Background: Recently, I suddenly came into contact with OpenSSL. I suddenly thought that I had not written anything related to the deployment of Django + uWSGI + Nginx + https project, so I sorted out a piece of data.
1, OpenSSL installation
Download the latest stable version from OpenSSL official website, I downloaded 2.0.16, official website: https://www.openssl.org/source/
-
Install dependent environment
#Check whether gcc is installed, if so, it is not necessary to install gcc -v #install yum -y install gcc
#Check if zlib library is installed, if so, no installation is required whereis zlib #install yum -y install zlib
-
Download OpenSSL installation package
wget https://www.openssl.org/source/openssl-fips-2.0.16.tar.gz
-
decompression
tar -xzf openssl-fips-2.0.16.tar.gz
-
Entry directory
cd openssl-fips-2.0.16/
-
Set installation path
./config --prefix=/usr/local/openssl
-
Compilation and installation
make && make install
-
View version
openssl version
2, Generate certificate
-
Create a directory
Used to save the certificate and private key. (it can also be placed in other directories)
mkdir /home/key_dir
-
Entry directory
cd /home/key_dir
-
Create server private key
Note: the length is 1024 bits, of the des3 encryption algorithm
openssl genrsa -des3 -out server.key 1024
-
Create certificate CSR for signing request
First, you will enter the password (set above), and you will be asked to enter the country, such as CN, province, city, company and a series of information. You can enter whatever you want to play
The last A challenge password []: and An optional company name []: can be directly entered to skip
openssl req -new -key server.key -out server.csr
-
Remove the required password when loading the SSL supported Nginx and using the above private key
cp server.key server.key.org openssl rsa -in server.key.org -out server.key #Password required
-
Tag certificate uses the above private key and CSR
Note: 365 is the expiration date
openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt
-
Check whether the certificate and private key are created successfully
[root@localhost key_dir]# ls server.crt server.csr server.key server.key.org [root@localhost key_dir]#
3, Nginx configuration
Because I have deployed projects before, I just need to modify the Nginx configuration file
For Django + Nginx + uWSGI deployment, please refer to my previous article: https://blog.csdn.net/weixin_44110998/article/details/104001529
-
Modify nginx.conf
In fact, on the basis of the original configuration, change the original listening port (80 for me) to listening 443, and then add the key related configuration
http { ...... server { listen 443; #Ports to monitor server_name localhost; ssl on; ssl_certificate /home/key_dir/server.crt; ssl_certificate_key /home/key_dir/server.key; location / { include uwsgi_params; uwsgi_pass 127.0.0.1:8080; #Same as ip: port in uwsgi uwsgi_send_timeout 600; } #Static file location /static { alias /home/nginx_test/static/; #Static file path } } ...... }
-
Check whether Nginx installs HTTP? SSL? Module
/usr/local/nginx/sbin/nginx -V
[root@localhost nginx-1.9.9]# /usr/local/nginx/sbin/nginx -V nginx version: nginx/1.9.9 built by gcc 4.8.5 20150623 (Red Hat 4.8.5-39) (GCC) built with OpenSSL 1.0.2k-fips 26 Jan 2017 TLS SNI support enabled configure arguments: --prefix=/usr/local/nginx --with-http_ssl_module [root@localhost nginx-1.9.9]#
If the words of the last line of the above code appear: - with-http_ssl_module, it has been installed. The following steps can be skipped to modify nginx.conf directly
Go to nginx decompression directory to execute (download again if deleted):
./configure --with-http_ssl_module
If an error is reported. / configure: error: SSL modules require the OpenSSL library
yum -y install openssl openssl-devel ./configure ./configure --with-http_ssl_module
Execute make (remember that make install will overwrite the installation directory)
make
Backup the original nginx
cp /usr/local/nginx/sbin/nginx /usr/local/nginx/sbin/nginx.bak
Overwrite the old installation directory with the new nginx
cp -rfp objs/nginx /usr/local/nginx/sbin/nginx
Test whether nginx is correct
/usr/local/nginx/sbin/nginx -t
Error run result:
[root@localhost nginx-1.9.9]# /usr/local/nginx/sbin/nginx -t nginx: [emerg] unknown directive "ssl" in /usr/local/nginx/conf/nginx.conf:43 nginx: configuration file /usr/local/nginx/conf/nginx.conf test failed [root@localhost nginx-1.9.9]#
Correct operation result:
[root@localhost nginx-1.9.9]# /usr/local/nginx/sbin/nginx -t nginx: the configuration file /usr/local/nginx/conf/nginx.conf syntax is ok nginx: configuration file /usr/local/nginx/conf/nginx.conf test is successful [root@localhost nginx-1.9.9]#
-
Start Nginx
If it has been started, it will stop at the start (Note: I used restart when testing, no error was reported, but the sll certificate did not take effect, then it is ok to stop at the start)
/usr/local/nginx/sbin/nginx # start-up /usr/local/nginx/sbin/nginx -s stop # Stop it /usr/local/nginx/sbin/nginx -s reload # restart
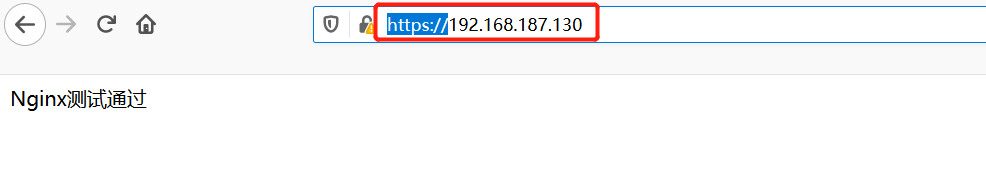
4, Access test
Now direct access to IP: the port should not be accessible. https://