1, Morphology
Morphological operation is actually to change the shape of an object. For example, corrosion is "getting thinner" and expansion is "getting fatter". You can see from the following figure:
(http://ex2tron.wang/opencv-python-erode-and-dilate/)

Experience: morphological operations generally act on binary graphs to connect adjacent elements or separate them into independent elements. Corrosion and expansion are aimed at the white (i.e. foreground) part in the picture!
Open / close operation
Corrosion before expansion is called open operation (because corrosion first will separate objects, which is easy to remember). Its function is to separate objects and eliminate small areas.
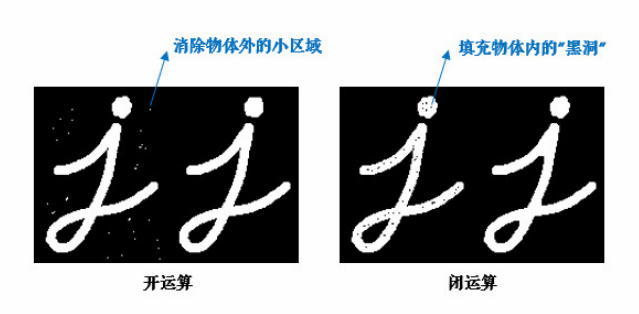
Experience: many people are not very clear about the role of opening and closing operation, but look at the figure ↑, don't be afraid: if there are many irrelevant small areas outside our target object, use the opening operation to remove them; If there are many small black holes inside an object, they are filled with closed operations.
Why do we have to open and close the operation with expansion corrosion? In fact, the most important point of opening and closing operation is that it can maintain the original size of the object. Then one is to eliminate the holes in the object, and the other is to enhance the connection points between the objects.
Other morphological operations
- Morphological gradient: subtracting the corrosion diagram from the expansion diagram to obtain the contour of the object:

Expansion and corrosion can achieve the following effects:
1. Eliminate noise
2. Separate image elements are segmented and adjacent elements are connected in the image
3. Find the obvious maximum or minimum region in the image
4. Calculate the gradient of the image
Note: both corrosion and expansion are for the white part (highlighted part) of the image. Expansion is the expansion of the highlighted part in the image, which is similar to domain expansion. The effect image has a larger highlighted area than the original image; Corrosion is that the highlighted part of the original image is corroded, which is similar to the field being eroded. The effect image has a smaller highlighted area than the original image.
From a mathematical point of view, the expansion and corrosion operation is to convolute the image with the core, which can be of any shape and size.

How did inflation come about? Find the local maximum.
The original image is convoluted with the kernel, and the maximum value is given to the specified pixel, so as to make the bright one brighter. The effect is that the bright area expands.
Let's talk about Erosion:
The operation is the opposite of expansion. Find the local minimum.
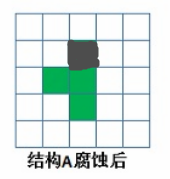
It can be understood that moving structure B (core), if the intersection of structure B and structure A completely belongs to the area of structure A, the location point is saved, and all qualified points constitute the result that structure A is corroded by structure B.

A the result of corrosion seems wrong, as if it should be like this:
. partial codes
% Feature point matching
% Point type matching
% tic; toc time
% After finding a feature point, find forty endpoints or intersections around it, and count the number of intersections and endpoints of forty points
% If the proportion of breakpoints in the two images is approximately the same, they are matched
% fff=abs(f11-f21)/(f11+f12) The closer to 0, the higher the matching degree
close all;
tic;
clear;
thin1=tuxiangyuchuli('zhiwen.png');
thin2=tuxiangyuchuli('zhiwen.png');
figure;
txy1=point(thin1);
txy2=point(thin2);
[w1,txy1]=guanghua(thin2,txy2);
[w2,txy2]=guanghua(thin2,txy2);
thin1=w1;
thin2=w2;
txy1=cut(thin1,txy1);
txy2=cut(thin2,txy2);
[pxy31,error2]=combine(thin1,8,txy1,60);
[pxy32,error2]=combine(thin2,8,txy2,60);
error=1;
num=20;
cxy1=pxy31;
cxy2=pxy32;
d1=distance(cxy1(1,1),cxy1(1,2),num,thin1);
d2=distance(cxy2(1,1),cxy2(1,2),num,thin2);
f=(sum(abs((d1./d2)-1)));
if(f<0.5)
error=0;
else
error=1;
end
f
c11=find_point(cxy1(1,1),cxy1(1,2),txy1,1);
c12=find_point(cxy1(1,1),cxy1(1,2),txy1,2);
c21=find_point(cxy2(1,1),cxy2(1,2),txy2,1);
c22=find_point(cxy2(1,1),cxy2(1,2),txy2,2);
cxy1(2,:)=c11;
cxy1(3,:)=c12(2,:);
cxy2(2,:)=c21;
cxy2(3,:)=c22(2,:);
x11=cxy1(1,1);y11=cxy1(1,2);
x12=cxy1(2,1);y12=cxy1(2,2);
x13=cxy1(3,1);y13=cxy1(3,2);
x21=cxy2(1,1);y21=cxy2(1,2);
x22=cxy2(2,1);y22=cxy2(2,2);
x23=cxy2(3,1);y23=cxy2(3,2);
dd1(1)=juli(x11,y11,x12,y12);
dd1(2)=juli(x12,y12,x13,y13);
dd1(3)=juli(x13,y13,x11,y11);
dd2(1)=juli(x22,y21,x22,y22);
dd2(2)=juli(x22,y22,x23,y23);
dd2(3)=juli(x23,y23,x21,y21);
ff=sum(sum(abs((d1./d2)-1)))
if ff<1
error=0
else error=1
end
cxy1(2:41,:)=find_point(pxy31(1,1),pxy31(1,2),txy1,40);
cxy2(2:41,:)=find_point(pxy32(1,1),pxy32(1,2),txy2,40);
f11=length(find(cxy1(:,3)==2));
f12=length(find(cxy1(:,3)==6));
f21=length(find(cxy2(:,3)==2));
f22=length(find(cxy2(:,3)==6));
fff=abs(f11-f21)/(f11+f12)
toc
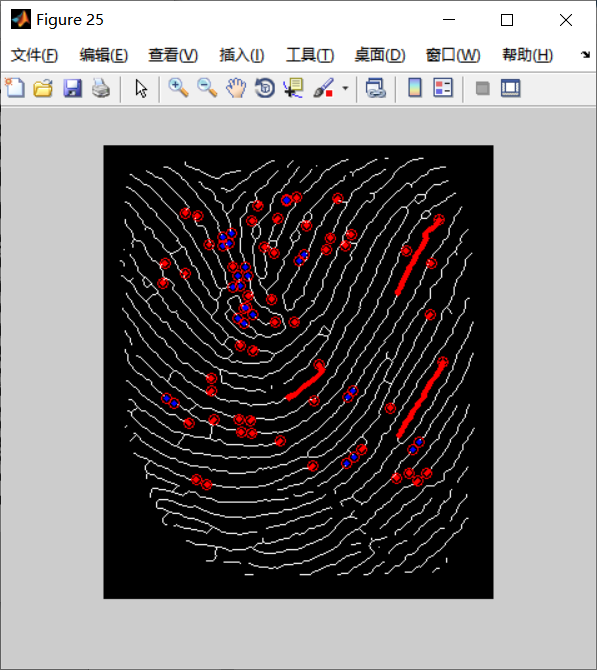
3, Simulation results
4, References
[1] Real time identity authentication system based on high-capacity fingerprint identification [J]. China Science and technology information, 2021 (16): 11