#################sshd services two computers can login without password ssh, which is a safer way.
sshd connection:
Host Connect Virtual Machine
[kiosk@foundation71 ~]$ ssh root@172.25.254.100 -X root@172.25.254.100's password: Last login: Sun Aug 18 15:57:46 2019 [root@desktop ~]#
########## The first link to an unfamiliar host is to establish an authentication file, so I will ask if it is established. I need to enter yes tree. When I link to this host again, because it has been generated.
#### The method of not requiring a key after loading ssh connection
server200:
[root@server .ssh]# ssh-keygen ##Commands to generate keys Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): ##Specify a file that holds encrypted characters (using default) Enter passphrase (empty for no passphrase): ##Set a password (using an empty password) Enter same passphrase again: ##Confirm password Your identification has been saved in /root/.ssh/id_rsa. ##Private key (key) Your public key has been saved in /root/.ssh/id_rsa.pub. The key fingerprint is: 17:a7:d2:68:ed:a4:80:a8:29:95:74:27:84:fc:4a:33 root@server The key's randomart image is: +--[ RSA 2048]----+ | . .. | | o. | | ..o . . . | | .E+.+ + + | | .++. . S * | | +. o * | |+ . . | |. | | | +-----------------+ [root@server .ssh]# ssh-copy-id -i /root/.ssh/id_rsa.pub root@172.25.254.200 ##Encrypted sshd service The authenticity of host '172.25.254.200 (172.25.254.200)' can't be established. ECDSA key fingerprint is eb:24:0e:07:96:26:b1:04:c2:37:0c:78:2d:bc:b0:08. Are you sure you want to continue connecting (yes/no)? yes /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys root@172.25.254.200's password: ##Native password Number of key(s) added: 1Now try logging into the machine, with: "ssh 'root@172.25.254.200'" ###Attempt to connect to the local machine with ssh and check to make sure that only the key(s) you wanted were added. ##Give you the key you want.[root@server .ssh]# ls ##There are two keys in it. authorized_keys id_rsa id_rsa.pub known_hosts
### Key issuance
[root@server .ssh]# scp /root/.ssh/id_rsa root@172.25.254.100:/root/.ssh/ ##Give the private key to 100 clients The authenticity of host '172.25.254.100 (172.25.254.100)' can't be established. ECDSA key fingerprint is eb:24:0e:07:96:26:b1:04:c2:37:0c:78:2d:bc:b0:08. Are you sure you want to continue connecting (yes/no)? yes ##Input consent Warning: Permanently added '172.25.254.100' (ECDSA) to the list of known hosts. root@172.25.254.100's password: ##Enter client password id_rsa
client100:
[root@desktop .ssh]# ssh root@172.25.254.200 ##On the client side, we saw that the connection was asked once, but no password was needed. The authenticity of host '172.25.254.200 (172.25.254.200)' can't be established. ECDSA key fingerprint is eb:24:0e:07:96:26:b1:04:c2:37:0c:78:2d:bc:b0:08. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '172.25.254.200' (ECDSA) to the list of known hosts. Last failed login: Sun Aug 18 17:56:36 EDT 2019 from 172.25.254.100 on ssh:notty There were 2 failed login attempts since the last successful login. Last login: Sun Aug 18 17:56:01 2019 from 172.25.254.100 [root@server ~]# [root@server ~]# exit //Logout Connection to 172.25.254.200 closed. [root@desktop .ssh]# ls ###In client. There is a secret key in ssh id_rsa known_hosts
############### ssh is so convenient that we can set up relevant settings in the configuration file to ensure the security of ssh links.
server200
[root@server .ssh]# vim /etc/ssh/sshd_config ##In the configuration file, we can add the relevant functions we want. 48 PermitRootLogin yes|no ##Are root users allowed to authenticate through sshd services 52 Allowusers student westos ##Set a user whitelist, whitelist appears default no longer list users can not use sshd 53 Denyusers westos ##Set user blacklist, blacklist appears default no longer list users can use sshd 78 PasswordAuthentication yes|no ##Is the user allowed to authenticate sshd with the password of the login system
########## In addition to setting information, we also want to set the information displayed when sshd is connected.
server200:
[root@server .ssh]# vim /etc/motd ##File entry hello ##Write down information client100 ##Client [root@desktop .ssh]# ssh root@172.25.254.200 ##ssh Connect Server Last login: Sun Aug 18 18:01:34 2019 from 172.25.254.100 hello ##Displayed information [root@server ~]#
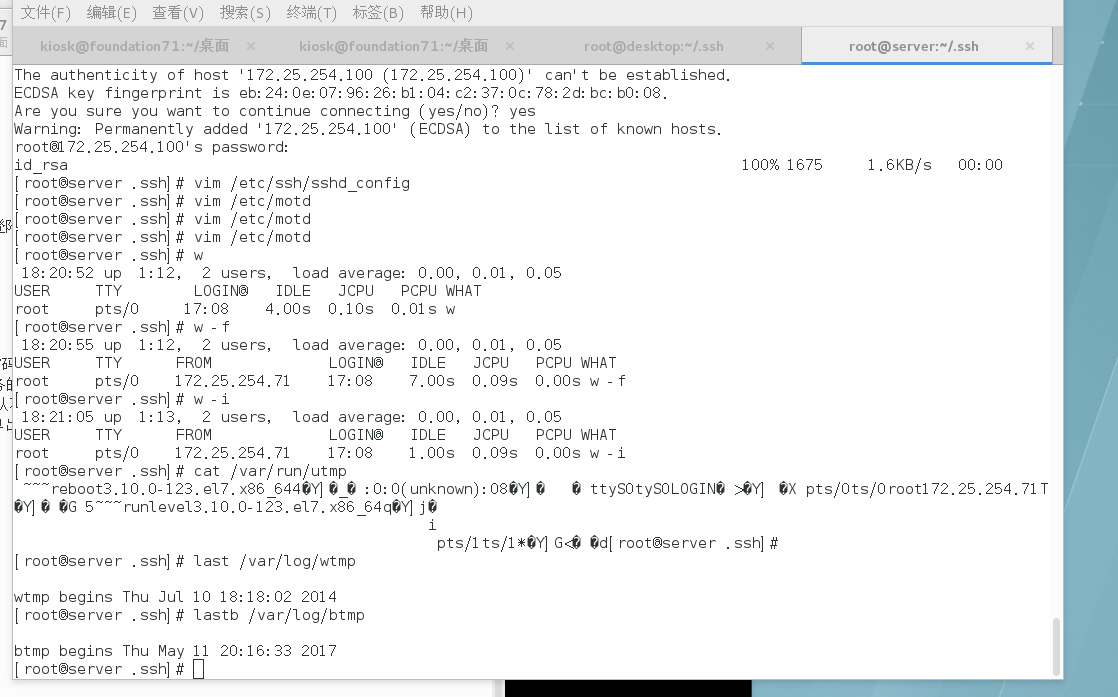
########## View ssh connections locally
1.w # View Users Using the Current System
- f # # View the Source of Use
- i # Display IP
/var/run/utmp
2.last # View User Information Used and Exit
/var/log/wtmp
3.lastb # Users who tried to log in but failed
/var/log/btmp