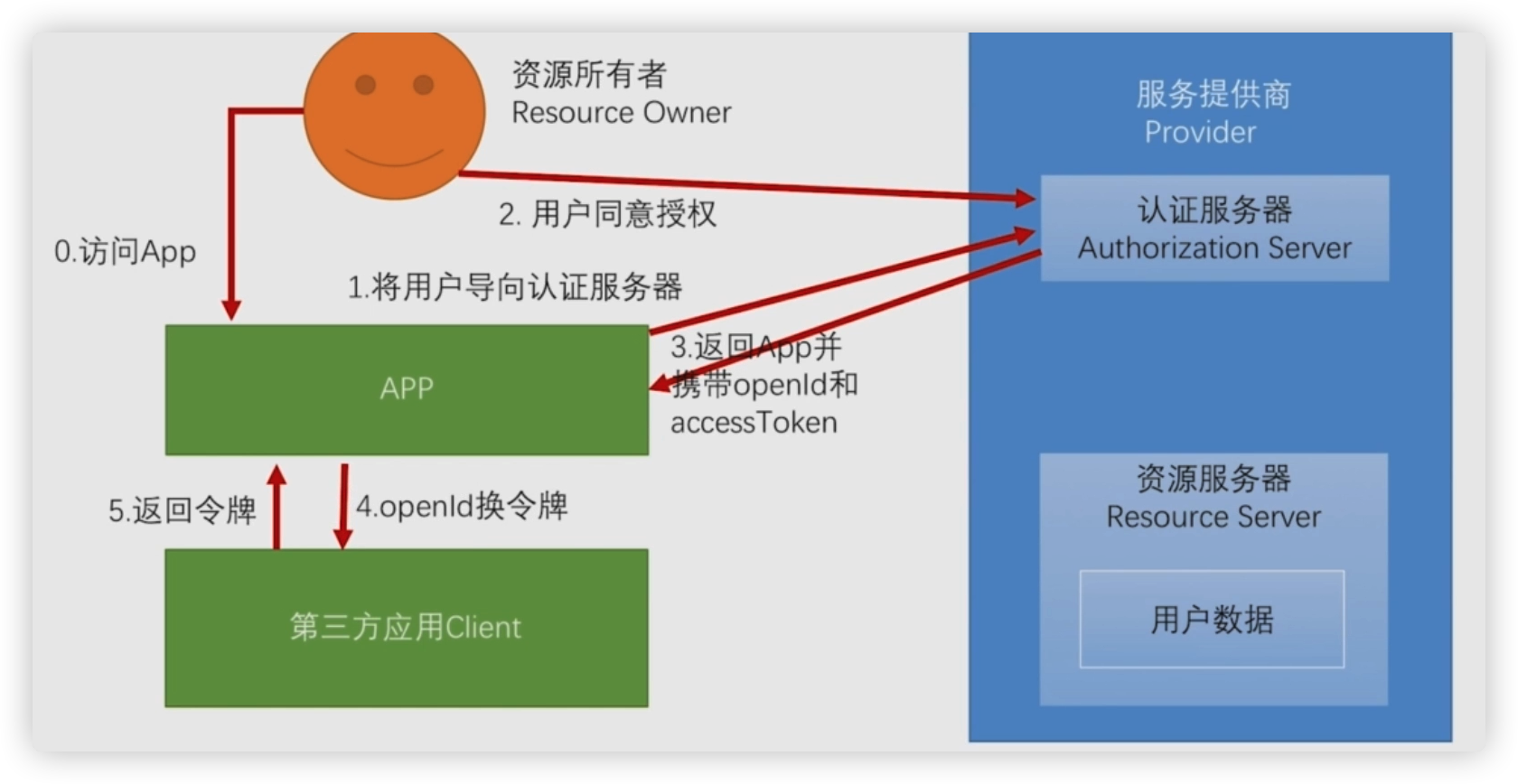
brief introduction
SDK is generally provided for APP social login. There are two situations for SDK
First kind
SDK provider returns openId and logs in to our interface system with openId to apply for token
Create the OpenIdAuthenticationToken class:
/** * */ package com.spring.security.social.openid; import java.util.Collection; import org.springframework.security.authentication.AbstractAuthenticationToken; import org.springframework.security.core.GrantedAuthority; import org.springframework.security.core.SpringSecurityCoreVersion; public class OpenIdAuthenticationToken extends AbstractAuthenticationToken { private static final long serialVersionUID = SpringSecurityCoreVersion.SERIAL_VERSION_UID; // ~ Instance fields // ================================================================================================ private final Object principal; private String providerId; // ~ Constructors // =================================================================================================== /** * This constructor can be safely used by any code that wishes to create a * <code>UsernamePasswordAuthenticationToken</code>, as the {@link #isAuthenticated()} * will return <code>false</code>. * */ public OpenIdAuthenticationToken(String openId, String providerId) { super(null); this.principal = openId; this.providerId = providerId; setAuthenticated(false); } /** * This constructor should only be used by <code>AuthenticationManager</code> or * <code>AuthenticationProvider</code> implementations that are satisfied with * producing a trusted (i.e. {@link #isAuthenticated()} = <code>true</code>) * authentication token. * * @param principal * @param credentials * @param authorities */ public OpenIdAuthenticationToken(Object principal, Collection<? extends GrantedAuthority> authorities) { super(authorities); this.principal = principal; super.setAuthenticated(true); // must use super, as we override } // ~ Methods // ======================================================================================================== @Override public Object getCredentials() { return null; } @Override public Object getPrincipal() { return this.principal; } public String getProviderId() { return providerId; } @Override public void setAuthenticated(boolean isAuthenticated) throws IllegalArgumentException { if (isAuthenticated) { throw new IllegalArgumentException( "Cannot set this token to trusted - use constructor which takes a GrantedAuthority list instead"); } super.setAuthenticated(false); } @Override public void eraseCredentials() { super.eraseCredentials(); } }
Create the OpenIdAuthenticationFilter class:
/** * */ package com.spring.security.social.openid; import javax.servlet.http.HttpServletRequest; import javax.servlet.http.HttpServletResponse; import com.spring.security.properties.SecurityConstants; import org.springframework.security.authentication.AuthenticationServiceException; import org.springframework.security.core.Authentication; import org.springframework.security.core.AuthenticationException; import org.springframework.security.web.authentication.AbstractAuthenticationProcessingFilter; import org.springframework.security.web.util.matcher.AntPathRequestMatcher; import org.springframework.util.Assert; /** * openId */ public class OpenIdAuthenticationFilter extends AbstractAuthenticationProcessingFilter { // ~ Static fields/initializers // ===================================================================================== private String openIdParameter = SecurityConstants.DEFAULT_PARAMETER_NAME_OPENID; private String providerIdParameter = SecurityConstants.DEFAULT_PARAMETER_NAME_PROVIDERID; private boolean postOnly = true; // ~ Constructors // =================================================================================================== public OpenIdAuthenticationFilter() { super(new AntPathRequestMatcher(SecurityConstants.DEFAULT_SIGN_IN_PROCESSING_URL_OPENID, "POST")); } // ~ Methods // ======================================================================================================== @Override public Authentication attemptAuthentication(HttpServletRequest request, HttpServletResponse response) throws AuthenticationException { if (postOnly && !request.getMethod().equals("POST")) { throw new AuthenticationServiceException("Authentication method not supported: " + request.getMethod()); } String openid = obtainOpenId(request); String providerId = obtainProviderId(request); if (openid == null) { openid = ""; } if (providerId == null) { providerId = ""; } openid = openid.trim(); providerId = providerId.trim(); OpenIdAuthenticationToken authRequest = new OpenIdAuthenticationToken(openid, providerId); // Allow subclasses to set the "details" property setDetails(request, authRequest); return this.getAuthenticationManager().authenticate(authRequest); } /** * Get openId */ protected String obtainOpenId(HttpServletRequest request) { return request.getParameter(openIdParameter); } /** * Get provider id */ protected String obtainProviderId(HttpServletRequest request) { return request.getParameter(providerIdParameter); } /** * Provided so that subclasses may configure what is put into the * authentication request's details property. * * @param request * that an authentication request is being created for * @param authRequest * the authentication request object that should have its details * set */ protected void setDetails(HttpServletRequest request, OpenIdAuthenticationToken authRequest) { authRequest.setDetails(authenticationDetailsSource.buildDetails(request)); } /** * Sets the parameter name which will be used to obtain the username from * the login request. * * @param openIdParameter * the parameter name. Defaults to "username". */ public void setOpenIdParameter(String openIdParameter) { Assert.hasText(openIdParameter, "Username parameter must not be empty or null"); this.openIdParameter = openIdParameter; } /** * Defines whether only HTTP POST requests will be allowed by this filter. * If set to true, and an authentication request is received which is not a * POST request, an exception will be raised immediately and authentication * will not be attempted. The <tt>unsuccessfulAuthentication()</tt> method * will be called as if handling a failed authentication. * <p> * Defaults to <tt>true</tt> but may be overridden by subclasses. */ public void setPostOnly(boolean postOnly) { this.postOnly = postOnly; } public final String getOpenIdParameter() { return openIdParameter; } public String getProviderIdParameter() { return providerIdParameter; } public void setProviderIdParameter(String providerIdParameter) { this.providerIdParameter = providerIdParameter; } }
/** * openid Parameter name */ String DEFAULT_PARAMETER_NAME_OPENID = "openId"; /** * providerId Parameter name */ String DEFAULT_PARAMETER_NAME_PROVIDERID = "providerId"; /** * Default OPENID login request processing url */ String DEFAULT_SIGN_IN_PROCESSING_URL_OPENID = "/authentication/openid";
Create the OpenIdAuthenticationProvider class:
/** * */ package com.spring.security.social.openid; import java.util.HashSet; import java.util.Set; import org.apache.commons.collections.CollectionUtils; import org.springframework.security.authentication.AuthenticationProvider; import org.springframework.security.authentication.InternalAuthenticationServiceException; import org.springframework.security.core.Authentication; import org.springframework.security.core.AuthenticationException; import org.springframework.security.core.userdetails.UserDetails; import org.springframework.social.connect.UsersConnectionRepository; import org.springframework.social.security.SocialUserDetailsService; public class OpenIdAuthenticationProvider implements AuthenticationProvider { private SocialUserDetailsService userDetailsService; private UsersConnectionRepository usersConnectionRepository; /* * (non-Javadoc) * * @see org.springframework.security.authentication.AuthenticationProvider# * authenticate(org.springframework.security.core.Authentication) */ @Override public Authentication authenticate(Authentication authentication) throws AuthenticationException { OpenIdAuthenticationToken authenticationToken = (OpenIdAuthenticationToken) authentication; Set<String> providerUserIds = new HashSet<>(); providerUserIds.add((String) authenticationToken.getPrincipal()); Set<String> userIds = usersConnectionRepository.findUserIdsConnectedTo(authenticationToken.getProviderId(), providerUserIds); if(CollectionUtils.isEmpty(userIds) || userIds.size() != 1) { throw new InternalAuthenticationServiceException("Unable to get user information"); } String userId = userIds.iterator().next(); UserDetails user = userDetailsService.loadUserByUserId(userId); if (user == null) { throw new InternalAuthenticationServiceException("Unable to get user information"); } OpenIdAuthenticationToken authenticationResult = new OpenIdAuthenticationToken(user, user.getAuthorities()); authenticationResult.setDetails(authenticationToken.getDetails()); return authenticationResult; } /* * (non-Javadoc) * * @see org.springframework.security.authentication.AuthenticationProvider# * supports(java.lang.Class) */ @Override public boolean supports(Class<?> authentication) { return OpenIdAuthenticationToken.class.isAssignableFrom(authentication); } public SocialUserDetailsService getUserDetailsService() { return userDetailsService; } public void setUserDetailsService(SocialUserDetailsService userDetailsService) { this.userDetailsService = userDetailsService; } public UsersConnectionRepository getUsersConnectionRepository() { return usersConnectionRepository; } public void setUsersConnectionRepository(UsersConnectionRepository usersConnectionRepository) { this.usersConnectionRepository = usersConnectionRepository; } }
Create the OpenIdAuthenticationSecurityConfig class:
/** * */ package com.spring.security.social.openid; import org.springframework.beans.factory.annotation.Autowired; import org.springframework.security.authentication.AuthenticationManager; import org.springframework.security.config.annotation.SecurityConfigurerAdapter; import org.springframework.security.config.annotation.web.builders.HttpSecurity; import org.springframework.security.web.DefaultSecurityFilterChain; import org.springframework.security.web.authentication.AuthenticationFailureHandler; import org.springframework.security.web.authentication.AuthenticationSuccessHandler; import org.springframework.security.web.authentication.UsernamePasswordAuthenticationFilter; import org.springframework.social.connect.UsersConnectionRepository; import org.springframework.social.security.SocialUserDetailsService; import org.springframework.stereotype.Component; @Component public class OpenIdAuthenticationSecurityConfig extends SecurityConfigurerAdapter<DefaultSecurityFilterChain, HttpSecurity> { @Autowired private AuthenticationSuccessHandler hkAuthenticationSuccessHandler; @Autowired private AuthenticationFailureHandler hkAuthenticationFailureHandler; @Autowired private SocialUserDetailsService userDetailsService; @Autowired private UsersConnectionRepository usersConnectionRepository; @Override public void configure(HttpSecurity http) throws Exception { OpenIdAuthenticationFilter OpenIdAuthenticationFilter = new OpenIdAuthenticationFilter(); OpenIdAuthenticationFilter.setAuthenticationManager(http.getSharedObject(AuthenticationManager.class)); OpenIdAuthenticationFilter.setAuthenticationSuccessHandler(hkAuthenticationSuccessHandler); OpenIdAuthenticationFilter.setAuthenticationFailureHandler(hkAuthenticationFailureHandler); OpenIdAuthenticationProvider OpenIdAuthenticationProvider = new OpenIdAuthenticationProvider(); OpenIdAuthenticationProvider.setUserDetailsService(userDetailsService); OpenIdAuthenticationProvider.setUsersConnectionRepository(usersConnectionRepository); http.authenticationProvider(OpenIdAuthenticationProvider) .addFilterAfter(OpenIdAuthenticationFilter, UsernamePasswordAuthenticationFilter.class); } }
Configure add to resource server HkResourceServerConfig configuration:
@Autowired private OpenIdAuthenticationSecurityConfig openIdAuthenticationSecurityConfig; .apply(openIdAuthenticationSecurityConfig)
Start project:
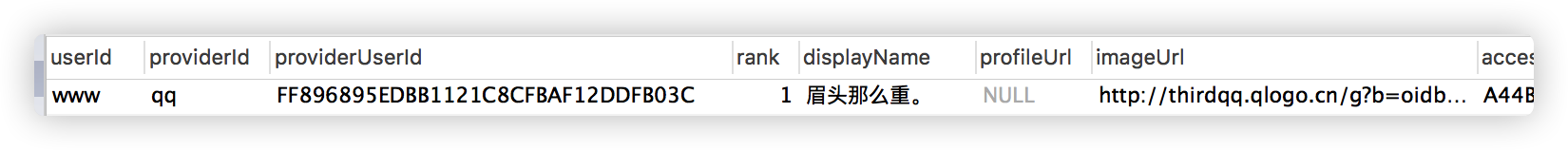
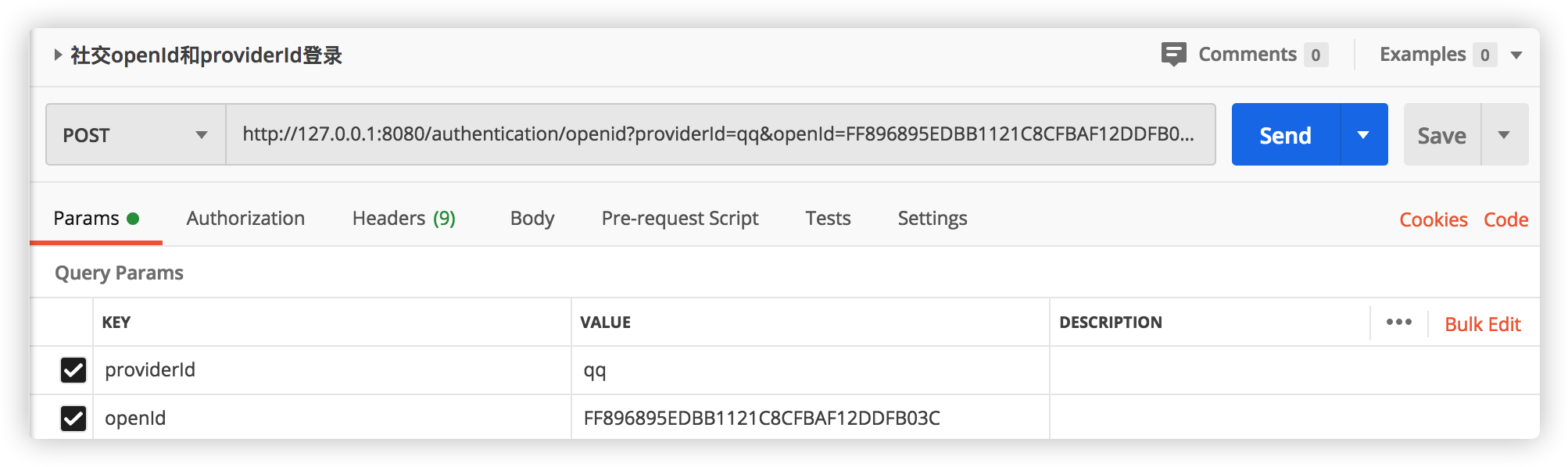
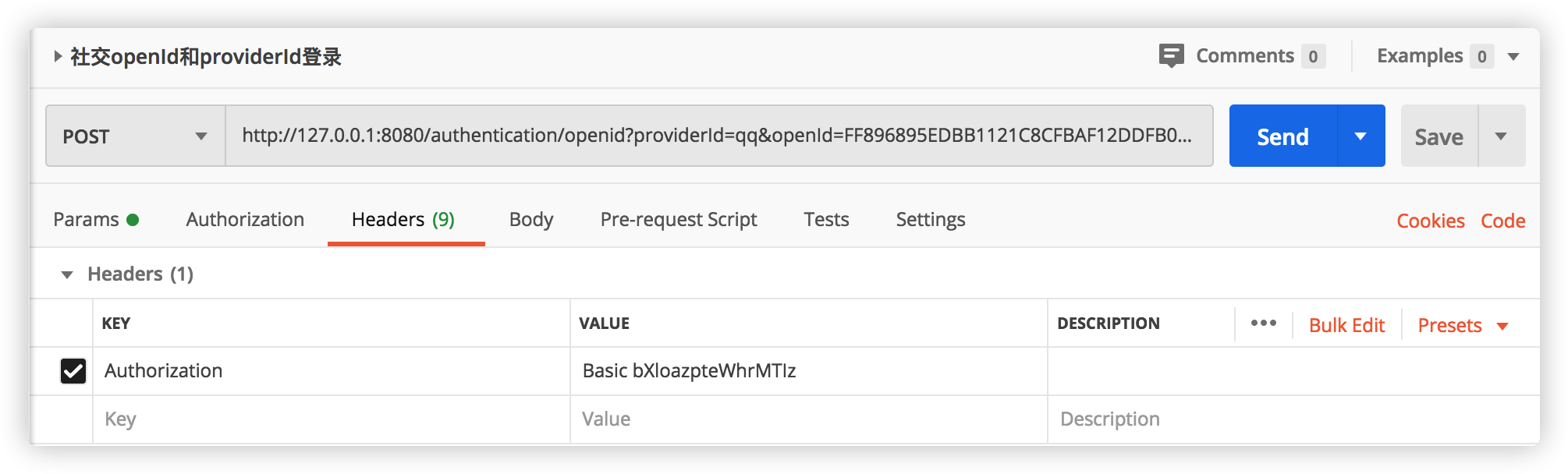
Click Send:
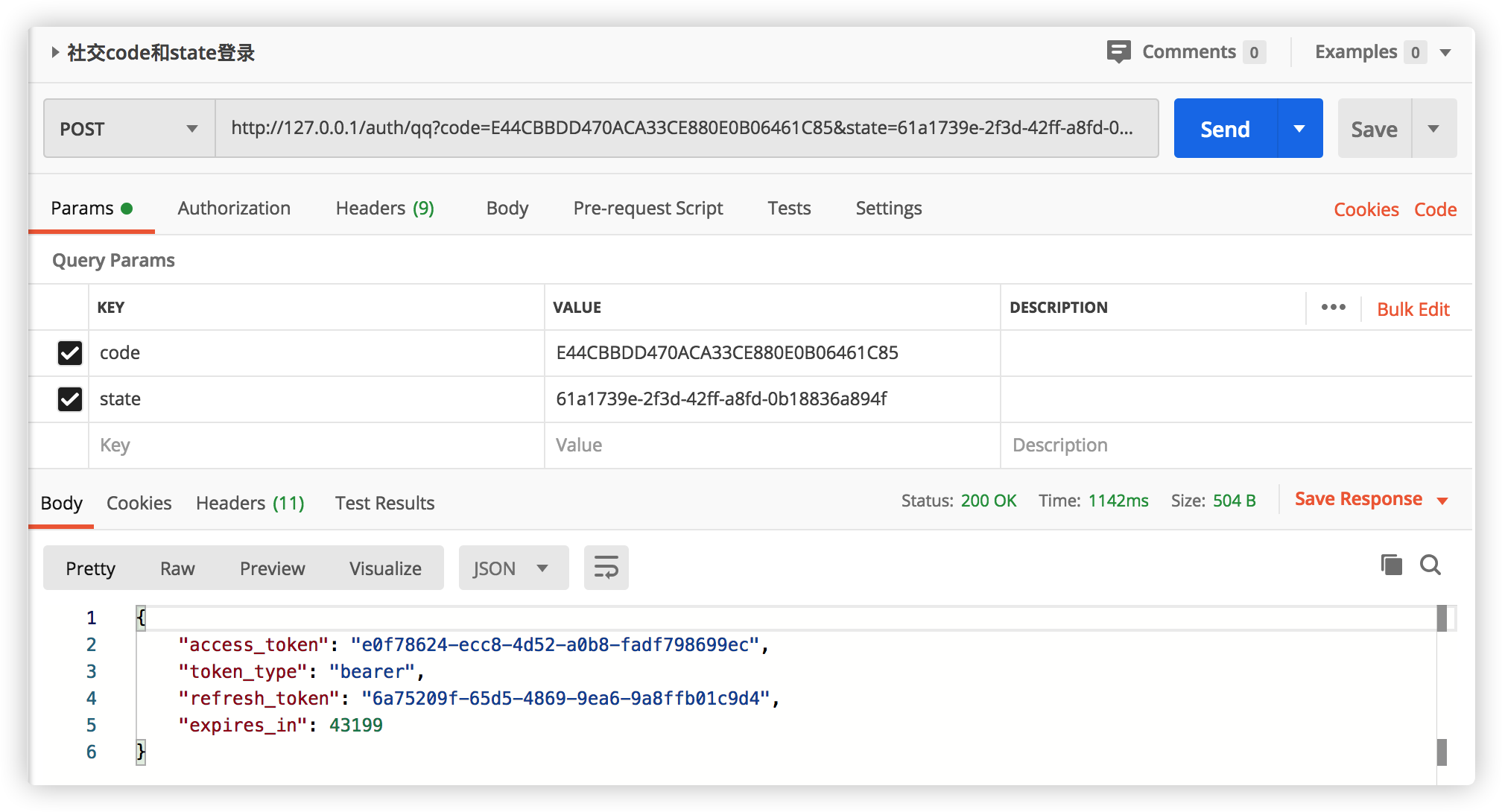
{ "access_token": "88c175c0-e6dc-465a-bb14-437b3436eae3", "token_type": "bearer", "refresh_token": "7e6b184c-688d-4565-97cf-88c57e38e482", "expires_in": 43159 }
Second kinds
The SDK provider returns the authorization code to the APP, and then the APP sends the authorization code to our interface system to apply for a token
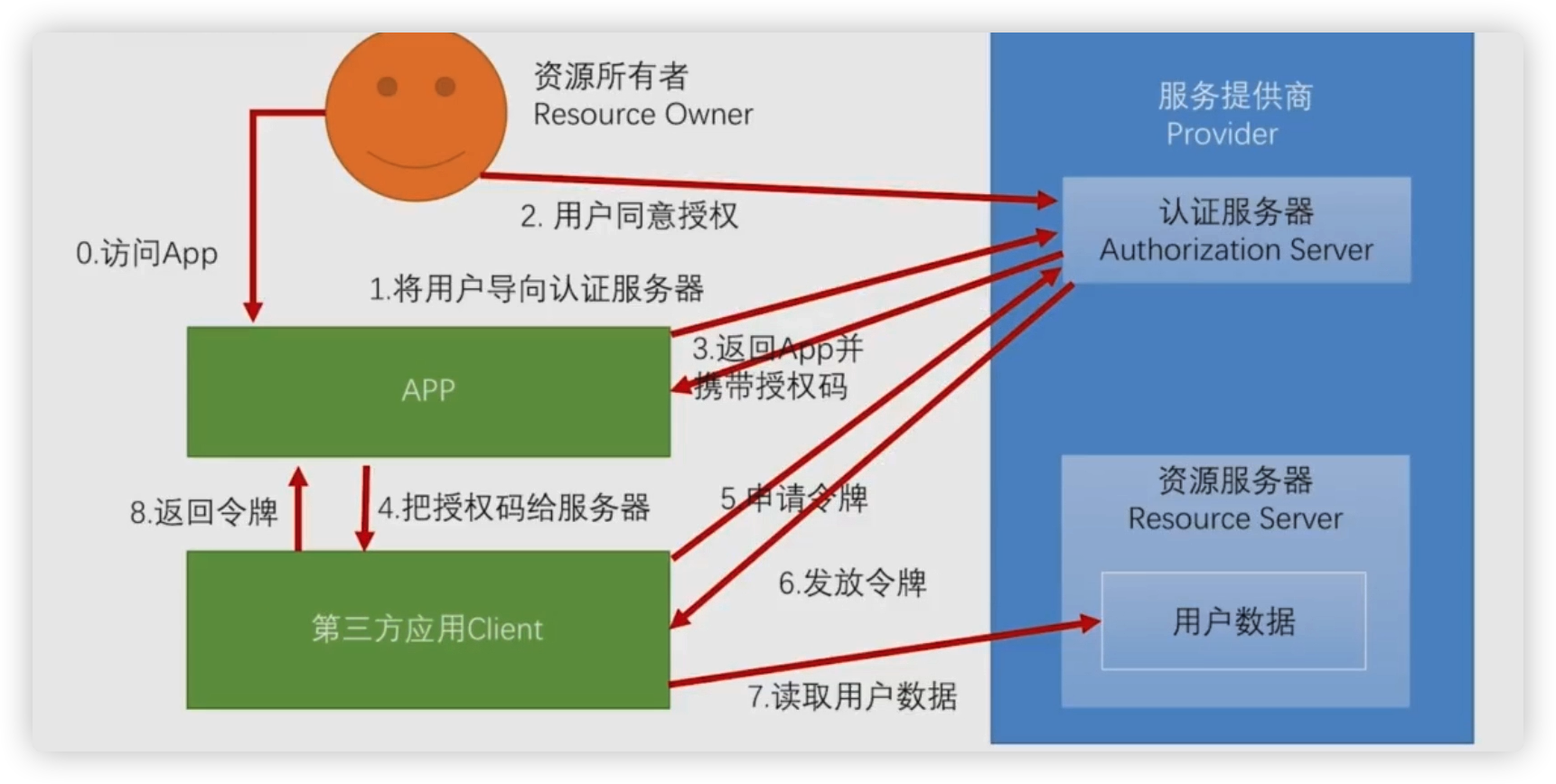
This mode is also supported by default
Modify the demo project pom:
<!--<dependency>--> <!--<groupId>com.spring.security</groupId>--> <!--<artifactId>spring-security-app</artifactId>--> <!--<version>${spring.security}</version>--> <!--</dependency>--> <dependency> <groupId>com.spring.security</groupId> <artifactId>spring-security-browser</artifactId> <version>${spring.security}</version> </dependency>
As we have previously saved the verification code in advance, the browser project creates a session operation verification code class:
package com.spring.security.validate.code.impl; import com.spring.security.validate.code.ValidateCode; import com.spring.security.validate.code.ValidateCodeRepository; import com.spring.security.validate.code.ValidateCodeType; import org.springframework.social.connect.web.HttpSessionSessionStrategy; import org.springframework.social.connect.web.SessionStrategy; import org.springframework.stereotype.Component; import org.springframework.web.context.request.ServletWebRequest; /** * Verification code accessor based on session * * @author zhailiang */ @Component public class SessionValidateCodeRepository implements ValidateCodeRepository { /** * Prefix of verification code when it is put into session */ String SESSION_KEY_PREFIX = "SESSION_KEY_FOR_CODE_"; /** * Tool class for operating session */ private SessionStrategy sessionStrategy = new HttpSessionSessionStrategy(); /** * Save verification code * * @param request * @param code * @param validateCodeType */ @Override public void save(ServletWebRequest request, ValidateCode code, ValidateCodeType validateCodeType) { sessionStrategy.setAttribute(request, getSessionKey(request, validateCodeType), code); } /** * Build the key when the verification code is put into the session * * @param request * @return */ private String getSessionKey(ServletWebRequest request, ValidateCodeType validateCodeType) { return SESSION_KEY_PREFIX + validateCodeType.toString().toUpperCase(); } /** * Get verification code * @param request * @param validateCodeType * @return */ @Override public ValidateCode get(ServletWebRequest request, ValidateCodeType validateCodeType) { return (ValidateCode) sessionStrategy.getAttribute(request, getSessionKey(request, validateCodeType)); } /** * Delete verification code * @param request * @param codeType */ @Override public void remove(ServletWebRequest request, ValidateCodeType codeType) { sessionStrategy.removeAttribute(request, getSessionKey(request, codeType)); } }
Debug mode startup project:
If you need to set a breakpoint here to log in using wechat, QQ does not need to
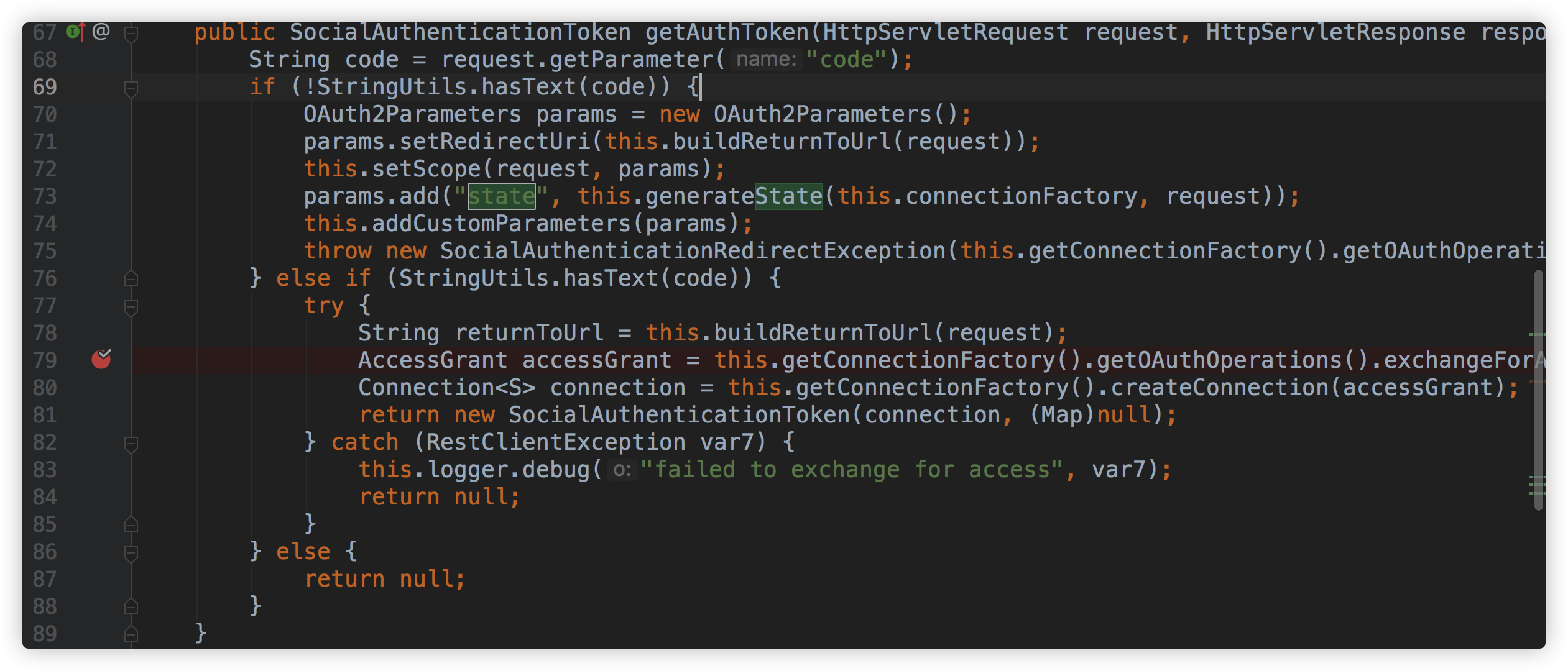
org.springframework.social.security.provider.OAuth2AuthenticationService
Find the OAuth2AuthenticationService class and set a breakpoint:
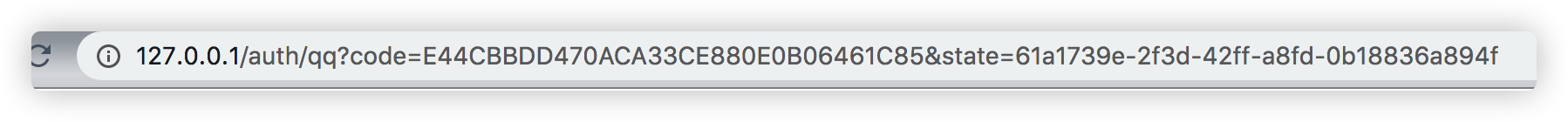
Visit http://127.0.0.1/signIn.html Click QQ to log in:
After coming out of this page, stop the project and then go back to the page and click qq to log in:
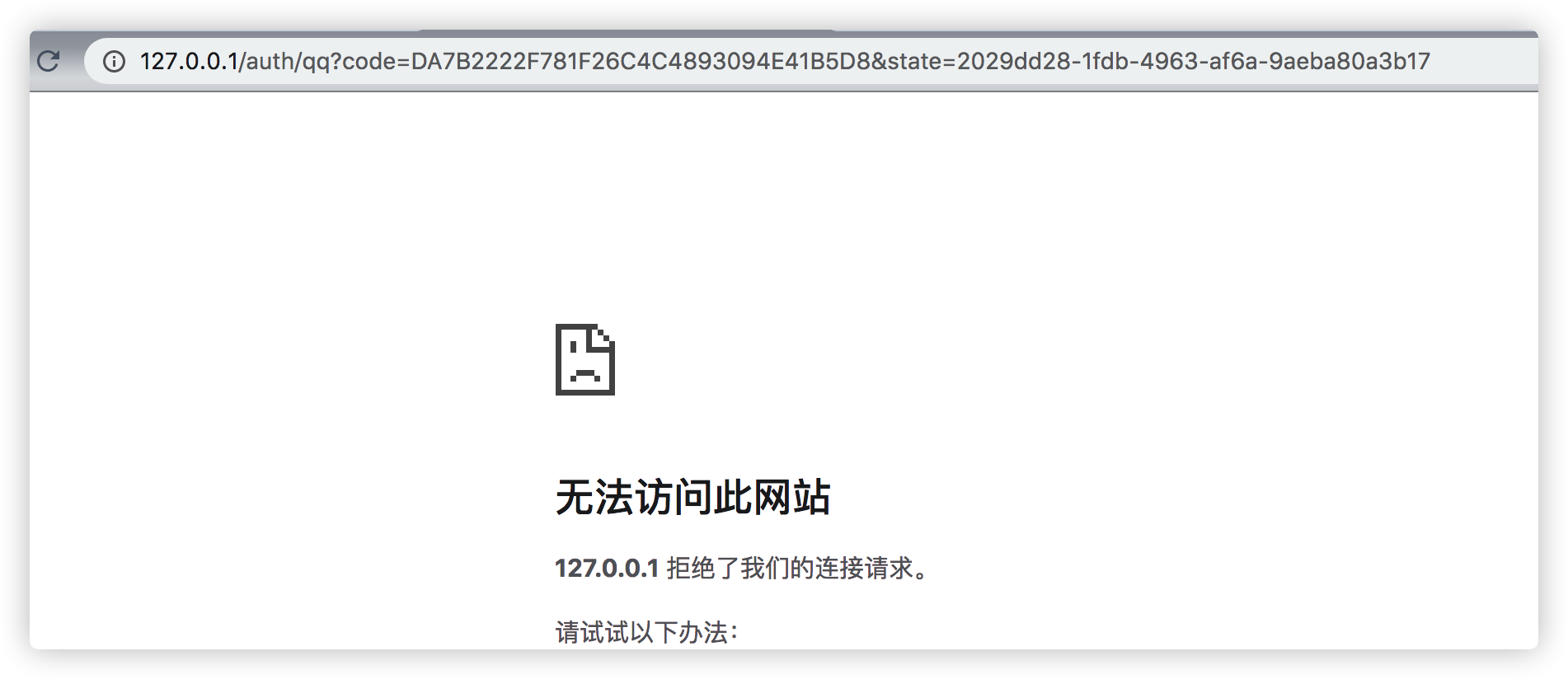
http://127.0.0.1/auth/qq?code=DA7B2222F781F26C4C4893094E41B5D8&state=2029dd28-1fdb-4963-af6a-9aeba80a3b17
Modify the pom dependency of the demo project again:
<dependency> <groupId>com.spring.security</groupId> <artifactId>spring-security-app</artifactId> <version>${spring.security}</version> </dependency> <!--<dependency>--> <!--<groupId>com.spring.security</groupId>--> <!--<artifactId>spring-security-browser</artifactId>--> <!--<version>${spring.security}</version>--> <!--</dependency>-->
Take these two paths
"/auth/qq", "/auth/weixin"
Start the project with Postman test:
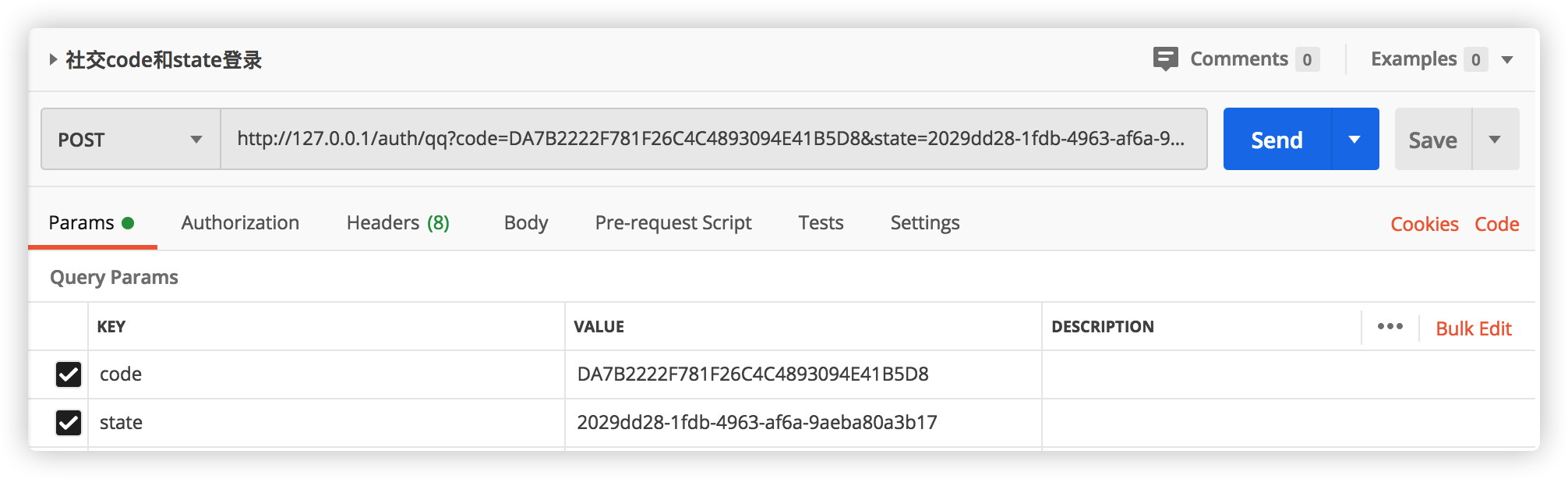
Click Send to return the message:
Full authentication is required to access this resource
{ "error": "unauthorized", "error_description": "Full authentication is required to access this resource" }
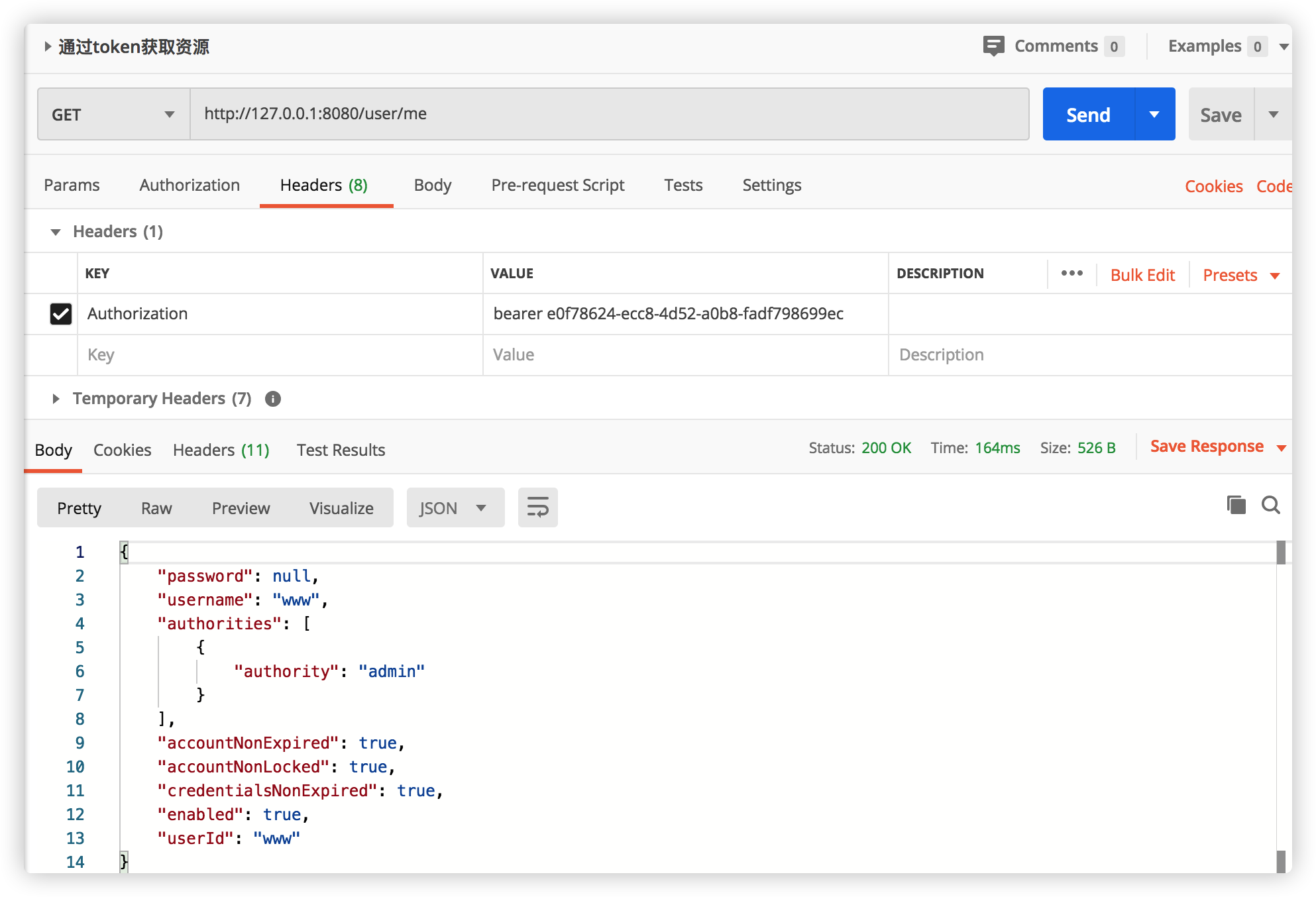
The IDE console output is actually logged in:
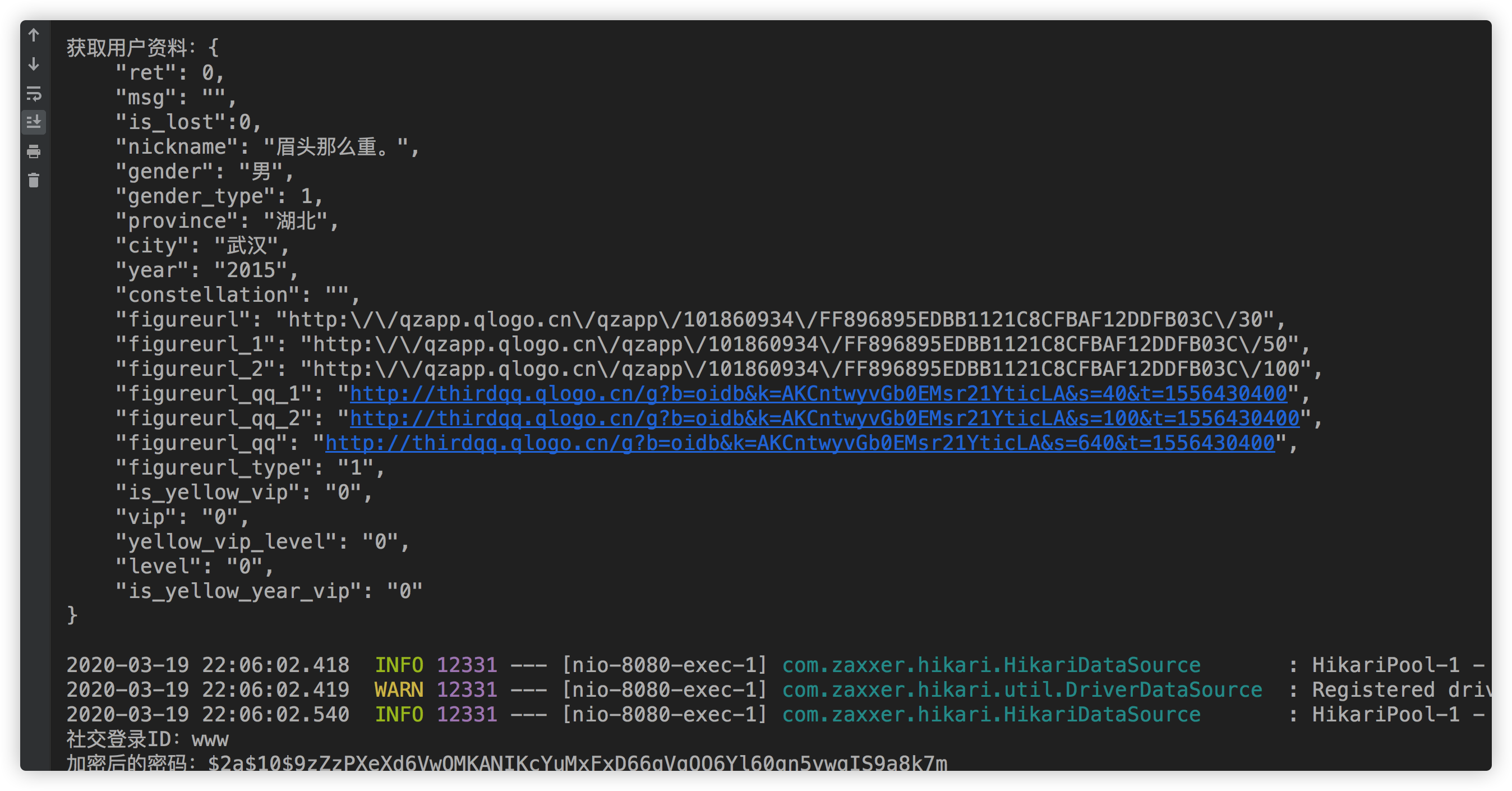
Click Send to return the message:
Console output code has been used
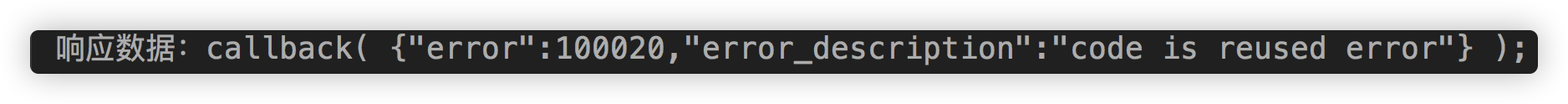
Reason: This is because the address we configured before for successful login jump uses the spring default request address, which is correct in browser mode, but we need to return the token token token in APP mode
package com.spring.security.social; import lombok.Data; import org.springframework.social.security.SocialAuthenticationFilter; import org.springframework.social.security.SpringSocialConfigurer; /** * Set login address */ @Data public class HkSpringSocialConfigurer extends SpringSocialConfigurer { private String filterProcessesUrl; public HkSpringSocialConfigurer(String filterProcessesUrl){ this.filterProcessesUrl = filterProcessesUrl; } @Override protected <T> T postProcess(T object) { SocialAuthenticationFilter filter = (SocialAuthenticationFilter) super.postProcess(object); filter.setFilterProcessesUrl(filterProcessesUrl); return (T) filter; } }
Solution: extract as interface
Create under the path of core project com.spring.security.social
package com.spring.security.social; import org.springframework.social.security.SocialAuthenticationFilter; public interface SocialAuthenticationFilterPostProcessor { void processor(SocialAuthenticationFilter socialAuthenticationFilter); }
Modify the HkSpringSocialConfigurer class:
package com.spring.security.social; import lombok.Data; import org.springframework.social.security.SocialAuthenticationFilter; import org.springframework.social.security.SpringSocialConfigurer; /** * Set login address */ @Data public class HkSpringSocialConfigurer extends SpringSocialConfigurer { private String filterProcessesUrl; private SocialAuthenticationFilterPostProcessor socialAuthenticationFilterPostProcessor; public HkSpringSocialConfigurer(String filterProcessesUrl) { this.filterProcessesUrl = filterProcessesUrl; } @Override protected <T> T postProcess(T object) { SocialAuthenticationFilter filter = (SocialAuthenticationFilter) super.postProcess(object); filter.setFilterProcessesUrl(filterProcessesUrl); //No need to implement social authentication filter postprocessor in browser mode if (socialAuthenticationFilterPostProcessor != null) { socialAuthenticationFilterPostProcessor.processor(filter); } return (T) filter; } }
Modify the SocialConfig class Bean processing:
@Bean public SpringSocialConfigurer hkSocialSecurityConfig() { // Default configuration class for component assembly // Include filter SocialAuthenticationFilter added to security filter chain //Custom login path String filterProcessesUrl = this.securityProperties.getSocial().getFilterProcessesUrl(); HkSpringSocialConfigurer configurer = new HkSpringSocialConfigurer(filterProcessesUrl); //Custom registration page configurer.signupUrl(securityProperties.getBrowser().getSignUpUrl()); //Post processor configurer.setSocialAuthenticationFilterPostProcessor(socialAuthenticationFilterPostProcessor); return configurer; }
Configure APP project to create AppSocialAuthenticationFilterPostProcessor to implement SocialAuthenticationFilterPostProcessor
package com.spring.security.social.openid.impl; import com.spring.security.social.SocialAuthenticationFilterPostProcessor; import org.springframework.beans.factory.annotation.Autowired; import org.springframework.security.web.authentication.AuthenticationSuccessHandler; import org.springframework.social.security.SocialAuthenticationFilter; import org.springframework.stereotype.Component; @Component public class AppSocialAuthenticationFilterPostProcessor implements SocialAuthenticationFilterPostProcessor { @Autowired private AuthenticationSuccessHandler hkAuthenticationSuccessHandler; //Configure return token success processor @Override public void processor(SocialAuthenticationFilter socialAuthenticationFilter) { socialAuthenticationFilter.setAuthenticationSuccessHandler(hkAuthenticationSuccessHandler); } }
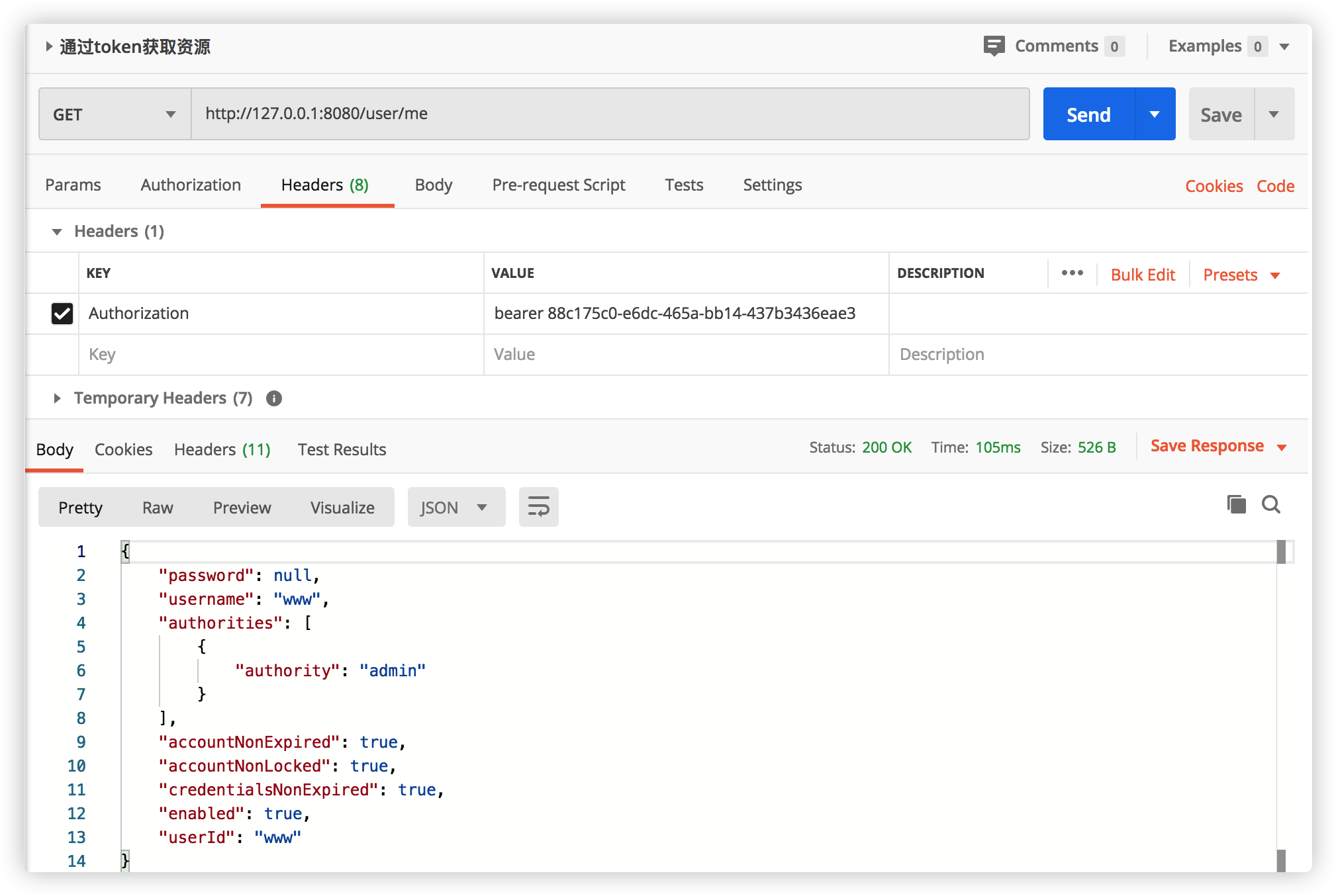
The configuration is finished here. Repeat the above steps to get the code link: