1. Background knowledge
What are 1.1, http, and https?
Simply put, http is a protocol for transferring web content, such as the website you see at the beginning of http http://www.163.com , the text, pictures, CSS, JS and other files on its web page are transferred to our browser through the http protocol, and then we can see them.

And HTTPS can be understood as "HTTP over SSL/TLS". Why does a good end of http need "over SSL/TLS"? Because http is transmitted in clear text, content transferred through the http protocol can be easily peeked at and tampered with, for security purposes (you certainly don't want to be peeked at or tampered with web page content, such as website bank password.)Add a layer of SSL/TLS security protocol to the http protocol, so there are https.
1.2 What is SSL/TLS?
"HTTP over SSL/TLS" literally means the HTTP protocol with a "Secure Socket Layer". Inner purity of mind can also be interpreted as "http with a condom", because it has a condom, it is certainly safer.SSL is the abbreviation for Secure Sockets Layer and means Secure Sockets Layer.TLS is short for Transport Layer Security and means Transport Layer Security Protocol.SSL and TLS are different phases of the same thing, so it's okay to understand that they are both security protocols.
1.3. Why deploy https?
In the end, HTTPS is safer.Even for security, a professional and reliable website, HTTPS is required.Both Firefox and Chrome plan to mark http sites that do not have SSL encryption configured as unsafe (as Firefox 50 seems to have done), and they are now joining other relevant foundations and companies to promote HTTPS across the Internet, some of the major websites you visit.For example, Google has enabled HTTPS completely many years ago, and domestic Taobao, Sogou, Zhizhi, Baidu and so on are also fully https.Even Google's search results are giving HTTPS sites higher rankings and preferential inclusion rights.
1.4. How do I deploy https?
All you need is a trusted CA (Certificate Authority), which is an SL security certificate issued by the Certificate Authority and deployed to your Web site server.Once deployed successfully, when a user visits your site, the browser will put a small green lock in front of the displayed web address, indicating that the site is secure, and you will also see the prefix of the web address changed to https, not http anymore.

1.5. How do I get an SSL security certificate?
In theory, we can also issue SSL security certificates ourselves, but our own security certificates will not be trusted by mainstream browsers, so we need security certificates issued by trusted Certificate Authorization Centers (CA s).Generally, SSL security certificate issuance services are more expensive. Certificates issued by Godaddy, GlobalSign and other institutions usually cost $20 a year or more. However, to speed up the spread of https, the EEF Electronic Outpost Foundation, the Mozilla Foundation, and the University of Michigan set up a public welfare organization called ISRG (Internet Security Research Group).The organization has introduced Let's Encrypt free certificates since 2015.This free certificate is not only free but also very useful, so we can deploy HTTPS using the free certificate provided by Let's Encrypt.So how do I get the Let's Encrypt security certificate and deploy it on my own web server?That's what this article is about.
2. Introduction to Let's Encrypt and Certbot
As mentioned earlier, Let's Encrypt is a free security certificate program launched by an organization called ISRG (Internet Security Research Group).Organizations and companies that participated in the program are arguably the top pioneers of the Internet. In addition to the three boisterous initiators mentioned earlier, Cisco (a global network device manufacturer), Akamai, and even the Linux Foundation joined in to ensure the reliability and sustainability of the project.

The ISRG sponsor EFF (Electronic Sentinel Foundation) later released an official client Certbot for the Let's Encrypt project, which can be used to fully automate the acquisition, deployment and updating of security certificates.This is really easy and convenient, so we can use the official client directly instead of using third-party tools.Although third-party tools can also be used, official tools are more authoritative, less risky, and easier to solve problems because of official support.What's more, Certbot is really convenient and more convenient than all third-party tools. Why not?
2.1, Authenticators and Installers
Certbot supports two types of plugin s, one for obtaining and installing certificates, called Authenticators;
The other is used to install certificates, called Installers.Some plugin s support one, while others support both, such as nginx.
Authenticators plugin uses the certonly command to obtain the certificate, while Installers plugin uses the install command to install the certificate.
22. plugin description
Here are a few common plugin s for a brief description:
- Webroot: If you have a webserver running locally and the ability to modify its configuration, you can use this method (create a hidden file.well-known) without pausing the webserver when you obtain a certificate.
- Standalone: The server is not running webserver s can use this method to keep ports 80 or 443 open.
- Nginx: Automatically acquire and install certificates (automatically modify configuration files).
3. Certbot Configure Certificate for nginx
3.1. Install certbot
Certbot's official website is https://certbot.eff.org/ Open this link to choose your own web server and operating system. EFF will give you detailed instructions on how to use it. Here is an example of the domain name of this site (bbs.wzlinux.com).
Our system environment is CentOS 7 and the Web server is nginx in the epel source. Just to cover up the installation certificate, there are no web pages. You know this process is the main one. We use the following command to install certbot.
yum install certbot python2-certbot-nginx
3.2. Generating Certificates
Before we use certbot to generate the certificate, we need to resolve the domain name to the current server, use the certificate generated by certbot --nginx, and automatically configure it on nginx, requiring us to enter the mailbox address.
[root@lnmp-1 ~]# certbot --nginx Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator nginx, Installer nginx Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): wangzan18@126.com Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at https://acme-v02.api.letsencrypt.org/directory - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (A)gree/(C)ancel: A - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: Y Starting new HTTPS connection (1): supporters.eff.org No names were found in your configuration files. Please enter in your domain name(s) (comma and/or space separated) (Enter 'c' to cancel): bbs.wzlinux.com Obtaining a new certificate Performing the following challenges: http-01 challenge for bbs.wzlinux.com Waiting for verification... Cleaning up challenges Resetting dropped connection: acme-v02.api.letsencrypt.org Deploying Certificate to VirtualHost /etc/nginx/nginx.conf Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: No redirect - Make no further changes to the webserver configuration. 2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for new sites, or if you're confident your site works on HTTPS. You can undo this change by editing your web server's configuration. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2 Redirecting all traffic on port 80 to ssl in /etc/nginx/nginx.conf - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Congratulations! You have successfully enabled https://bbs.wzlinux.com You should test your configuration at: https://www.ssllabs.com/ssltest/analyze.html?d=bbs.wzlinux.com - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/bbs.wzlinux.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/bbs.wzlinux.com/privkey.pem Your cert will expire on 2019-07-25. To obtain a new or tweaked version of this certificate in the future, simply run certbot again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot renew" - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
Enter your own information as prompted. If you want to manually configure the nginx certificate yourself, you can use the following command.
certbot --nginx certonly
3.3. Configuration Certificate
Now we have automatically configured the certificate for us. We can see the form of configuration and configure it by ourselves in the future.
server {
server_name bbs.wzlinux.com; # managed by Certbot
root /usr/share/nginx/html;
# Load configuration files for the default server block.
include /etc/nginx/default.d/*.conf;
location / {
}
error_page 404 /404.html;
location = /40x.html {
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
}
listen [::]:443 ssl ipv6only=on; # managed by Certbot
listen 443 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/bbs.wzlinux.com/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/bbs.wzlinux.com/privkey.pem; # managed by Certbot
include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
}
server {
if ($host = bbs.wzlinux.com) {
return 301 https://$host$request_uri;
} # managed by Certbot
listen 80 ;
listen [::]:80 ;
server_name bbs.wzlinux.com;
return 404; # managed by Certbot
}3.4. Update Certificate
Now that you've done that, we can check the installation of the certificate.
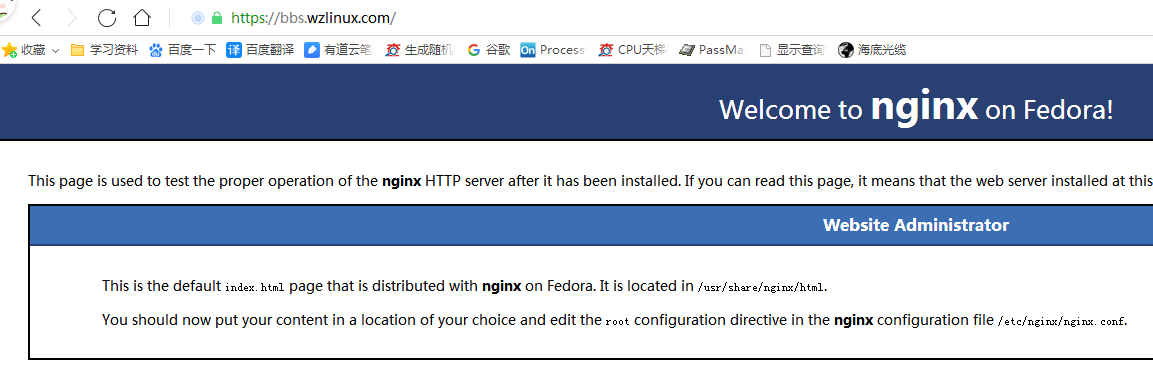

For security reasons, Let's Encrypt only issues certificates with a validity period of 90 days, so it's worth updating the security certificate every three months, although it's a little cumbersome, for network security.Fortunately, Certbot also provides a convenient update method.
We can test the certificate at www.ssllabs.com.
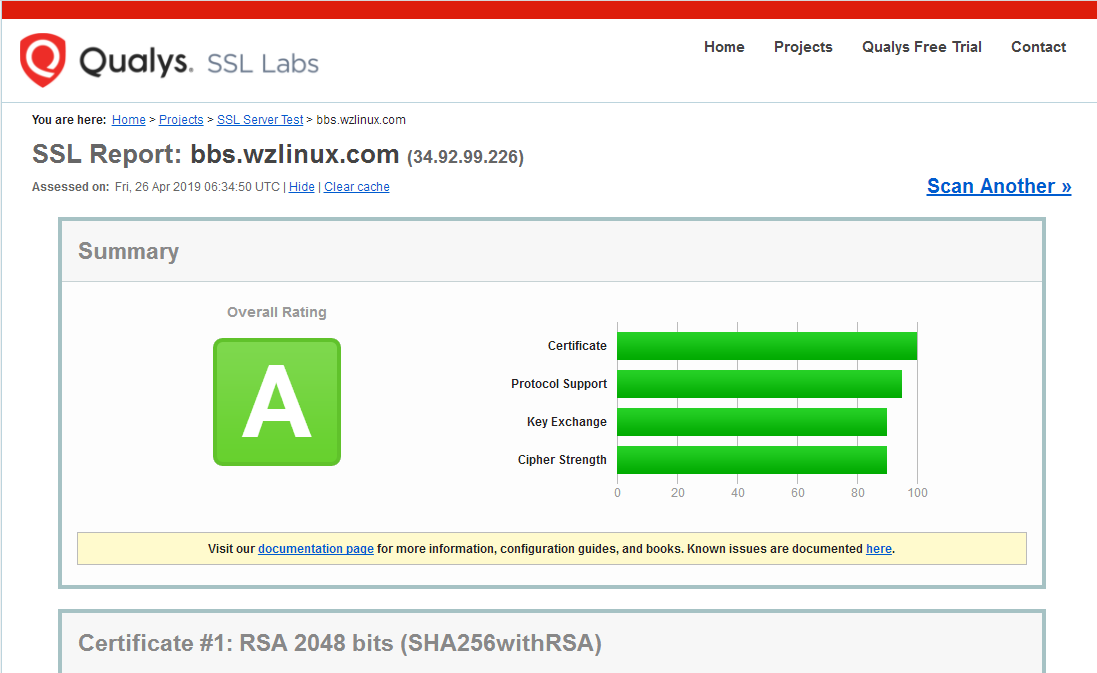
- Test the update. This step is not a real update, but a call to Certbot to test.
certbot renew --dry-run
It is recommended that you add a timer task on the server to allow the server to request updates regularly.
0 0,12 * * * python -c 'import random; import time; time.sleep(random.random() * 3600)' && certbot renew
Finally, I wish all of our sites will be upgraded to https, which everyone can afford.