There are many games in perfect world. The more famous ones are Zhu Xian, world of Warcraft and so on. Perfect today, let's take a look at the reverse analysis of the landing of the perfect world!
JS reverse parsing
There is a click authentication when logging in. Never mind, perfect ignore it first and click directly. Perfect mainly discusses the reverse way of password.
After the packet capture login, we see that there is no login url in the XHR column of the tool, so we click all to view it. There is login in it.
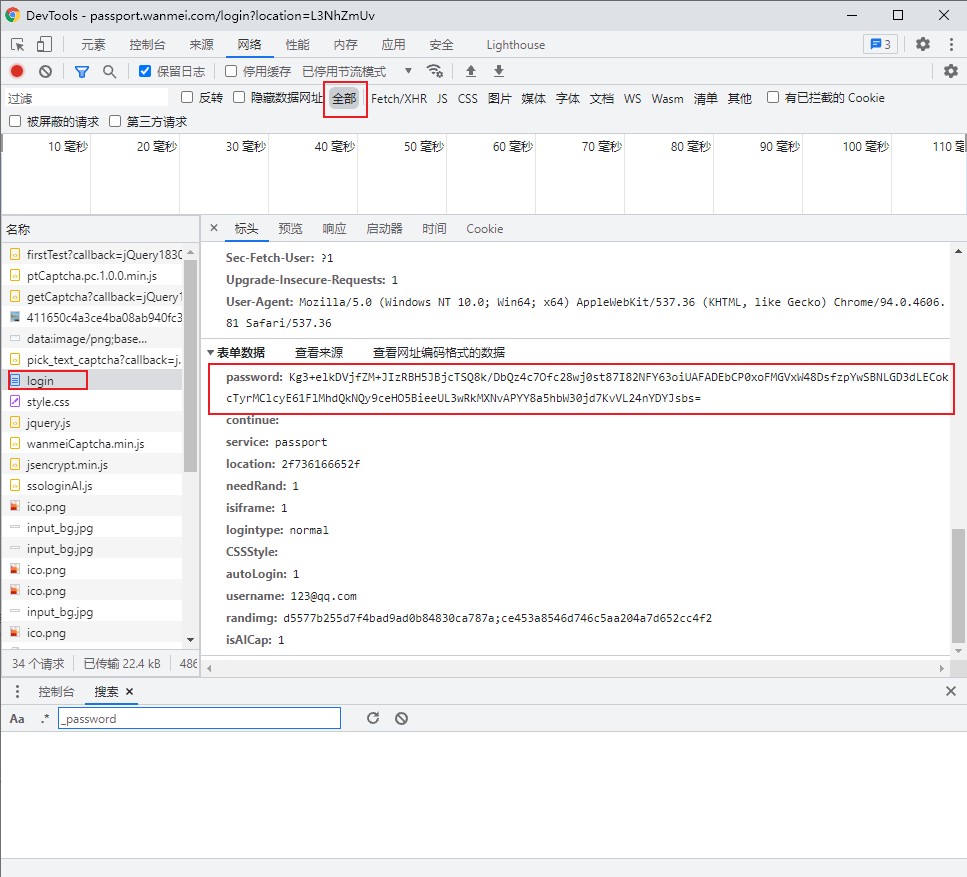
In the form data, we can see the password data, which is so long. The basic judgment is that it is an RSA encryption method:
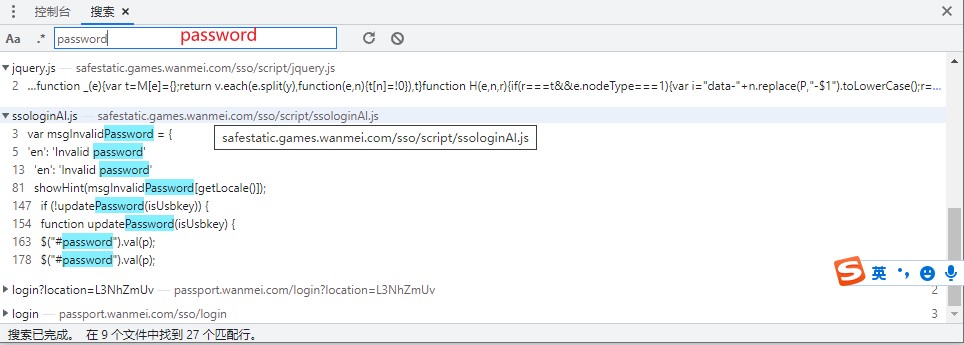
We searched the password and found that there are many JS that meet the conditions. After analysis, we judged that ssologinAI.js may be the data we want, and then we click in to have a look:
Search password and analyze each qualified code. We see a column of code with e.setPublicKey on it, which means public key in RSA. It's likely that this column is the data we're looking for. Hit the breakpoint and click login again. Sure enough, it was suspended here.
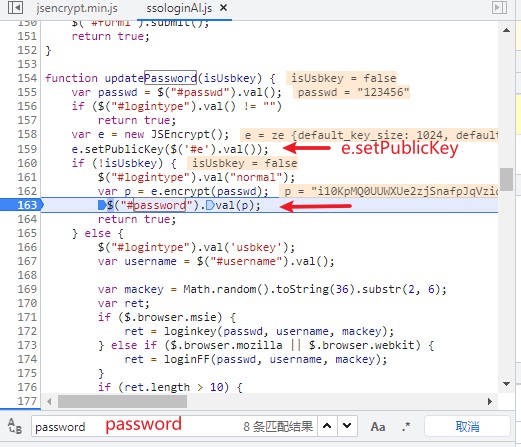
We click the above implementation method var p = e.encrypt(passwd);, Go in and have a look. The file name of this JS is called jsencrypt.min.js. You can copy the whole code to the analysis tool for rewriting
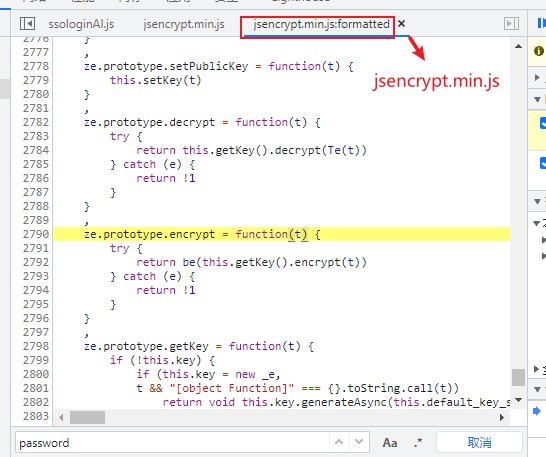
After copying, format – load the code.
We see that 'navigator' is undefined and 'window' is undefined. These two are obviously built-in objects of js, so we directly locate this. Then the load succeeds.
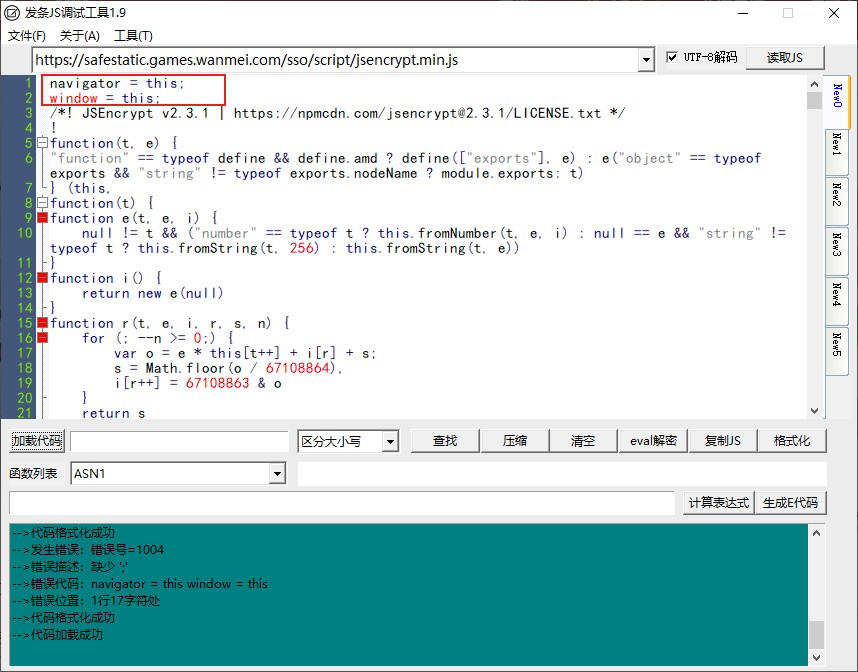
Now let's rewrite the code and add a function:
function getPwd(passwd){
var e = new JSEncrypt();
e.setPublicKey($('#e').val());
var p = e.encrypt(passwd);
return p
}
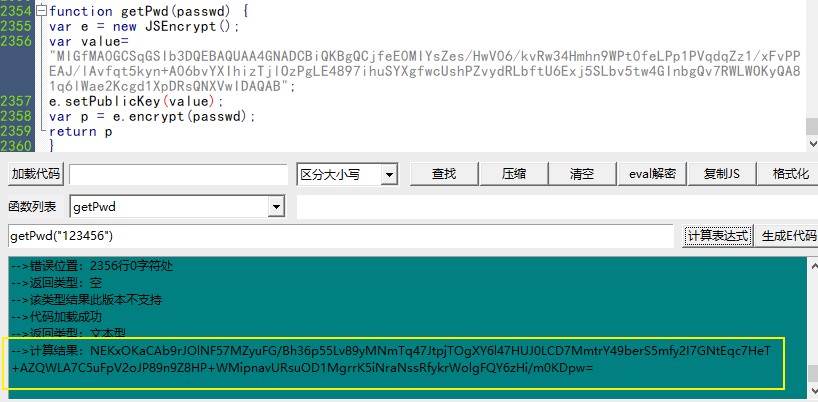
Then we calculate the getPwd("123456") and find that the prompt "this type result is not supported in this version".
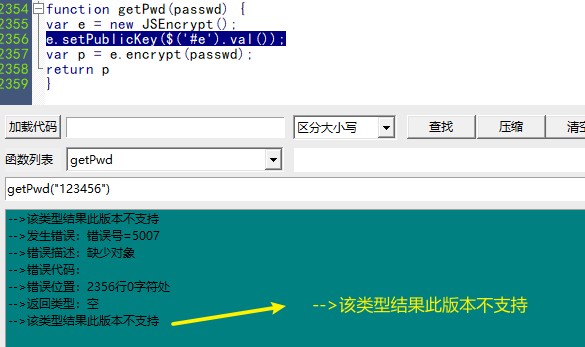
All the students at the front of the meeting know that #e means id="e", that is, the E is right in the web source code, so go to the web page to search for id="e". See the following values:
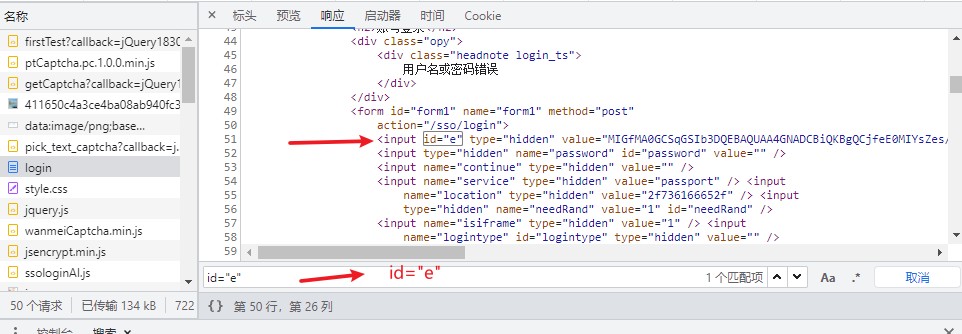
Then we will copy the value of this value and continue to rewrite it:
var e = new JSEncrypt(); var value="MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCjfeE0MIYsZes/HwV06/kvRw34Hmhn9WPt0feLPp1PVqdqZz1/xFvPPEAJ/lAvfqt5kyn+A06bvYXIhizTjlOzPgLE4897ihuSYXgfwcUshPZvydRLbftU6Exj5SLbv5tw4GInbgQv7RWLWOKyQA81q6lWae2Kcgd1XpDRsQNXVwIDAQAB"; e.setPublicKey(value); var p = e.encrypt(passwd); return p }
After calculation, we see the result!
So far, JS source code analysis is completed!
Python code implementation
Create the wanmei.js file, copy the above code and save it! Remember to change the key(value) of the public key to a parameter:
function getPwd(value, passwd) {
var e = new JSEncrypt();
e.setPublicKey(value);
var p = e.encrypt(passwd);
return p;
}
Get public key
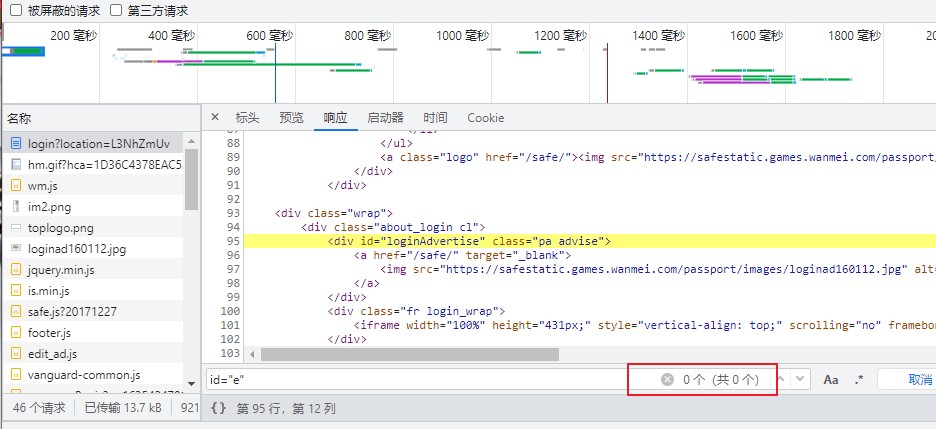
We directly grabbed the home page, and the search id="e" was not found. Here is a tip to share. Align the login box, right-click to view the "source code of the framework", delete view source:, and then capture the url in the framework source code:
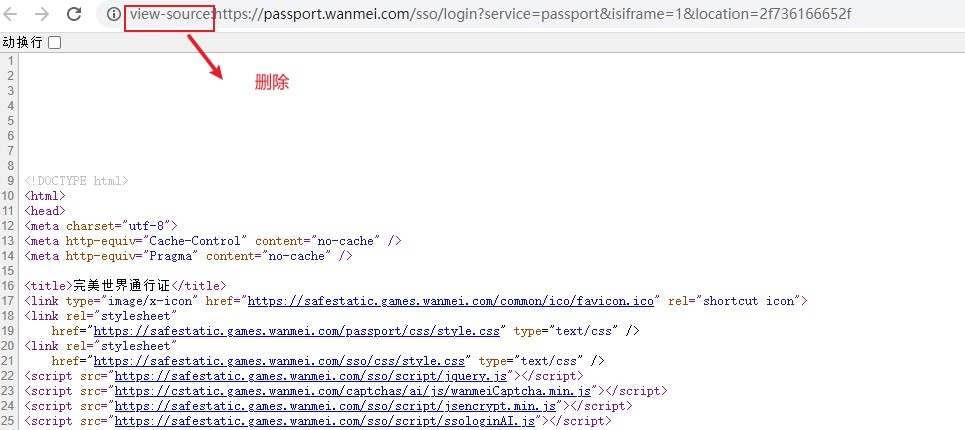
You can search for id="e". Then write python code:
import requests
from lxml import etree
import execjs
# Initiate a request to obtain the public key
url = 'https://passport.wanmei.com/sso/login?service=passport&isiframe=1&location=2f736166652f'
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.81 Safari/537.36'
}
page_text = requests.get(url=url, headers=headers).text
tree = etree.HTML(page_text)
key = tree.xpath('//input[@id="e"]/@value')[0]
print(key)
Encrypted reverse
# Encrypted reverse
node = execjs.get()
ctx = node.compile(open('./wanmei.js', encoding='utf-8').read())
fucnName = 'getPwd("{0}","{1}")'.format('123456', key)
pwd = ctx.eval(fucnName)
print(pwd)
In this way, the ciphertext is obtained!
Follow Python Taoge! Learn more about Python!
