A few days ago, my Aliyun server was violently cracked, very uncomfortable, so I made this key certificate password-free login.
First check whether sshd is installed in Aliyun's ECS server
Get the secret key: If you don't see the previous git upload github's article. Type:
[root@iz2ze8w7169ei61c5c1il5z ~]# vi /etc/ssh/sshd_config Modified to Password Authentication no At this point, set to yes, and then set to no after setting the client's secret key. [root@iz2ze8w7169ei61c5c1il5z ~]systemctl restart sshd.service You can't log in with xShell anymore.
[Server End, a server requiring remote connection)
[root@iz2ze8w7169ei61c5c1il5z ~]#ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
...
//Enter all the way, and the default generated secret key is under, / root/.ssh /.
[root@iz2ze8w7169ei61c5c1il5z .ssh]# pwd
/root/.ssh
[root@iz2ze8w7169ei61c5c1il5z .ssh]# ll
total 16
-rw------- 1 root root 789 Jun 20 11:23 authorized_keys
-rw------- 1 root root 1679 Jun 16 15:54 id_rsa
-rw-r--r-- 1 root root 399 Jun 16 15:54 id_rsa.pub
-rw-r--r-- 1 root root 1550 Jun 20 10:57 known_hosts
"Public and private keys"Principle of Authentication Method
1,First of all, in the client Create a pair of public and private keys.
//Public key file: ~/.ssh/id_rsa.pub
//Private key file: ~/.ssh/id_rsa
2,Then put the public key in server upper
~/.ssh/authorized_keys
3,client Sign in server process
client Keep the private key in use ssh Sign in server When, ssh Programs send private keys to sum server If the matching is successful, you can log in.
Now the preparation of the server is over, and the client configuration is done later.
Two operating system clients are prepared: Windows 10 client and Linux Centos 7 client.
W(Windows)
C(Centos)
First, C:
[root@ceshi ~]# ssh-keygen
All the way back, the. ssh folder will be generated under the ~directory.
[root@ceshi .ssh]# pwd
/root/.ssh
[root@ceshi .ssh]# ll
Total dosage 12
- RW - ----- 1 root 1671 June 20:53 id_rsa
- rw-r--r -- 1 root 392 June 20:53 id_rsa.pub
- rw-r--r -- 1 root 1585 June 20 11:07 known_hosts
[root@ceshi .ssh]# more id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAxs5W2gIw5paR+3cXmI8NsttblqeuFv8m3HLoZPMXQ7/ZTePJvCijdzUxn+bxXtthEVdcMgWid7ET86sZ5fPJ75KprJ/vIzOqOWmTTUgbNrqV2ytdPY8wkswwAmZlSiJdGQJgsJuGTtdxU6HN/k4PWVykD88NT+jklNsIViUvPzwEG4hYsMVDVONFDgD0pKgLyfr4uvOd7NZi
wVhyjPF42ATASj8efPCuwadGewp2nB5U+Q7eJOuvpvHfcTw55XM5rhpyNydE7QyXrOw8GOJFXCc1lFV/rJ/m9UO9fsIER9DOgy3uQdGL4M6E+NaM1kTfO/QwAkrGqmm5V0fgNhvPQeCu/w== root@ceshi
[root@ceshi .ssh]# ssh-copy-id -i /root/.ssh/id_rsa.pub root@YourRemoteIP
The ssh-copy-id operation is automatically saved in the / root/.ssh/authorized_keys file of the host.
[root@ceshi .ssh]# ssh root@YourRemoteIP
Successful connection without passwordThere are no big problems under Centos system, mainly Windows system has many problems.
The process of ssh-key verification is the same. The principle is to send the public key and then verify it.
However, in Windows, the generation of id_rsa.pub encounters the following problems:
①: 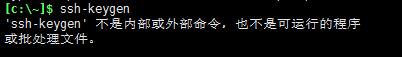
Solution: Download a git bash https://git-scm.com/download
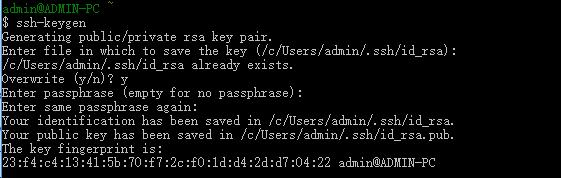
Because keys have been generated before, overwriting the rewritten key file is prompted. The first generation does not have this prompt.
②: 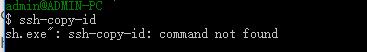
Solution: If you understand a little ssh password-free login process, you will know the point principle, use other operations to achieve the effect of scp-copy-id, anyway, the ultimate result is the same, whether he walked or drove to.
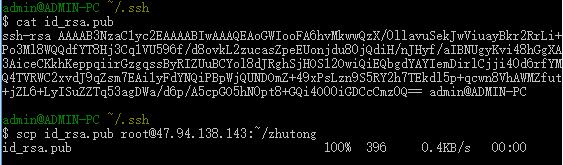
Then come to the Server side:
[root@iz2ze8w7169ei61c5c1il5z zhutong]# pwd
/root/zhutong
[root@iz2ze8w7169ei61c5c1il5z zhutong]# cat id_rsa.pub >> /root/.ssh/authorized_keys
[root@iz2ze8w7169ei61c5c1il5z zhutong]# more /root/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAxs5W2gIw5paR+3cXmI8NsttblqeuFv8m3HLoZPMXQ7/ZTePJvCijdzUxn+bxXtthEVcMgWi7ET86Z5fPJ75KprJ/vIzOqOWmTTUgbNrqV2ytdPY8wkswwAmZlSiJdGQJgsJuGTtdxU6HN/k4PWVykD88NT+jklNIViUvPzwEG4hYsMVDVONFDgD0pKgLyfr4uvOd7NZiwVhyjPF42ATASj8efPCuwadGewp2nB5U+Q
7eJOuvpvHfcTw55XM5rhpyNydE7QyXrOw8GOJFXCc1lFV/rJ/m9UO9fsIER9DOgy3uQsGL4M6E+NaM1kTfO/QwAkrGqmm5V0fgNhvPQeCu/w== root@ceshi
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAoGWIooFA6hvMkwwQzX/0llavuSekJwViuayBkr2RrLi+Po3Ml8WQQdfYT8Hj3Cq1VU596f/d8ovkL2zucasZpeEUonjdu80jQdiH/nJHyf/aIBNUgyKvi48hGgXA3AiceCKkhKeppqiirGzgqssByRIZUuBCYol8dJRghSjHOS12OwiQiEQbgdYAYIemDirlCjji40d6rfYMQ4TVRWC2xvdJ9qZsm7EAi1yFdYNQiP
BpWjQUNDOmZ+49xPsLzn9S5RY2h7TEkdl5p+qcwn8VhAWMZfut+jZL6+LyISuZZTq53agDWa/d6p/A5cpGO5hN0pt8+GQi4O00iGDCcCmz0Q== admin@ADMIN-PCW-End Connection Test:
Attention, attention, attention
Set the corresponding parameter in / etc/ssh/sshd_config to Password Authentication no before testing
Then restart the service.
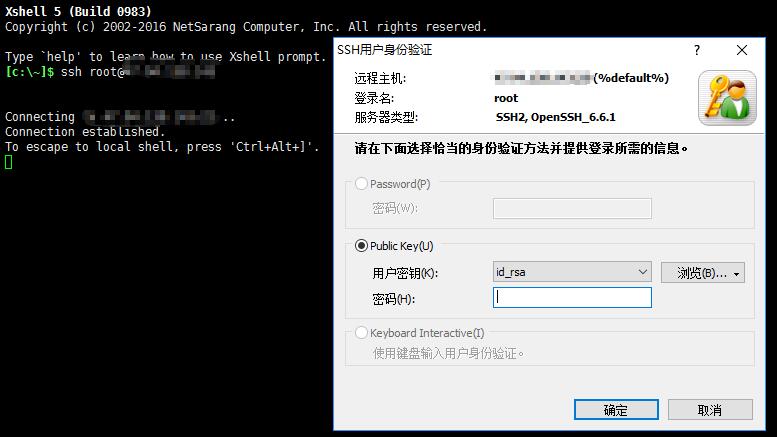
The W end finds that the place where the original password is entered is directly ashed by the xshell connection. It can only enter the public key. Then we choose the corresponding secret key:
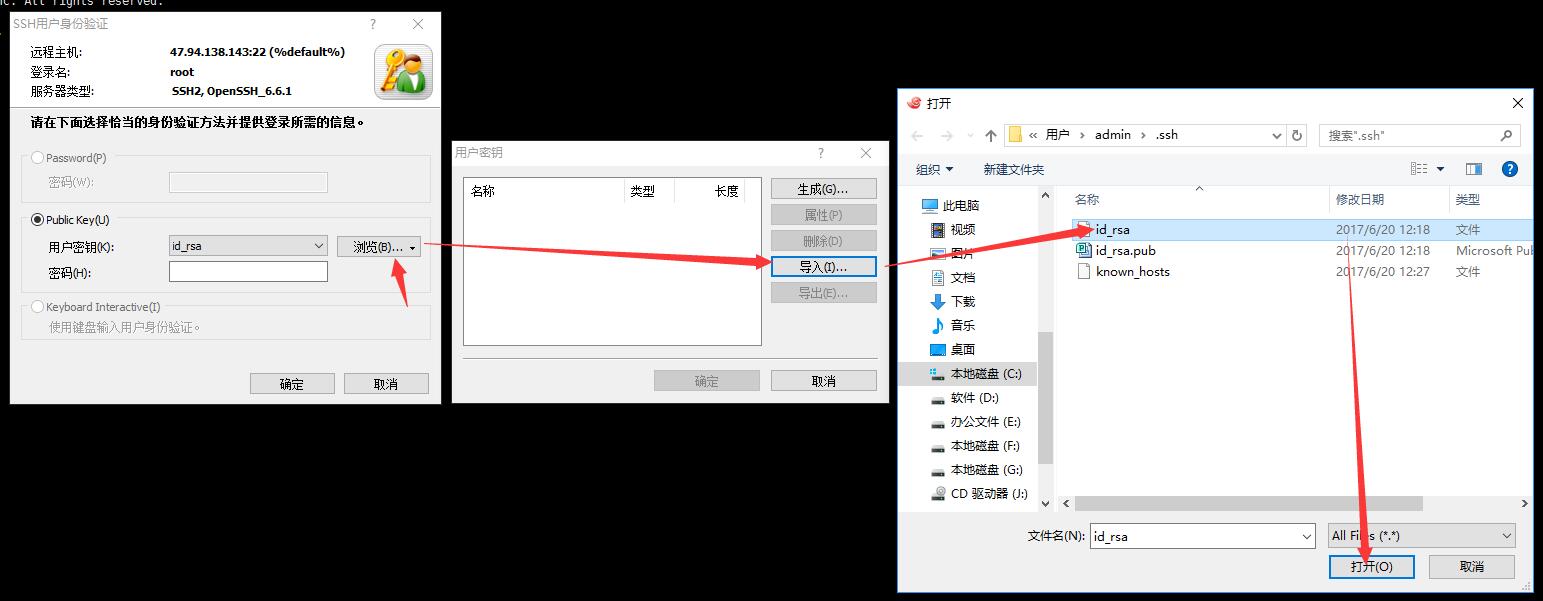
OK
Doing so effectively prevents hackers from violently cracking servers (but surely 0.0% higher than the previous security factor)