's that poll when visiting #Generic Domain Name Resolves here*, indicating that nothing is wrong with the user's input #Or write as * IN. A. 172.16.100.11 because CNAME cannot enter an ip address [root@localhost ~]# cd /var/named/ [root@localhost named]# vim wsescape.com.zone $TTL 86400 $ORIGIN wsescape.com. @ IN SOA ns1.wsescape.com. admin.wsescape.com ( 2016042201 1H 5M 7D 1D ) IN NS ns1 IN NS ns2 IN MX 10 mx1 IN MX 20 mx2 ns1 IN A172.16.100.11 ns2 IN A172.16.100.12 mx1 IN A172.16.100.13 mx2 IN A172.16.100.14 www IN A172.16.100.11 www IN A172.16.100.12 ftp INCNAMEwww * IN CNAME www [root@localhost named]# named-checkzone "wsescape.com" /var/named/wsescape.com.zone zone wsescape.com/IN: loaded serial 2016042201 OK
change permission
#You can see that the process is running with a name #Where the owner of the /etc/named.conf file is root and the owner group is named #For security reasons, make permission changes to files you create [root@localhost named]# ps -aux | grep named named 40086 0.0 1.1 160072 11736 ? Ssl 22:07 0:00 /usr/sbin/named -u named root 40785 0.0 0.0 103324 864 pts/0 S+ 23:19 0:00 grep named [root@localhost named]# ll /etc/named.conf -rw-r-----. 1 root named 1004 6 month 20 22:23 /etc/named.conf [root@localhost named]# id named uid=25(named) gid=25(named) group=25(named) [root@localhost named]# ll Total dosage 32 drwxrwx---. 2 named named 4096 6 month 20 21:45 data drwxrwx---. 2 named named 4096 6 month 20 21:45 dynamic -rw-r-----. 1 root named 3171 1 month 11 22:12 named.ca -rw-r-----. 1 root named 152 12 month 15 2009 named.empty -rw-r-----. 1 root named 152 6 month 21 2007 named.localhost -rw-r-----. 1 root named 168 12 month 15 2009 named.loopback drwxrwx---. 2 named named 4096 5 month 11 07:07 slaves -rw-r--r--. 1 root root 408 6 month 20 22:53 wsescape.com.zone [root@localhost named]# chmod 640 wsescape.com.zone [root@localhost named]# chown :named wsescape.com.zone [root@localhost named]# ll Total dosage 32 drwxrwx---. 2 named named 4096 6 month 20 21:45 data drwxrwx---. 2 named named 4096 6 month 20 21:45 dynamic -rw-r-----. 1 root named 3171 1 month 11 22:12 named.ca -rw-r-----. 1 root named 152 12 month 15 2009 named.empty -rw-r-----. 1 root named 152 6 month 21 2007 named.localhost -rw-r-----. 1 root named 168 12 month 15 2009 named.loopback drwxrwx---. 2 named named 4096 5 month 11 07:07 slaves -rw-r-----. 1 root named 408 6 month 20 22:53 wsescape.com.zone
Restart takes effect
[root@localhost ~]# service named restart Stopping named: . [ OK ] Starting named: [ OK ] #Use the dig command to help us validate information #Because of previous configuration, polling is performed here [root@localhost ~]# dig -t A wsescape.com @172.16.242.178
3.5 Reverse Zone
Reverse and forward resolution are separate systems, so they can be deployed on different or the same machine.
-
A zone can have only one primary server, either forward or reverse
-
A primary server can have more than one slave server
Determine the network address based on the host address defined in the configuration file
-
If they are all hosts within 172.16.100, then the network address is 172.16.100.
-
There are many kinds of addresses, such as 172.16.100.12, 172.16.200.121, etc., so the network address is 172.16.
-
And so on
What is the reverse zone
-
The invariant part is used as the area name, and the variable part is used as the name when the resolution is implemented
format
-
Zone name: Reverse network address. in-addr.arpa.
-
For example, 172.16.100. ==>100.16.172.in-addr.arpa.
How to define the reverse zone
(1) Define areas
#file is also a relative path, /var/named/
#If there are multiple forward domains corresponding to the same network, the multiple domains will have the same name, so the network address here can be defined at will, such as "network address 1.zone", "network address 2.zone", etc.
#If there is only one reverse zone, you only need to write a reverse parsing library, so you can name it Network Address.zone
zone "ZONE_NAME" IN {
type {master|slave|forward};
file "network address.zone";
};
#Because 172.16.242.178 and our other servers (172.16.100.12/172.16.100.11), it can only be written as "16.172.in-addr.arpa" and "172.16.zone"
#Finally add the following
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "16.172.in-addr.arpa" IN {
type master;
file "172.16.zone";
};
(2) Zone parsing library files
-
Primary PTR record
-
MX and A and AAAA records are not required
#$TTL represents the TTL value of the macro definition #$ORIGIN Here is the name of the reverse zone #The reverse host name cannot be omitted #11 and 12 are automatically supplemented with 16.172.in-addr.arpa. #Alias records do not need to be inversed, so ftp does not write reverse resolution #Here you can use vim-o wsescape.com.zone 16.172.zone to edit both files at the same time [root@localhost ~]# cd /var/named/ [root@localhost named]# vim 100.16.zone $TTL 86400 $ORIGIN 16.172.in-addr.arpa. @IN SOAns1.wsescape.com. admin.wsescape.com. ( 2016042201 1H 5M 7D 1D ) IN NSns1.wsescape.com. IN NSns2.wsescape.com. 11.100IN PTRns1.wsescape.com. 11.100IN PTRwww.wsescape.com. 12.100IN PTRmx1.wsescape.com. 12.100IN PTRwww.wsescape.com. 13.100IN PTRmx2.wsescape.com.
#Reverse resolution can also be written without $ORIGIN [root@localhost named]# vim 100.16.zone $TTL 86400 @IN SOAns1.wsescape.com. admin.wsescape.com. ( 2016042201 1H 5M 7D 1D ) 16.172.in-addr.arpa.IN NSns1.wsescape.com. IN NSns2.wsescape.com. 11.100IN PTRns1.wsescape.com. 11.100IN PTRwww.wsescape.com. 12.100IN PTRmx1.wsescape.com. 12.100IN PTRwww.wsescape.com. 13.100IN PTRmx2.wsescape.com.
(3) Modify permissions and restart
[root@localhost named]# chmod 640 16.172.zone [root@localhost named]# chmod :named 16.172.zone #Grammar [root@localhost named]# named-checkconf [root@localhost named]# named-checkzone "16.172.inaddr-addr" 16.172.zone ok [root@localhost named]# service named reload #Detection [root@localhost named]# host -t PRT 172.16.100.12 172.16.242.178 [root@localhost named]# dig -x 172.16.100.12 @172.16.242.178
3.6 Configuration from DNS Name Server
Defining a slave DNS server is to modify the configuration based on the caching server
-
Add zone records in/etc/named.rfc1912.zones
Master-slave replication
(1) Should be a stand-alone name server
(2) There must be an NS record in the zone parsing library file of the master server pointing to the slave server
(3) From the server, only zones need to be defined, not parse library files; parse library files should be placed in the / var/named/slaves/directory
(4) The master server must allow zone transfer from the server
(5) Master-slave server time should be synchronized and can be done through ntp
(6) The version of the bind program should be consistent; otherwise, it should be from high to low
Method for defining slave regions
Forward slave server format
#Synchronize master server parse files from server in/var/named/slaves/
zone "ZONE_NAME" IN {
type slave;
masters { MASTER_IP; };
file "slaves/ZONE_NAME.zone";
};
Reverse slave server format
#Synchronize master server parse files from server in/var/named/slaves/
zone "Reverse_Net_Addr.in-addr.arpa" IN {
type master;
file "SOMEFILE.zone";
};
(1) Forward slave server instance
#Note that from the DNS server here, NS records need to be defined in the master DNS server
#This will notify synchronization from the DNS server when the resolution Library of the master DNS changes, otherwise it will not be synchronized
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "wsescape.com" IN {
type slave;
masters { 172.16.242.178; };
file "slaves/wsescape.com.zone";
};
#Re-start the service to be effective
[root@localhost ~]# rndc reload
#Viewable through log
[root@localhost ~]# tail /var/log/messages
(2) Reverse slave server instance
#Note that from the DNS server here, NS records need to be defined in the master DNS server
#This will notify synchronization from the DNS server when the resolution Library of the master DNS changes, otherwise it will not be synchronized
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "16.172.in-addr.arpa" IN {
type slave;
masters { 172.16.242.178; };
file "slaves/172.16.zone";
};
#Re-start the service to be effective
[root@localhost ~]# rndc reload
#Viewable through log
[root@localhost ~]# tail /var/log/messages
4.Subdomain Authorization for Advanced Features
Features of 4.1 Subdomain Authorization
Subdomain authorization is actually a situation where you subdivide your domain name. For example, if you have registered the domain name wsescap.com, you need to use your own DNS server separately for the ops department and the fin department, because of business relations, etc. Then you need to subdomain authorization.
Characteristic
-
Distributed database
-
Subdomain authorization for forward resolution zones is common, while reverse authorization is relatively difficult
4.2 Subdomain Authorization Method
Forward Resolution Region Subdomain Method
#Define a subregion #Configure in the specified file under / var/named/ such as / var/named/wsescape.com.zone here #Under our authorization of wsescape.com, two subdomains are defined, ops and fin ops.wsescape.com.INNSns1.ops.wsescape.com. ops.wsescape.com.INNSns2.ops.wsescape.com. ns1.ops.wsescape.com.INA1.1.1.1 ns2.ops.wsescape.com.INA1.1.1.2 fin.wsescape.com.INNSns1.fin.wsescape.com. fin.wsescape.com.INNSns2.fin.wsescape.com. ns1.fin.wsescape.com.INA3.1.1.1 ns2.fin.wsescape.com.INA3.1.1.2
4.3 Resolution
Prerequisite: If under wsescape.com, a subdomain is defined as ops, and a WW service is created under ops.
External Resolution
(1) When a host in www.test.org needs to access the WW host under ops, the following stages need to be advanced:
-
First find the root (.), root says you go to com
-
Find com again, com says you're going to wsescape
-
Find wsescape again, wsescape says you're looking for ops
-
Last ops returns the required information
Internal Resolution
(1) When a host under wsescape.com needs to access the www host under ops, although the DNS host of wsescape.com is not resolved, it knows the location of the subdomain and will immediately point to the DNS server of the ops.
(2) When a host under ops needs access to a WW host under wsescape.com, the following stages need to be advanced:
-
Find ops first, ops says you find root
-
Find another root (.), root says you go to com
-
Find com again, com says you're going to wsescape
-
Finally wsescape returns the required information
We'll find this looping, so to avoid this problem, you need to define a forwarding server.
4.4 Define a forwarding server
Be careful
(1) Turn off dnssec functionality
-
dnssec-enable no
-
dnssec-validation no
(2) The forwarded server needs to be able to recurse for the requester, otherwise the forwarding request will not proceed
(3) that is, Global Forwarding is defined with defined zone forwarding, with priority that can be accurately matched first by zone forwarding and no more by global forwarding.
Forwarding mode
(1) Global Forwarding
All requests to non-native regions responsible for resolution are forwarded to the specified server
#forward defines forwarding mode
#first means forwarding to the specified resolution server before finding the root server if there is no response, i.e. recursively in iteration
#Only means gold is forwarded to the specified resolution server, only recursively
#fowwarders define who to forward
Options {
forward { first|only };
forwarders;
}
(2) Regional forwarding
Forward requests to a server for a specific zone only, need to define your own zone and zone type, etc.
#forward defines forwarding mode
#first means forwarding to the specified resolution server before finding the root server if there is no response, i.e. recursively in iteration
#Only means gold is forwarded to the specified resolution server, only recursively
#fowwarders define who to forward
zone "ZONE_NAME" IN {
type forward;
forward { first|only };
forwarders;
}
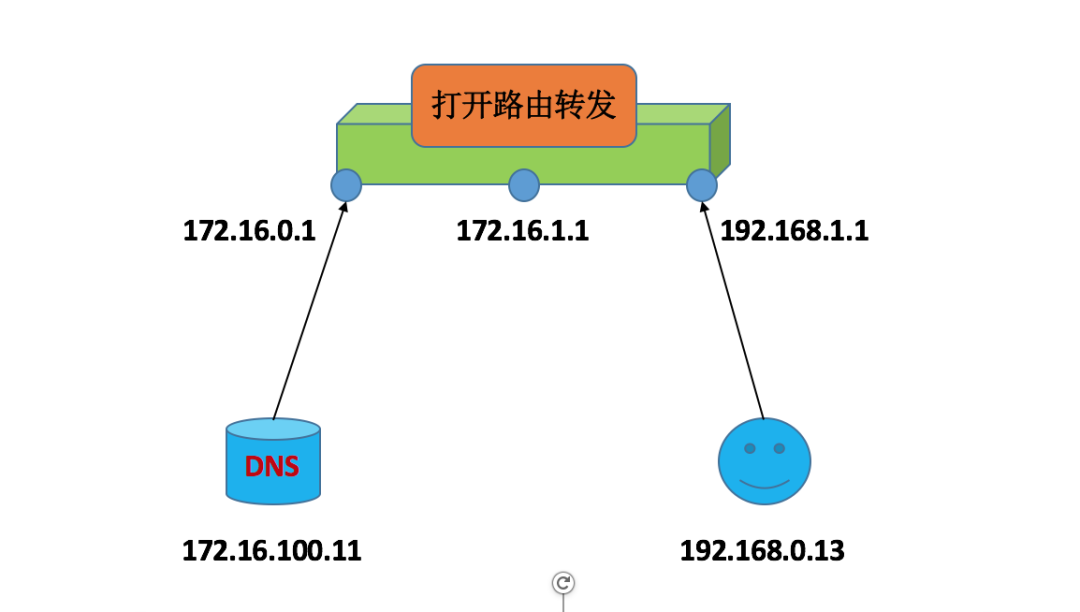
4.5 Child Domain Parent Domain Configuration
Prerequisite:
Parent domain IP address==> 172.16.100.11
Subdomain IP address==> 172.16.100.12
IP Address with Internet Access==> 172.16.0.1
(1) Parent Domain Server Configuration
#A separate host, where configuring the parent domain is based on the master server configuration, adding subdomains #Note, default listens on all #If the test fails, change the dnssec in view/etc/named.conf to no instead of commenting it out, otherwise the local client will not accept it
[root@localhost ~]# yum installl -y bind
[root@localhost ~]# vim /etc/named.conf
options {
// listen-on port 53 { 172.16.242.178; 127.0.0.1; };
// listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
// allow-query { localhost; };
recursion yes;
dnssec-enable no;
dnssec-validation no;
/* Path to ISC DLV key */
// bindkeys-file "/etc/named.iscdlv.key";
// managed-keys-directory "/var/named/dynamic";
};
[root@localhost ~]# service named start [root@localhost ~]# ss -tunl | grep :53 udp UNCONN 0 0 127.0.0.1:53 *:* udp UNCONN 0 0 ::1:53 :::* tcp LISTEN 0 3 ::1:53 :::* tcp LISTEN 0 3 127.0.0.1:53 *:*
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "wsescape.com" IN {
type master;
file "wsescape.com.zone";
};
#Ops, ns2.ops, and ns1.ops will automatically complete wsescape.com. #The A record for ns2.ops is not defined here because ns2.ops does not have a host configured #If the parent domain needs to find a child domain, it may run to our unconfigured machine, causing service resolution, so this is why there is no definition [root@localhost ~]# vim /var/named/wsescape.com.zone $TTL 1D $ORIGIN wsescape.com. @ IN SOA ns1.wsescape.com. admin.wsescape.com ( 2016042201 1H 5M 7D 1D ) IN NS ns1 IN NS ns2 ns1 IN A 172.16.100.11 ns2 IN A 172.16.100.18 www IN A 172.16.100.11 * IN A 172.16.100.11 ops IN NS ns1.ops ops IN NS ns2.ops ns1.ops IN A 172.16.100.12
[root@localhost ~]# cd /var/named/ [root@localhost named]# chown :named wsescape.com.zone [root@localhost named]# chmod 640 wsescape.com.zone [root@localhost ~]# rndc reload server reload successful [root@localhost ~]# tail /var/log/messages
(2) Subdomain server configuration
#Configuring a subdomain server, a separate host, is no different from the parent domain configuration #Note, default listens on all #If the test fails, change the dnssec in view/etc/named.conf to no instead of commenting it out, otherwise the local client will not accept it
[root@localhost ~]# yum installl -y bind
[root@localhost ~]# vim /etc/named.conf
options {
// listen-on port 53 { 172.16.242.178; 127.0.0.1; };
// listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
// allow-query { localhost; };
recursion yes;
dnssec-enable no;
dnssec-validation no;
/* Path to ISC DLV key */
// bindkeys-file "/etc/named.iscdlv.key";
// managed-keys-directory "/var/named/dynamic";
};
[root@localhost ~]# service named start [root@localhost ~]# ss -tunl | grep :53 udp UNCONN 0 0 127.0.0.1:53 *:* udp UNCONN 0 0 ::1:53 :::* tcp LISTEN 0 3 ::1:53 :::* tcp LISTEN 0 3 127.0.0.1:53 *:*
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "ops.wsescape.com" IN {
type master;
file "ops.wsescape.com.zone";
};
#Both ns1 and ns2 automatically complete ops.wsescape.com. #The definition of ns2 is also omitted because there is no machine here, if the parent domain needs to find a child domain #Possibly running to our unconfigured machine causing service resolution, so that's why it's undefined [root@localhost ~]# vim /var/named/ops.wsescape.com.zone $TTL 1D $ORIGIN ops.wsescape.com. @ IN SOA ns1.ops.wsescape.com. admin.ops.wsescape.com ( 2016042201 1H 5M 7D 1D ) IN NS ns1 IN NS ns2 ns1 IN A 172.16.100.12 www IN A 172.16.100.20 * IN A 172.16.100.20
[root@localhost ~]# cd /var/named/ [root@localhost named]# chown :named wsescape.com.zone [root@localhost named]# chmod 640 wsescape.com.zone [root@localhost ~]# rndc reload server reload successful [root@localhost ~]# tail /var/log/messages
(3) Test Configuration
#When we are here, we will find the following problems #In a subdomain server, you can view ops information after executing a command #172.16.100.12 is a subdomain server [root@localhost ~]# dig -t A www.ops.wsescape.com @172.16.100.12 #In a subdomain server, the information of the parent domain cannot be viewed when there is no network after the command is executed. In the case of a network, the information returned by the root is used to locate the parent domain information. [root@localhost ~]# dig -t A www.wsescape.com @172.16.100.12 #In the parent domain server, you can view information about the subdomain ops after executing the command #The dig command does a recursive operation by default, so you need to add + norecurse to it #172.16.100.11 is the parent domain server [root@localhost ~]# dig -t A ops.wsescape.com @172.16.100.11 +norecurse [root@localhost ~]# dig -t A www.ops.wsescape.com @172.16.100.11 +norecurse
4.6 Define forwarding domains
Be careful
-
If the test is found to be unsuccessful, change the dnssec in view/etc/named.conf to no instead of commenting it out, otherwise the local client will not accept it
-
If the test should be unresolved but still parsed, you may need to empty the cache rndc flush
Service Configuration
(1) Global Forwarding
#Configure in parent domain
#Global forwarding, that is, pass forwarding to 172.16.0.1 for query
#Edit/etc/named.conf on the parent domain server and add the following information on options
#Because the above machines are not connected to the Internet, they can be resolved by 172.16.0.1
[root@localhost ~]# vim /etc/named.conf
Options {
forward first;
forwarders { 172.16.0.1; };
}
[root@localhost ~]# rndc reload
server reload successful
[root@localhost ~]# tail /val/log/messages
#The tests in the parent domain can
[root@localhost ~]# dig -t A www.baidu.com @172.16.100.11
(2) Regional forwarding
#Configuring in subdomains
#Zone forwarding refers to forwarding queries in the wsescape.com domain to 172.16.100.11 for queries
#Edit/etc/named.rfc1912.zones on a subdomain server and add one last zone
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "wsescape.com" IN {
type forword;
forward only;
forwarders { 172.16.100.11; };
};
[root@localhost ~]# rndc reload
server reload successful
[root@localhost ~]# tail /val/log/messages
#Subdomain test OK, successful
[root@localhost ~]# dig -t A www.wsescape.com @172.16.100.12
(3) Test Configuration
#Test in parent domain, successful [root@localhost ~]# dig -t A www.ops.wsescape.com @172.16.100.11 [root@localhost ~]# dig -t A www.baidu.com @172.16.100.11 #Test in subdomain, subdomain knows where parent domain is and succeeds #In the subdomain, it is still unresolved because the definition area wsescape.com is specified to resolve #If, in a subdomain, a global forwarding is defined with a defined zone forwarding, the priority is that the precisely matched zone forwarding is done first, and Global Forwarding is no longer possible [root@localhost ~]# dig -t A www.wsescape.com @172.16.100.12 #Subdomain resolution failed [root@localhost ~]# dig -t A www.baidu.com @172.16.100.12
5.View view of advanced features
5.1 Basic security-related configuration in BIND
(1) acl mechanism
-
Merge one or more addresses into a set and call them with a uniform name
-
Can only be defined before used, generally defined in front of options in the configuration file
(2) acl format
#Acl for keyword and acl_name for custom name
#IP denotes a single IP address, net denotes a network, meaning that both a single IP and a network can be defined
acl acl_name {
ip;
ip;
net/prelen;
};
(3) Four built-in ACLS
Because these four are built-in acl s, we cannot use these names when we define them ourselves, otherwise misuse will occur.
-
None ==>There is no host
-
Any ==>any host
-
Local ==>Native
-
Localnet ==>Network address of local IP after operation with mask
(4) Access control instructions
The following directives can be used in/etc/named.conf to indicate global validity or in/etc/named.rfc1912.zones to indicate local validity in a separate zone. At the same time, {} can contain defined ACLS or host IP addresses, both built-in and self-defined.
-
Allow-query {} ==> host that allows queries, whitelist
-
Allow-transfer {} ==>Host that allows zone transfer, whitelist
-
Allow-recursion {} ==>Host that allows recursion
-
Allow-update {} ==>Allow updates to the contents of the regional database, recommended set to none
(5) Demonstration examples
#The acl we defined here can be used in the option in the main configuration file/etc/named.conf and in `/etc/named.rfc1912.zones`
#Define your own acl
acl mynet {
172.16.1.100;
172.16.0.0/16;
}
#Use in option in/etc/named.conf
[root@localhost ~]# vim /etc/named.conf
acl mynet {
172.16.1.100;
172.16.0.0/16;
}
options {
// listen-on port 53 { 172.16.242.178; 127.0.0.1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { mynet; };
recursion yes;
dnssec-enable no;
dnssec-validation no;
};
...
#Use in `/etc/named.rfc1912.zones`
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "wsescape.com" IN {
type master;
file "wsescape.com.zone";
allow-query { mynet; };
};
...
5.2 BIND view
Purpose: Mainly applicable to the classification of users, to improve the efficiency of site access.
-
If you visit the website by specifying different ways of accessing it on both internal and external networks
-
For example, depending on the type of operator, different users access the specified server to access the website
-
In fact, BIND view implements distributed caching, similar to the way CDN always works
Parsing process
-
When a user requests reception, first determine the source of the user, then match each view's own user section series table from top to bottom to determine the view system resolution function and return to the specified region resolution library file
-
Generally, the first network is matched with view1, the second network with view2, and the remaining networks with view3, so as to ensure that there are no omissions
(1) View
-
A bind server can define multiple views, and each view can define one or more zone s
-
Each view matches a set of requests to the client
-
Multiple view s may need to parse the same region, but use different regions to parse library files
(2) Format
-
view is top-down, matching one by one
-
Most of the instructions used in the option can be used in the view
view VIEW_NAME {
match-clients { };
}
(3) Attention
-
(1) Once view is enabled, all zone s can only be defined in view, with no exceptions allowed
-
(2) It is only necessary to define the root region in the view that matches the customer's view that allows recursive requests
-
(3) Client requests arrive by checking the list of clients served by each view top-down
(4) Experimental demonstration
Users from the 172.16 network who access www.wsescape.com use the 172.16.100.11 DNS server to specify the address of the WW server
Users who are not from the 172.16 network and have access to www.wsescape.com will use the public network 2.2.2.1 DNS server to specify the address of the WW server
#In 172.16.100.11 Host
#Define acl and delete root zone defined in/etc/named.conf
[root@localhost ~]# vim /etc/named.conf
#Delete the following root zone
zone "." IN {
type hint;
file "named.ca";
};
#Add acl
acl mynet {
172.16.0.0/16;
127.0.0.0/8;
};
#In 172.16.100.11 Host
#Move the root to/etc/named.rfc1912.zones and include all zones in the view
#And add internal access configuration internal
[root@localhost ~]# vim /etc/named.rfc1912.zones
#Add view s to restrict mynet access and allow recursion
view internal {
match-chlients { mynet; };
allow-recursion { mynet; };
#Add Root
zone "." IN {
type hint;
file "named.ca";
};
#Because of previous settings, here is wsescape.com and the wsescape.com.zone file is configured
zone "wsescape.com" IN {
type master;
file "wsescape.com.zone";
}
...
};
#In 172.16.100.11 Host #If we add 192.168.0.0/24 network in/etc/named.conf, it will be resolvable in 192.168.0.13, which is not added here [root@localhost ~]# named-checkconf [root@localhost ~]# service named restart #Success on 172.16.100.11 host [root@localhost ~]# dig -t A www.wsescape.com @172.16.100.11 #If configured, on host 192.168.0.13, succeeded [root@localhost ~]# dig -t A www.wsescape.com @172.16.100.11
#In 172.16.100.11 Host
#Add external access configuration in/etc/named.rfc1912.zones
#There is no recursion for hosts that do not match, so no root domain is added in external
[root@localhost ~]# vim /etc/named.rfc1912.zones
view external {
match-clents { any; };
zone "wsescape.com" IN {
type master;
file "wsescape.com.external";
allow-update { none; };
};
};
[root@localhost ~]# cd /var/named/
#Archive Copy
[root@localhost named]# cp -a wsescape.com.zone wsescape.com.external
#2.2.2.1 here represents the public network DNS server for the wsescape.com website
[root@localhost named]# vim wsescape.com.external
$TTL 1D
$ORIGIN wsescape.com.
@ IN SOA ns1.wsescape.com. admin.wsescape.com (
2016042201
1H
5M
7D
1D )
IN NS ns1
IN NS ns2
ns1 IN A 172.16.100.11
ns2 IN A 172.16.100.18
www IN A 2.2.2.1
* IN A 2.2.2.1
[root@localhost ~]# service named restart
#Success on 172.16.100.11 host from 172.16.100.11 [root@localhost ~]# dig -t A www.wsescape.com @172.16.100.11 #Success on host 192.168.0.13 from 2.2.2.1 [root@localhost ~]# dig -t A www.wsescape.com @172.16.100.1
6.Compile Install BIND for Advanced Features
#Minimize installation machine [root@localhost ~]# yum groupinstall "Development Tools" "Server Platform Development"
#Go to the website isc.org to download the installation package, bind-9.10.1-P1.tar.gz #The bind9 and bind10 are very different, and the bind10 is still in beta #Create named Users and Groups #Install in the same directory/usr/local/bind9, system files in/etc/named/ #Disable IPv6 functionality, disable chroot functionality, start multi-core threading #Compile and install bind s manually by yourself #(1) In/etc/named/no profile or empty, you need to create your own #(2) There is no zone parsing library file, i.e. /var/named, so there are no 13 root nodes to create. #(3) no rndc configuration file, you need to create your own #(4) No startup script, no / etc/init.d/name file #Because custom is installed in/usr/local/bind9, tools like dig, host, etc. cannot be called directly and require a full path
[root@localhost ~]# tar xf bind-9.10.1-P1.tar.gz [root@localhost ~]# cd bind-9.10.1-P1 [root@localhost ~]# groupadd -r -g 53 named [root@localhost ~]# useradd -r -u 53 -g 53 named [root@localhost ~]# ./configure --prefix=/usr/local/bind9 --sysconfdir=/etc/named/ --disable-ipv6 --disable-chroot --enable-threads [root@localhost ~]# make [root@localhost ~]# make install
#Add environment variables and you can call related commands [root@localhost ~]# vim /etc/profile.d/named.sh export PATH=/usr/local/bind9/bin:/usr/local/bind9/sbin:$PATH [root@localhost ~]# . /etc/profile.d/named.sh #Export library files [root@localhost ~]# vim /etc/ld.so.conf.d/named.conf /usr/loacl/bind9/lib #Reload library file [root@localhost ~]# ldconfig -v #If there is a header file, export the header file [root@localhost ~]# ln -sv /usr/local/bind9/include /usr/include/named #You can then use/usr/include/name to access the header file in/usr/local/bind9/ [root@localhost ~]# ls /usr/include/named #Add MANPATH to put share's help file under/usr/local/bind9/ [root@localhost ~]# vim /etc/man.conf MANPATH /usr/local/bind9/share/man
#Add master profile, just add directory here
[root@localhost ~]# vim /etc/named/named.conf
option {
directory "/var/named"
};
zone "." IN {
type hint;
file "named.ca";
};
zone "localhost" IN {
type master;
file "localhost.zone";
allow-update { none; };
};
zone "0.0.127.in-addr.arpa" IN {
type master;
file "named.local";
allow-update { none; };
};
[root@localhost ~]# mkdir /var/named/{named.ca, localhost.zone, named.local}
#Use the dig command to generate 13 root nodes, 172.16.0.1 being the gateway address, to help us connect to the address of the external network and get 13 root nodes [root@localhost ~]# dig -t NS . @172.16.0.1 > /var/named/named.ca [root@localhost ~]# vim /var/named/localhost.zone $TTL 1D @ IN SOA localhost. admin.localhost. ( 2016042201 1H 5M 7D 1D ) IN NS localhost. localhost. IN A 172.0.0.1 [root@localhost ~]# vim /var/named/named.local $TTL 1D @ IN SOA localhost. admin.localhost. ( 2016042201 1H 5M 7D 1D ) IN NS localhost. 1 IN PRT localhost. [root@localhost ~]# cd /var/named/ [root@localhost named]# chmod 640 ./* [root@localhost named]# chown :named * [root@localhost named]# chmod 640 /etc/named/named.conf
#View Help Documentation [root@localhost ~]# man named #Start named service, debug [root@localhost ~]# named -u named -f -g -d 3 #Start the name service without debugging [root@localhost ~]# named -u named #Check whether to start [root@localhost ~]# ss -tunl named | grep :53 #Close the name service [root@localhost ~]# killall named
#Add parsing area
[root@localhost ~]# vim /etc/named/named.conf
zone "wsescape.com" IN {
type master;
file "wsescape.com.zone";
allow-update { none; };
};
[root@localhost ~]# vim /var/named/wsescape.com.zone
$TTL 1D
$ORIGIN wsescape.com.
@ IN SOA ns.wsescape.com. admin.wsescape.com. (
2016042201
1H
5M
7D
1D )
IN NS ns
ns IN A 172.16.100.11
www IN A 172.16.100.11
[root@localhost named]# chmod 640 wsescape.com.zone
[root@localhost named]# chown :named wsescape.com.zone
#Start
[root@localhost named]# named -u named
#Resolution Normal
[root@localhost named]# dig -t A www.wsescape.com @172.16.100.11
#When we use rndc reload, etc., we are prompted that we do not have a configuration file #To make rndc available, use rndc-confgen to generate a configuration file #If blocking occurs using rndc-confgen, use rndc-confgen-r/dev/urandom to generate random numbers # use rndc-confgen The resulting file will#Start and#Configuration files between End s are placed in/etc/named/rndc.conf, and subsequent content is placed in/etc/named/named.conf as prompted
[root@localhost ~]# rndc-confgen
# Start of rndc.conf
key "rndc-key" {
algorithm hmac-md5;
secret "ZeE7NXZTprjARrGN/KRANQ==";
};
options {
default-key "rndc-key";
default-server 127.0.0.1;
default-port 953;
};
# End of rndc.conf
# Use with the following in named.conf, adjusting the allow list as needed:
# key "rndc-key" {
#algorithm hmac-md5;
#secret "ZeE7NXZTprjARrGN/KRANQ==";
# };
#
# controls {
#inet 127.0.0.1 port 953
#allow { 127.0.0.1; } keys { "rndc-key"; };
# };
# End of named.conf
#Now rndc reload is available
[root@localhost ~]# rndc reload
#After that, just provide a script to start and close the service like a service
#Compile and install, there is a contrib directory under bind-9.10.1-P1 source directory #Included are complementary enhancements to bind contributed by third parties #One of the directories contains some scripts for scripts, which we can refer to #There is also a directory called queryperf to evaluate query performance, which is presumptive and requires compilation and installation to be used #Compiling and installing queryperf requires only execution under its directory. /configure and make to complete #The queryperf executable is generated and can be used directly by doing the following [root@localhost queryperf]# cp queryperf /usr/local/bind9/bin/ #When testing, you need to specify a test file, such as test [root@localhost ~]# vim test www.wsescape.com A wsescape.com NS [root@localhost ~]# queryperf -d test -s 172.16.100.11
Author: Escape