Test file: https://lanzous.com/b07rlg5gd
Misc
Sign in
After answering the question and entering token, it is visible in the console.
flag{32c7c08cc310048a8605c5e2caba3e99}
crypto
boom
#include <iostream> using namespace std; int main() { long long a = 0; long long b = a * (a + 1); while (1) { if (b == 7943722218936282) break; a++; b = a * (a + 1); } cout << a << endl; system("PAUSE"); return 0; }
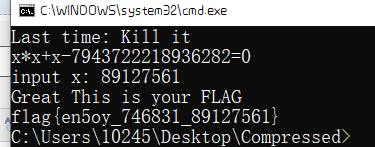
flag{en5oy_746831_89127561}
Reverse
bang
The free version of bang bang encryption mainly uses FART to shell classes.dex obtain
public void onClick(View paramAnonymousView) { String str = localEditText.getText().toString(); paramAnonymousView = paramBundle.getText().toString(); if (str.equals(paramAnonymousView)) { MainActivity.showmsg("user is equal passwd"); } else if ((str.equals("admin") & paramAnonymousView.equals("pass71487"))) { MainActivity.showmsg("success"); MainActivity.showmsg("flag is flag{borring_things}"); } else { MainActivity.showmsg("wrong"); } }
flag{borring_things}
joker
First remove the confusion in the code and adjust the stack balance.
wrong function, the odd and even subscripts of flag are XOR subscript and minus subscript respectively.
omg function, transformed flag and unk_4030C0 comparison.
model = [0x66, 0x6B, 0x63, 0x64, 0x7F, 0x61, 0x67, 0x64, 0x3B, 0x56, 0x6B, 0x61, 0x7B, 0x26, 0x3B, 0x50, 0x63, 0x5F, 0x4D, 0x5A, 0x71, 0x0C, 0x37, 0x66] flag = "" for i in range(len(model)): if(i % 2 == 0): flag += chr(model[i]^i) else: flag += chr(model[i] + i) print (flag)
Reverse solution, flag{fak3_alw35_sp_me!!}
Use dbg to debug to
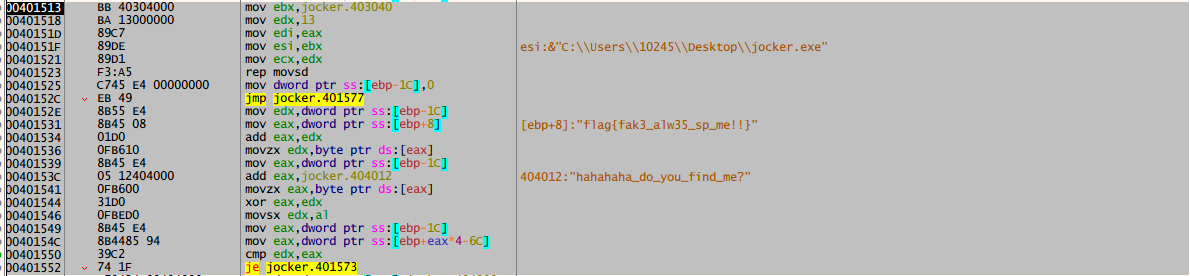
Here, flag{fak3_alw35_sp_me!!} and hahaha_ Do_ you_ find_ Exclusive or of the first 19 characters of me
[0x0E,0x0D,0x09,0x06,0x13,0x05,0x58,0x56,0x3E,0x06,0x0C,0x3C,0x1F,0x57,0x14,0x6B,0x57,0x59,0x0D,0x00]
Inverse solution
m = "hahahaha_do_you_find_me?" n = [0x0E,0x0D,0x09,0x06,0x13,0x05,0x58,0x56,0x3E,0x06,0x0C,0x3C,0x1F,0x57,0x14,0x6B,0x57,0x59,0x0D] for i in range(len(n)): print (chr(ord(m[i])^n[i]),end="")
flag{d07abccf8a410c, 5 characters are missing, the last bit is'} '
In the finally function, the five digit values are used

It can be seen that 0x3a must be '}', the relationship between guesses is XOR (71), and a complete flag is obtained.
flag{d07abccf8a410cb37a}
You can't blow up the last few bits of this question, because you can't go through the check flag when you bring it in, and finally guess it's XOR with a bit of brain hole.
signal
VM topic
First pass in an array of length 114 as the switch operand
a=[0x0A,0x04,0x10,0x08,0x03,0x05,0x01,0x04,0x20,0x08,0x05,0x03,0x01,0x03,0x02,0x08,0x0B,0x01,0x0C,0x08,0x04,0x04,0x01,0x05,0x03,0x08,0x03,0x21,0x01,0x0B,0x08,0x0B,0x01,0x04,0x09,0x08,0x03,0x20,0x01,0x02,0x51,0x08,0x04,0x24,0x01,0x0C,0x08,0x0B,0x01,0x05,0x02,0x08,0x02,0x25,0x01,0x02,0x36,0x08,0x04,0x41,0x01,0x02,0x20,0x08,0x05,0x01,0x01,0x05,0x03,0x08,0x02,0x25,0x01,0x04,0x09,0x08,0x03,0x20,0x01,0x02,0x41,0x08,0x0C,0x01,0x07,0x22,0x07,0x3F,0x07,0x34,0x07,0x32,0x07,0x72,0x07,0x33,0x7,0x18,0x7,0xffffffa7,0x7,0x31,0x7,0xffffff,0x7,0x28,0x7,0xffffff84,0x7,0xffffffc1,0x7,0x1e,0x7,0x7a]
Dynamic debugging found that in case 7, v4[v8] is the fixed value, record the value of eax (change je to jmp)

v4 = [0x22,0x3F,0x34,0x32,0x72,0x33,0x18,0xFA7,0x31,0xF1,0x28,0xF84,0xC1,0x1E,0x7A]
The a table is actually the option directory for executing switch. The v3 array is our flag. Each time case 1 is executed, it assigns a value to v4 (v4 is known). Therefore, each time to 1, it is a processing, such as 4, 16, 8, 3, 5, 1. Manual processing, we can write the script to get the flag
# -*- coding:utf-8 -*- flag = [0]*15 flag[0] = (0x22+5)^0x10 flag[1] = (0x3f//3)^0x20 flag[2] = 0x34+1+2 flag[3] = (0x32^4)-1 flag[4] = (0x72+0x21)//3 flag[5] = 0x33 + 2 flag[6] = (0x18+0x20)^0x9 flag[7] = (0xa7^0x24)-0x51 flag[8] = 0x31+1-1 flag[9] = (0xf1-0x25)//2 flag[10] = (0x28^0x41)-0x20 flag[11] = 0x84-0x20 flag[12] = (0xc1-0x25)//3 flag[13] = (0x1e+0x20)^0x9 flag[14] = 0x7a-0x1-0x41 print ('flag{'+''.join([chr(x) for x in flag])+'}')
flag{757515121fId478}